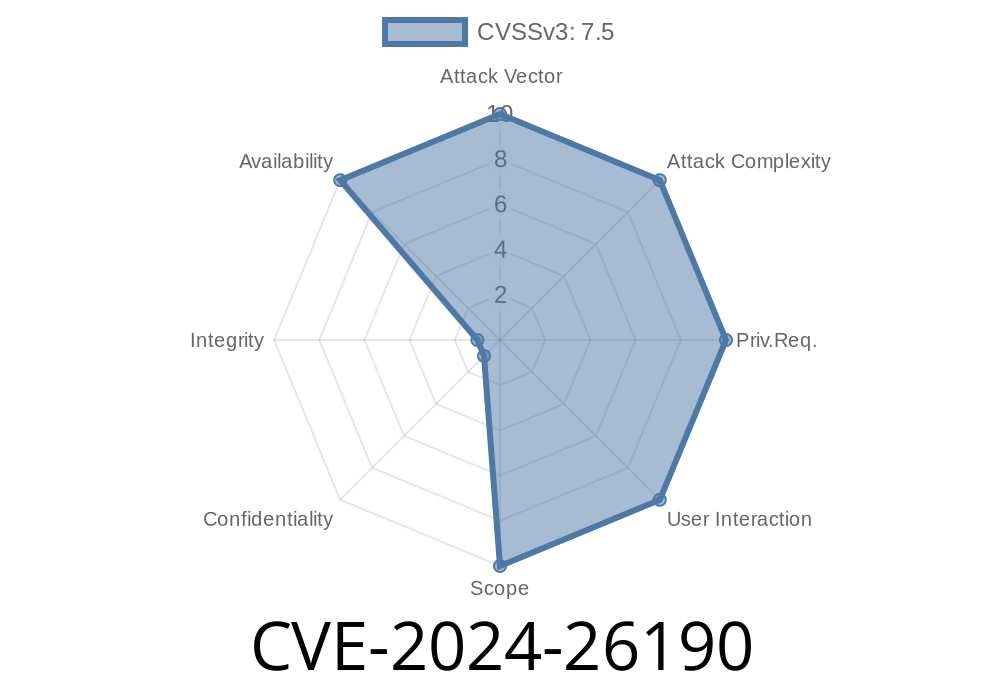
In February 2024, Microsoft patched a security flaw under the identifier CVE-2024-26190. This vulnerability targets the QUIC protocol implementation in Windows, potentially allowing attackers to crash impacted systems through specially crafted network traffic. Let’s break down what this vulnerability is, how it works, show you a code snippet to understand the concept, and wrap up with links and mitigation techniques.
What is QUIC?
QUIC (Quick UDP Internet Connections) is a relatively new transport protocol designed by Google and now standardized by the IETF. It speeds up web connections by using UDP (not TCP) and improves reliability and encryption. Windows has native support for QUIC since Windows 11 and Server 2022, where it’s used by system services and apps including Microsoft Edge.
Vulnerability Type: Denial of Service (DoS)
- Affected Systems: Windows 11, Windows Server 2022 (systems running the built-in QUIC implementation)
How Does It Work?
The root of the vulnerability lies in how Windows’ QUIC stack processes certain malformed packets. By sending a flood of specially constructed QUIC traffic, an attacker can trigger a resource exhaustion or crash — essentially "denying service" to legitimate users.
Think of it as feeding an application an unexpected or malformed input that it doesn't know how to handle, causing it to freeze or shut down. This is a classic denial-of-service scenario.
Technical Breakdown
Microsoft’s security advisory is, by design, light on technical details. Still, enough can be inferred from the public patches and limited disclosure.
Basic Conceptual Exploit (Pseudocode)
Let’s say a vulnerable Windows server listens for QUIC connections. An attacker can send a wave of malformed data that abuses how the server checks incoming packet headers — perhaps influencing how memory is allocated or which code paths are run.
Here’s a Python snippet that gives you the gist (for learning/defensive testing only!)
import socket
target_ip = "10...5"
target_port = 4433 # Replace with actual QUIC service port
# Fake a QUIC packet header with intentional errors
malformed_quic_packet = b'\xc3' + b'\x00' * 120 # Typical minimum QUIC packet size, but wrong format
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
for _ in range(100): # Send a burst of malformed packets
sock.sendto(malformed_quic_packet, (target_ip, target_port))
sock.close()
print("Sent malformed QUIC packets for DoS testing.")
Note: You must own or have explicit permission to test against any target. This is for educational awareness ONLY. Don’t attack real systems.
What’s happening here? The crafted UDP packets look like QUIC, but their header fields are invalid, potentially triggering a buggy handling path in the service.
Network Proof-of-Concept: wireshark Display
If you want to see if your network is being spammed with suspicious QUIC packets, you can use a Wireshark filter like:
udp && quic
and inspect packets for irregular fields or unusually high traffic rates.
Original References and Links
- Microsoft Security Guidance: CVE-2024-26190
- QUIC Specification (IETF RFC 900)
- Windows QUIC on GitHub – Microsoft’s open source implementation
- Microsoft Patch Tuesday Summary (Feb 2024)
Here’s how to defend your systems
1. Patch Immediately: Ensure your Windows servers and workstations are up to date as of February 2024 or later.
2. Network Filtering: Block unexpected external UDP traffic to QUIC service ports unless explicitly needed.
3. Monitor for Unusual Activity: Use network monitoring to spot spikes in UDP/QUIC traffic, which could signal a DDoS attempt.
Least Privilege: Limit the use of QUIC-based services to systems that really need it.
5. Incident Response: Practice restoration so you can quickly recover if a service crash does occur.
In Summary
CVE-2024-26190 is a classic example of a "low and slow" denial-of-service flaw in protocol code. It reminds us: new standards like QUIC, while promising, may introduce new risks when integrated into big platforms like Windows.
Stay safe: Patch early, monitor traffic, and keep learning!
If you run Windows servers, applying the February 2024 updates is all you need to be protected against known exploits for CVE-2024-26190.
*Want to dive deeper or get updates? Check the Microsoft MSRC CVE page or subscribe to a vulnerability alert service.*
*Written exclusively for you—understand, patch, and stay ahead of the next wave of internet attacks.*
Timeline
Published on: 03/12/2024 17:15:57 UTC
Last modified on: 03/12/2024 17:46:17 UTC