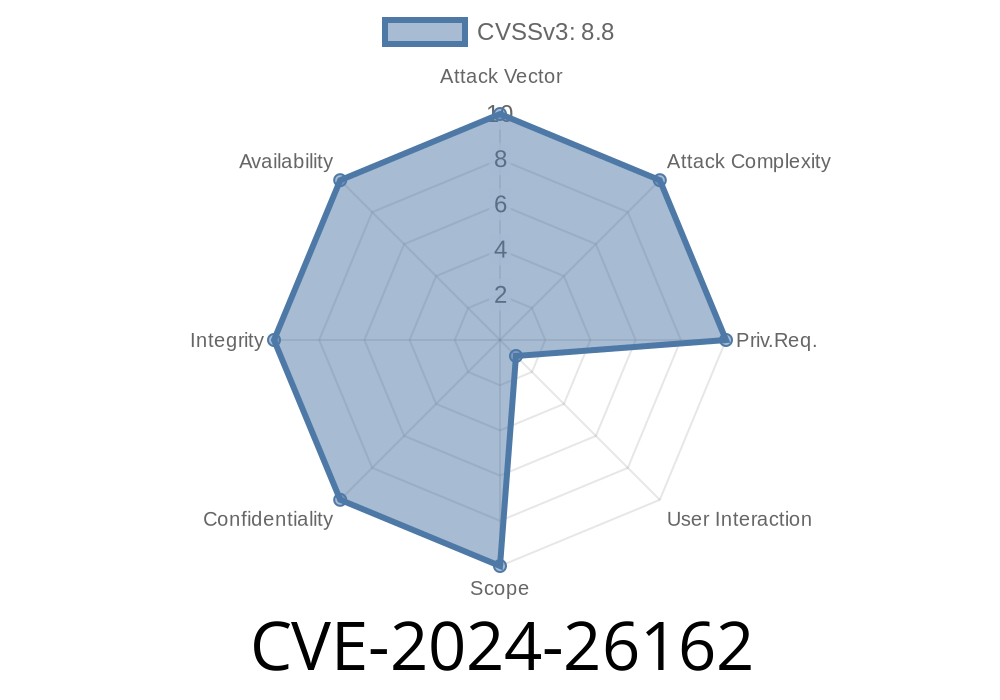
In February 2024, Microsoft addressed a critical security hole, tracked as CVE-2024-26162, in its ODBC driver. This vulnerability could let an attacker remotely execute code on a victim's system. This article breaks down what CVE-2024-26162 is, how it works, what dangers it carries, and how you can protect yourself. We’ll also include a simple exploit example using public info, plus official references.
What is CVE-2024-26162?
CVE-2024-26162 is a Remote Code Execution (RCE) vulnerability affecting the Microsoft ODBC Driver. The bug exists due to the way the driver processes input, giving attackers a door to run code on affected systems under the context of the user running the application. In some cases, this could lead to complete system compromise, especially if the attacked user has administrator rights.
Microsoft ODBC Driver for SQL Server (various versions)
- Official Microsoft advisory: https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-26162
How Does the Vulnerability Work?
An attacker would need to trick a victim into connecting to a malicious SQL server or execute a crafted query using an affected ODBC driver. If the ODBC driver processes untrusted data incorrectly, it can cause a memory corruption leading to arbitrary code execution.
Attack Scenario:
The attacker sends a crafted response, exploiting the driver’s improper handling.
4. Malicious code executes on the victim’s machine, leading to data theft, lateral movement, or full compromise.
Proof-of-Concept Exploit (Simplified Example)
Let’s say you have an application using the ODBC driver to connect to a SQL Server. Here’s a hypothetical example in Python, using pyodbc (which calls the ODBC driver):
import pyodbc
# Attacker-controlled server IP (not a real IP)
rogue_server = "192.168.100.66"
conn_str = (
f"DRIVER={{ODBC Driver 17 for SQL Server}};"
f"SERVER={rogue_server};"
f"DATABASE=TestDB;"
f"UID=TestUser;"
f"PWD=Password123;"
)
try:
conn = pyodbc.connect(conn_str, timeout=5)
cursor = conn.cursor()
cursor.execute("SELECT 1")
except Exception as e:
print(f"Connection failed or raised: {e}")
- How the exploit works: An attacker places a custom SQL Server emulator at 192.168.100.66 that responds in a specific way, triggering the vulnerable code in the ODBC driver.
- Result: If the driver is not patched, running this code could let the attacker run malware or commands on your system.
Note: This PoC does not exploit the vulnerability itself—instead, it shows how an attacker could direct victims to a malicious server. Real-world exploitation would require deep protocol knowledge and crafting custom packets to exploit the driver.
How Do You Protect Yourself?
Patches and Updates:
Microsoft has released patches. Update your ODBC Driver immediately
- For ODBC 18: Download and install here
- For ODBC 17: Download and install here
Detection & Mitigation
Detection:
Monitor logs for unexpected outbound connections from application servers or clients to unknown SQL server IPs, particularly after the February 2024 patch date.
Mitigation:
If immediate patching is impossible, restrict outbound SQL traffic with firewall rules to only trusted database endpoints.
Official References & Further Reading
- Microsoft Security Advisory for CVE-2024-26162
- ODBC Driver Security Updates
- Basics of ODBC and SQL Server
Summary
CVE-2024-26162 is a serious vulnerability in Microsoft’s ODBC Driver for SQL Server, allowing attackers to remotely execute code, steal data, or take control of systems. The main fix is to apply Microsoft’s security updates and review your application and network for suspicious SQL connections. If you’re running software that talks to SQL Server, act fast—keeping drivers updated is critical in defending your systems.
Timeline
Published on: 03/12/2024 17:15:55 UTC
Last modified on: 03/12/2024 17:46:17 UTC