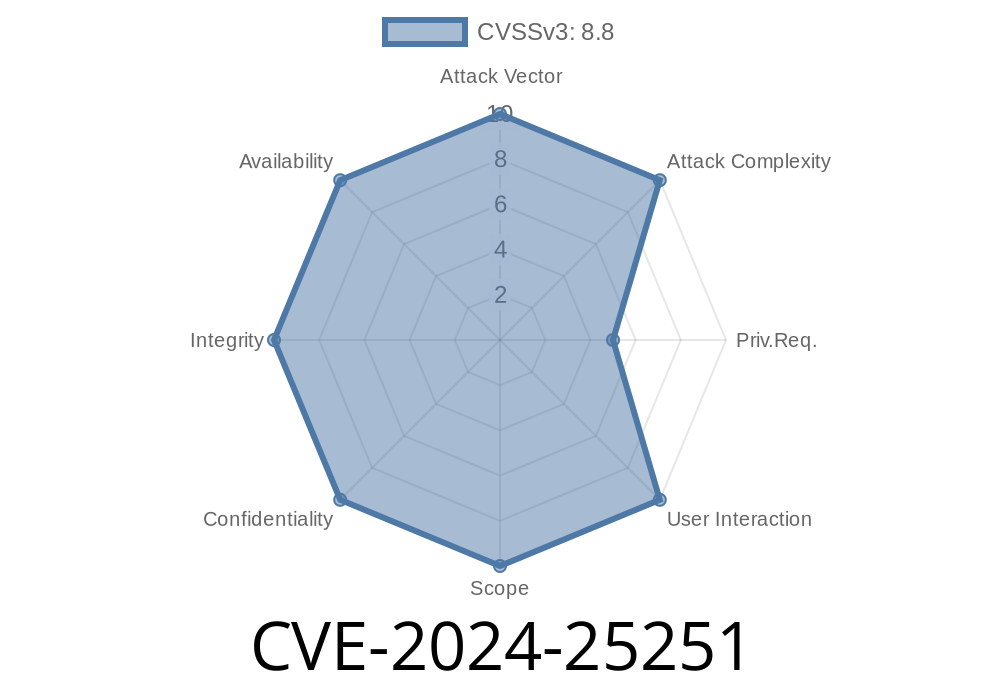
In 2024, the vulnerability CVE-2024-25251 was assigned to the open-source Agro-School Management System 1.. This issue exposes sensitive areas of the system because of Incorrect Access Control. In simple terms, users can get into restricted parts of the application without the right permission checks.
Many schools and agricultural training centers use this system for managing students, teachers, attendance, and more. A flaw here can lead to leaks of personal data, unauthorized changes, or even system compromise.
In this article, we break down the vulnerability in plain words, show you how it happens, include code snippets for reference, and provide links so you can dig deeper. If you run this project, read on — you might be at risk.
What Is Incorrect Access Control?
In software, Access Control means making sure that only authorized users can do certain things. If this fails — say, anyone can act as an administrator or see private student records — that's called Incorrect Access Control.
With Agro-School Management System 1., certain pages and actions don't properly check who you are. That means a regular user, or even someone not logged in, can stumble into admin functions.
Looking at the code and user reports, the root cause is
- Lack of session/user permission checks on critical pages.
For example, the system relies on session variables like $_SESSION['user_id'], but sometimes forgets to check them. Attackers can access URLs directly (without logging in), and the system happily serves them admin pages.
Exploit Details and Code Demo
Here’s how an attacker might exploit CVE-2024-25251.
Suppose your system has an admin-only page at
http://example.com/agro-school/admin/dashboard.php
In the code, you might see something like
// dashboard.php
// This is supposed to be the access control
include('../config.php');
if(!isset($_SESSION['user_id'])){
header('Location: ../login.php');
exit();
}
// ...dashboard content...
But in some of the included files or other critical areas, this check is absent
// student-list.php
include('../config.php');
// MISSING: if(!isset($_SESSION['user_id'])){ ... }
// ... code to list all students ...
while($row = mysqli_fetch_assoc($result)){
echo $row['name'] . " - " . $row['contact'] . "
";
}
As a result, anyone who knows the URL can access student-list.php and get a list of all students — no login or privilege check required.
`
http://your-server/agro-school/admin/student-list.php
`
Data Exposure:
You’ll see a full list of students, their contacts, maybe even their addresses and parents’ names.
Escalating the Attack:
Test other pages (teacher-list.php, grades.php, settings.php). Many might also lack proper checks.
A correct protection should be at the top of every sensitive PHP script
session_start();
if (!isset($_SESSION['user_id']) || $_SESSION['role'] != 'admin') {
header('Location: ../login.php');
exit();
}
More Technical Details
- Affected Version: Agro-School Management System 1. (https://www.code-projects.org/agro-school-management-system-in-php-with-source-code/)
Attackers can
- View or edit student/teacher records without authentication
- Access admin functions (like adding/deleting records)
References
- Original CVE-2024-25251 entry (NVD)
- Code-Projects source page
- Common Weakness Enumeration: Insufficient Access Control (CWE-284)
- OWASP Top 10: Broken Access Control
Conclusion
CVE-2024-25251 is both simple and serious. If your application doesn't check who you are before showing sensitive data, anyone can walk right in. Don't just rely on hidden links or security through obscurity — use real code checks like session_start() and *always* confirm a user's role.
Are you running Agro-School Management System? Check your access controls today!
Stay safe. Always verify access!
*(This post is for educational purposes only. Do not use this information for unauthorized or illegal activity. Always notify and work with vendors and administrators for responsible disclosure.)*
Timeline
Published on: 02/22/2024 01:15:08 UTC
Last modified on: 08/16/2024 18:35:06 UTC