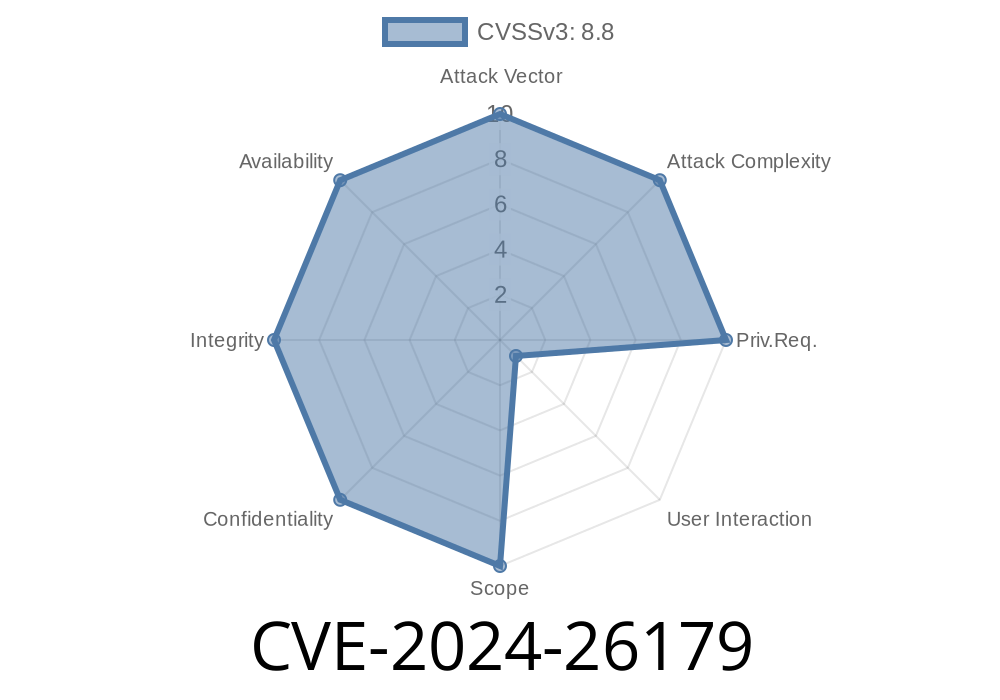
The March 2024 Patch Tuesday dropped a bombshell for IT folks everywhere: CVE-2024-26179. This vulnerability affects the Windows Routing and Remote Access Service (RRAS)—a core Windows feature for many organizations. If exploited, it could let hackers run their own code on your machine. In this article, we break down what this vulnerability is, how an attack might happen, and what you can do right now.
What is RRAS and Why Should You Care?
Windows RRAS is a service that lets administrators route network traffic and provide VPN access right from a Windows server. It powers remote connections for businesses of all sizes.
But great power comes with great responsibility. If RRAS gets compromised, an attacker could pivot anywhere on your network.
In plain English
A specially crafted network packet, sent to a Windows server running RRAS, can trick the service into running code supplied by an attacker. No username or password needed. Just network access to RRAS.
The Patch (March 12, 2024)
Microsoft released details here:
🔗 Microsoft Security Update Guide: CVE-2024-26179
TL;DR:
If you’re running RRAS, patch immediately! The vulnerability is likely to be exploited now that details are public.
Exploit Details (How Could This Work?)
RRAS listens on your network for connection requests (VPN, NAT, routing). There’s a bug in how it handles certain packets. An attacker can exploit this by:
Sending specially crafted packets (malformed data) to the RRAS service.
3. Those packets trigger a memory corruption bug—allowing the attacker’s code to run on your server, with SYSTEM rights.
Simple Proof of Concept Outline
*(No weaponized exploit, just for educational/research context.)*
A common attack vector is the PPTP VPN protocol. Here’s a basic idea using Python and Scapy to send unexpected data to port 1723 (PPTP) of the target server.
# Proof-of-Concept: RRAS Invalid Packet to Port 1723
from scapy.all import *
target_ip = "192.168.1.100"
target_port = 1723 # PPTP port
# Create a packet with abnormal length/content
payload = b"A" * 4096 # Oversize payload, may trigger bug
packet = IP(dst=target_ip)/TCP(dport=target_port, flags="S")/Raw(load=payload)
# Send the packet
send(packet)
Note: The actual exploit involves discovering the exact way the service mishandles memory or input—it’s not public at the time of writing and is probably more complex. But the principle stays: attacker abuses RRAS parsing.
How to Detect
- Monitor for unusual connections to RRAS ports (PPTP: 1723, L2TP/IPsec: 1701/500/450)
Check Windows Event Logs for RRAS crashes or unexpected behavior
- Use tools like Sysmon to watch for suspicious network activity
Block exposure:
Don’t expose RRAS to the public internet if not absolutely needed. Firewall it off from untrusted networks.
More Information
- Microsoft Advisory
- Patch Tuesday (March 2024) Highlight
- NIST NVD Page
Final Thoughts
CVE-2024-26179 is a stark reminder: legacy services like RRAS are juicy targets. Keep your Windows systems updated, restrict unnecessary services, and watch your network doors.
If you’re running RRAS, patch it now before someone else does it for you!
Timeline
Published on: 04/09/2024 17:15:36 UTC
Last modified on: 04/10/2024 13:24:00 UTC