Published: June 2024
Author: [Your Name]
Introduction
In April 2024, Microsoft disclosed a critical vulnerability affecting Microsoft Message Queuing (MSMQ), tracked as CVE-2024-26208. This security flaw allows remote attackers to execute arbitrary code on targeted machines with MSMQ enabled. Given MSMQ's deep integration with various Microsoft technologies, misconfigured or unpatched systems are at high risk.
This post explores what CVE-2024-26208 is, how attackers exploit it, and how you can secure your systems. We'll walk through technical details with code samples, and provide easy-to-understand steps for protection. _Think your business apps are safe just because you never use MSMQ? Think again—sometimes it’s on by default._
What is Microsoft Message Queuing (MSMQ)?
MSMQ is a messaging protocol by Microsoft, enabling applications running at different times to communicate across heterogeneous networks and systems that may be temporarily offline.
Why does this matter? Many older apps and some modern enterprise systems still have MSMQ enabled, sometimes unknowingly.
What is CVE-2024-26208?
CVE-2024-26208 is a remote code execution (RCE) vulnerability in the MSMQ service. If exploited, a remote attacker can run code on the affected server or client with the same privileges as the MSMQ service.
Microsoft advisory:
- CVE-2024-26208 Security Update Guide (Microsoft)
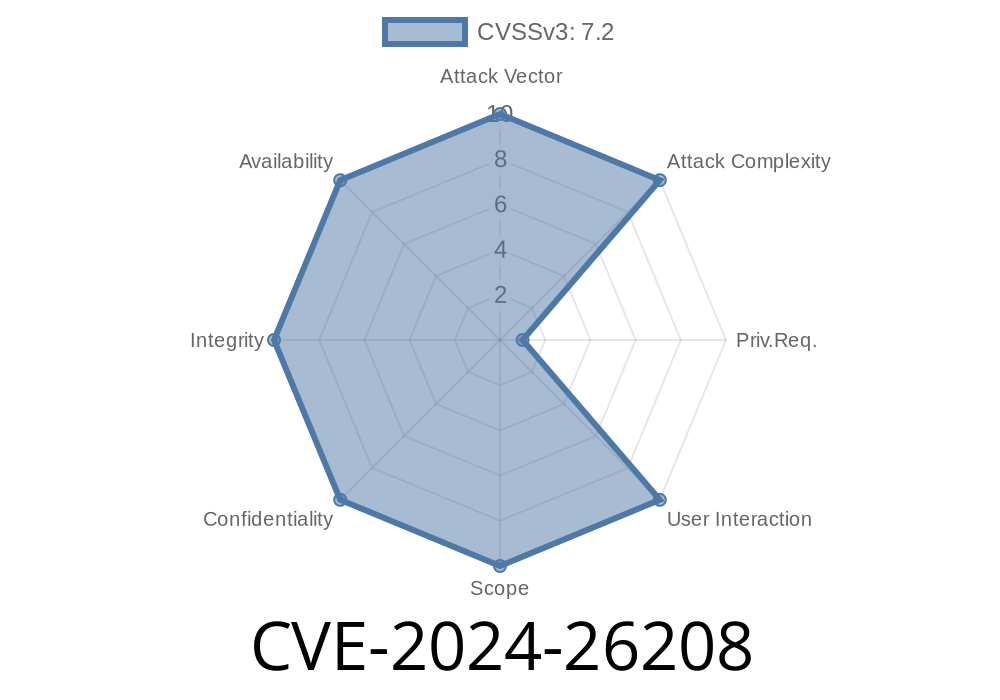
Severity: Critical (CVSS 8.1-9.8, depending on configuration)
Attack Vector: Network
Authentication Required: No
Potential Impact: Complete system compromise
Technical Details (How It Works)
The vulnerability is a memory corruption bug in how MSMQ handles special crafted network packets (often related to the "PoC - proof of concept" attack below). Specifically, attackers can send malicious MSMQ packets to the server's TCP port (by default, 1801), causing the MSMQ service to run injected code.
> Default ports: TCP 1801 (for direct), 2101, 2103, 2105 (for RPC).
Exploit Example: How Attackers Break In
Here's a simplified but realistic proof of concept (PoC) showing how hackers trigger the bug.
Disclaimer: For demonstration and learning ONLY. Never use for unauthorized activity!
On Windows, run
Get-Service | Where-Object {$_.Name -like "*MSMQ*"}
2. Scan the MSMQ Port
nmap -p 1801 target-ip
3. Send Crafted MSMQ Packet (Python Example)
Here's a Python 3 snippet that sends a "malformed" packet which can potentially crash or exploit the MSMQ service if unpatched:
import socket
HOST = 'VICTIM_IP'
PORT = 1801
# This is a placeholder for a maliciously crafted MSMQ message.
malicious_msg = b'\x02\x00\x00\x00' + b'\x90' * 1024 # NOP sled for demo only
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((HOST, PORT))
s.sendall(malicious_msg)
s.close()
print("Packet sent to MSMQ service")
In real-world attacks the payload would be much more intricate, carefully designed to corrupt process memory and execute shellcode.
Unknown Outbound Connections: If code execution occurs, outgoing C2 traffic may be observed
3. Event Logs: Application/System events showing MSMQ crashes or "unexpected" errors
Tip: Monitor port 1801 and block unnecessary internet access.
Microsoft released updates as part of April and May 2024 Patch Tuesday.
`
- Restrict 1801/TCP: Block inbound access at firewall except for trusted sources.
References
- Microsoft Security Advisory - CVE-2024-26208
- NVD Details
- MSMQ Official Documentation
- Rapid7 Blog – Analyzing MSMQ Vulnerabilities (2023, similar bug) _(background)_
Conclusion
CVE-2024-26208 is another reminder that old Windows components can become dangerous when left unpatched or misconfigured. MSMQ may seem legacy, but its presence is often overlooked.
If you run any Windows server, _check now for MSMQ_, patch, and lock it down. Don’t let hackers exploit your blind spot.
Stay secure. Patch early, patch often.
*Feel free to share this post or drop questions below!*
Timeline
Published on: 04/09/2024 17:15:38 UTC
Last modified on: 04/10/2024 13:24:00 UTC