Suricata stands out in the world of network security. As a powerful open-source Network Intrusion Detection System (NIDS), Intrusion Prevention System (IPS), and Network Security Monitoring (NSM) engine, Suricata is widely trusted to spot and stop cyber threats coursing through your network. But in early 2024, security researchers uncovered a serious flaw—CVE-2024-24568—that left HTTP/2 traffic wide open for crafty attackers.
In this article, I’ll explain in simple terms how this bug worked, why it was dangerous, walk you through a proof-of-concept, and—crucially—tell you how to make sure your Suricata installs are safe.
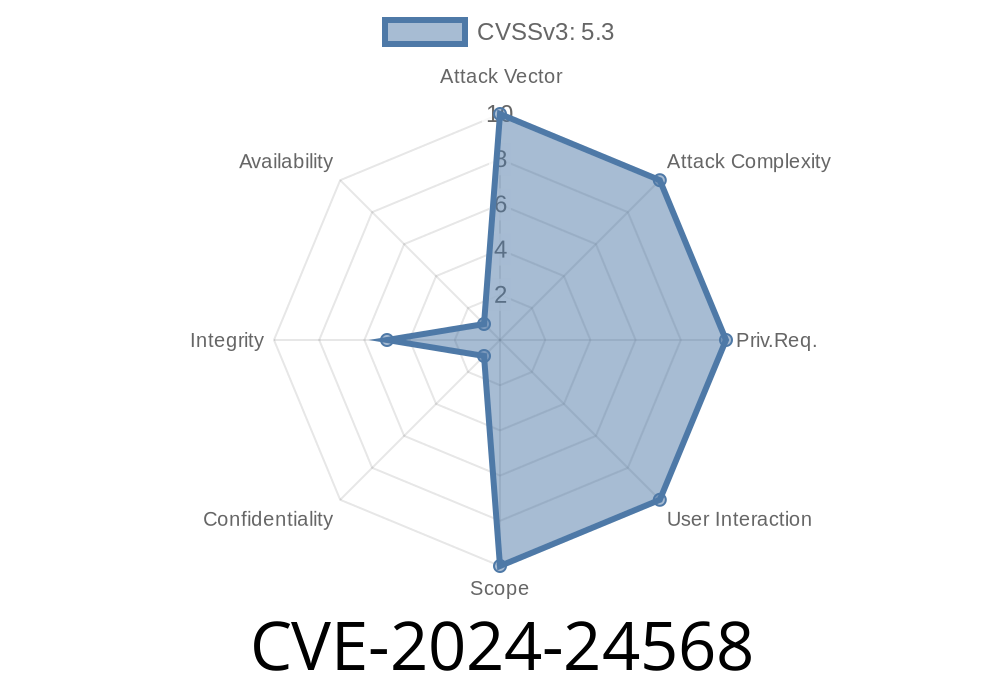
What is CVE-2024-24568?
To put it simply, before Suricata version 7..3, certain crafted HTTP/2 traffic could slip past Suricata’s detection rules that are supposed to inspect HTTP headers. The engine would miss or misinterpret these headers, allowing attackers to smuggle threats under the radar.
Technical Summary
- Component: Suricata NIDS/IPS
Affected Versions: All prior to 7..3
- Impact: Attackers could bypass detection for malicious or unwanted HTTP/2 headers
Why Was This a Big Deal?
Suricata rules can, for example, alert you if malware is being delivered using specific HTTP headers or if an attacker is trying to exfiltrate data using those headers. With this bug, attackers could manipulate the HTTP/2 protocol so Suricata wouldn’t see or match the traffic against these rules!
This is especially concerning for environments that heavily use HTTP/2—a standard now in common use for speed and security on the web.
Step by Step: How the Bypass Works
HTTP/2 is more complex than HTTP/1.1. Instead of headers being simple text, they use special frames and binary encodings. The bug in Suricata meant that with some clever formatting, the engine’s parser failed to properly assemble and check the headers.
A Simplified Exploit Example
Let’s say you have a Suricata rule to catch a suspicious header (e.g., X-Evil: true) in HTTP/2 traffic:
alert http any any -> any any (msg:"Evil header detected"; http.header; content:"X-Evil: true"; sid:999999;)
With the CVE-2024-24568 vulnerability, an attacker could split or encode headers in an unexpected way, and Suricata would not process them correctly. For example, using an attack proxy or custom script:
import h2.connection
import h2.events
from socket import create_connection
def send_crafted_http2_headers():
conn = create_connection(("target-server", 443))
conn = ssl.wrap_socket(conn, server_hostname="target-server")
h2_conn = h2.connection.H2Connection()
h2_conn.initiate_connection()
conn.sendall(h2_conn.data_to_send())
# Craft header block with edge-case formatting
headers = [
(':method', 'GET'),
(':path', '/secret'),
(':scheme', 'https'),
(':authority', 'target-server'),
# Split or encode this header in a non-standard way
('x-evil', 'true'),
]
h2_conn.send_headers(1, headers)
conn.sendall(h2_conn.data_to_send())
# ...
conn.close()
By sending HTTP/2 headers that are split or encoded “weirdly” (perhaps with pseudo-headers, extra whitespace, or odd segmentation), Suricata doesn’t match them against the detection rule—but the application server does see and process them.
References & Further Reading
- CVE Record: CVE-2024-24568
- Suricata Security Advisory
- Suricata 7..3 Changelog
Fixing the Vulnerability
Update Suricata to at least version 7..3!
All older versions are at risk and can’t reliably inspect HTTP/2 headers.
sudo apt update
sudo apt install suricata
Or, if using a source install
wget https://www.openinfosecfoundation.org/download/suricata-7..3.tar.gz
tar xvf suricata-7..3.tar.gz
cd suricata-7..3
./configure && make && sudo make install
Don’t forget to restart your Suricata service
sudo systemctl restart suricata
Consider using Suricata’s latest rulesets, as newer rules often detect post-exploit behavior.
- If HTTP/2 is not needed, you can block it at your network perimeter until all tools correctly parse it.
- Monitor your Suricata logs for unexpected traffic and missed matches, especially involving HTTP/2.
What to Watch For Going Forward
HTTP/2 support is tricky for security tools—so always run the latest versions. Attackers are eager to find bypasses in the parsing logic of IDS/IPS software.
Don’t get caught off-guard. Patch now, and watch those HTTP/2 headers like a hawk!
*Want more details or have questions about Suricata, detection rules, or network security? Drop your queries below and let’s dig in together.*
Timeline
Published on: 02/26/2024 16:27:58 UTC
Last modified on: 02/26/2024 16:32:25 UTC