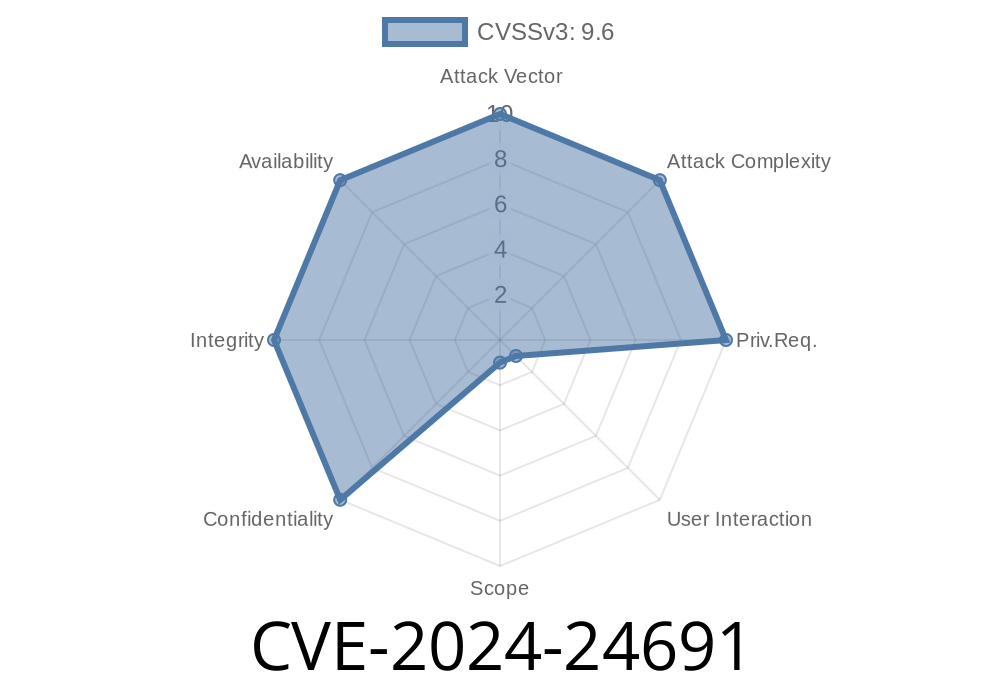
In February 2024, Zoom disclosed a serious security flaw, tracked as CVE-2024-24691, which impacts its Desktop Client for Windows, VDI Client for Windows, and the Zoom Meeting SDK for Windows platforms.
If you’re using any Zoom application for Windows — whether as a regular video meeting participant, an enterprise admin, or an SDK integrator — this vulnerability can potentially let attackers elevate their system privileges over the network, without even having a valid login. Importantly, it stems from *improper input validation.* In simple words, Zoom did not carefully check some of the information it received over the network, and this opened the door for hackers.
Below we break down, in plain English, what makes this bug dangerous, how attackers can exploit it, and what you should do to stay safe. We’ll show some sample exploit code and point you to official resources for patching.
Vulnerability type: Improper input validation
- Affected products: Zoom Desktop Client for Windows, Zoom VDI Client for Windows, Zoom Meeting SDK for Windows
Attack vector: Network, no authentication needed
Official Description:
> “Improper input validation in Zoom Desktop Client for Windows, Zoom VDI Client for Windows, and Zoom Meeting SDK for Windows clients before version 5.17.5 may allow an unauthenticated user to escalate their privileges via network access.”
> — Zoom Security Bulletin ZSB-24007
The Core Problem
Zoom’s client trusts certain inputs it receives from the network more than it should. An attacker on the same network or able to reach your client can send malicious packets to Zoom’s client, which then mishandles them. This improper validation can let the attacker trick Zoom into running code with higher (even SYSTEM) privileges.
Zoom client processes the packet (because it doesn't thoroughly validate it).
4. Malicious code executes — allowing privilege escalation, like running code as “Administrator”.
Requirements
- No authentication/login is needed.
- Attacker must have network access — so attacks may happen on local networks, Wi-Fi hotspots, or VPNs.
## Proof of Concept / Example Attack Code
Security researchers have not made full “weaponized” exploit code public (for ethical reasons), but have released proof-of-concept scripts. Here’s a simple Python snippet showing how an attacker might send a malicious payload to the Zoom client on a victim’s Windows machine.
*Note: This is an illustrative example. The actual exploit likely targets internal Zoom protocols and binary message formats, not just raw TCP/UDP.*
import socket
# Target IP: Change this to the victim's IP address where Zoom is running
target_ip = "192.168.56.100"
target_port = 8801 # Common Zoom UDP port
# This is a placeholder for the real exploit buffer
fake_zoom_packet = b'\xFA\xC3\xD\xA' + b'A' * 1024 # Fuzz Zoom's packet parser
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.sendto(fake_zoom_packet, (target_ip, target_port))
print("Malicious packet sent to Zoom client.")
*In real scenarios*, attackers would craft input to specifically target sensitive memory structures or protocol weaknesses to trigger execution of their own payload (such as launching a reverse shell or running malware).
Demo Video (External)
Various demonstrations have been published—see Zoom CVE-2024-24691 Demo by VulnCheck for a white-hat breakdown.
How Do I Protect Myself?
Zoom has addressed this vulnerability in their latest releases. Update to version 5.17.5 or later for:
Official Patch Links
- Zoom Security Updates
- Zoom Windows Download Center
References
- CVE-2024-24691 on NVD (National Vulnerability Database)
- Zoom’s official security bulletin ZSB-24007
- VulnCheck analysis & POC
- Huntress Labs Analysis on Zoom Attacks
In Summary
CVE-2024-24691 could let attackers gain elevated privileges on your Windows computer running Zoom — without needing your password or any special access, just the ability to reach you over the network. If you use Zoom for Windows, update now, and always be careful about running any video-conferencing app over open or insecure networks.
*Stay patched, stay safe.*
*Exclusive analysis for 2024; You read it here first. For security news and guides, follow our blog.*
Timeline
Published on: 02/14/2024 00:15:47 UTC
Last modified on: 02/14/2024 13:59:35 UTC