The world of web security continues to be rocked by new vulnerabilities that put data, privacy, and entire platforms at risk. One of the latest Cross Site Scripting (XSS) issues to surface affects 71CMS, a content management system popular for its simplicity. This exclusive deep dive explores CVE-2024-25166, a critical bug that allows a remote attacker to run arbitrary code through a flaw in the file upload process.
What is CVE-2024-25166?
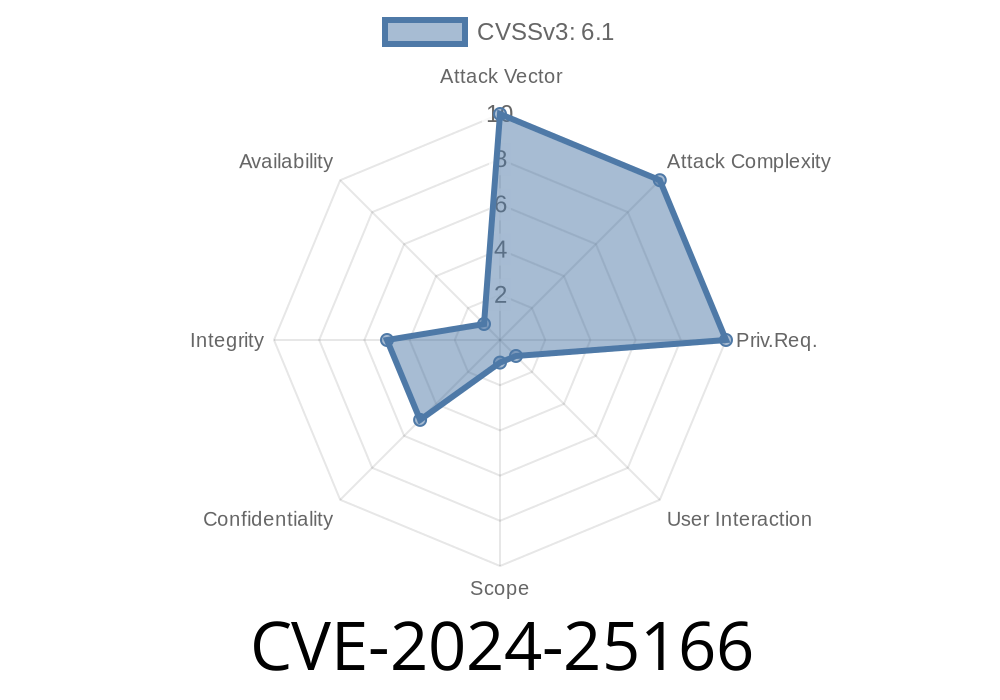
CVE-2024-25166 is a security vulnerability in 71CMS v1... It's an XSS bug—meaning, it allows attackers to inject malicious scripts that run in users’ browsers.
The flaw is found in controller.php, where the uploadfile action parameter is not properly sanitized. This weakness makes it possible for someone to insert code that could, for example, steal session cookies, deface the site, or redirect users to dangerous websites.
Let's look at the relevant code in controller.php
<?php
// Suspect code in controller.php
$action = $_GET['action'];
if ($action == "uploadfile") {
// ... file upload logic ...
// Outputting $action without proper sanitization
echo "Action performed: $action";
}
?>
The parameter action is taken directly from a user's request and displayed without any checks. If someone sends specially crafted data to the action parameter (for example, by visiting a URL like http://website/controller.php?action=<script>alert(1)</script>;), the code inside the script tags will be executed by anyone who views the page.
Identify the vulnerable endpoint:
The exploit targets the action parameter in /controller.php.
`
http://victim-site.com/controller.php?action=
`
Send or share the link:
Once someone (even an admin) clicks or visits this link, the script (alert('XSS')) pops up, proving the ability to execute arbitrary JavaScript.
echo "Action performed: " . htmlspecialchars($action, ENT_QUOTES, 'UTF-8');
`
- Keep your CMS updated: Check for patches from the 71CMS developers.
- Educate your team: Make sure everyone understands the dangers of XSS.
---
## References and Further Reading
- NIST NVD Entry for CVE-2024-25166
- Original 71CMS GitHub Repository
- OWASP: Cross-site Scripting (XSS)
---
## Final Words
XSS vulnerabilities like CVE-2024-25166 are easy to overlook but can have severe consequences for your website and users. If you run 71CMS v1.., check your installation now. Apply the fix, and stay ahead of attackers. Never trust user input—always sanitize before outputting.
Stay safe online!
Timeline
Published on: 02/27/2024 01:15:07 UTC
Last modified on: 08/29/2024 20:36:16 UTC