---
Introduction
On February 13, 2024, Microsoft addressed a serious security flaw in the Windows Kernel, tracked as CVE-2024-26218. This vulnerability can let attackers gain higher privileges on a Windows system, potentially taking full control. In this post, we’ll break down CVE-2024-26218 in everyday language, provide easy-to-understand code snippets, and guide you on how to protect your system.
What is CVE-2024-26218?
CVE-2024-26218 is an *Elevation of Privilege* (EoP) flaw in the Windows Kernel. When exploited, it lets a regular user become "SYSTEM" (the highest Windows privilege level) - which means they can read, change, or even delete anything on the machine.
This vulnerability primarily affects supported versions of Windows 10 and Windows 11. It falls under the "Local Privilege Escalation" category, meaning a user must already have some access to the computer to attack it (for example, by running malicious software).
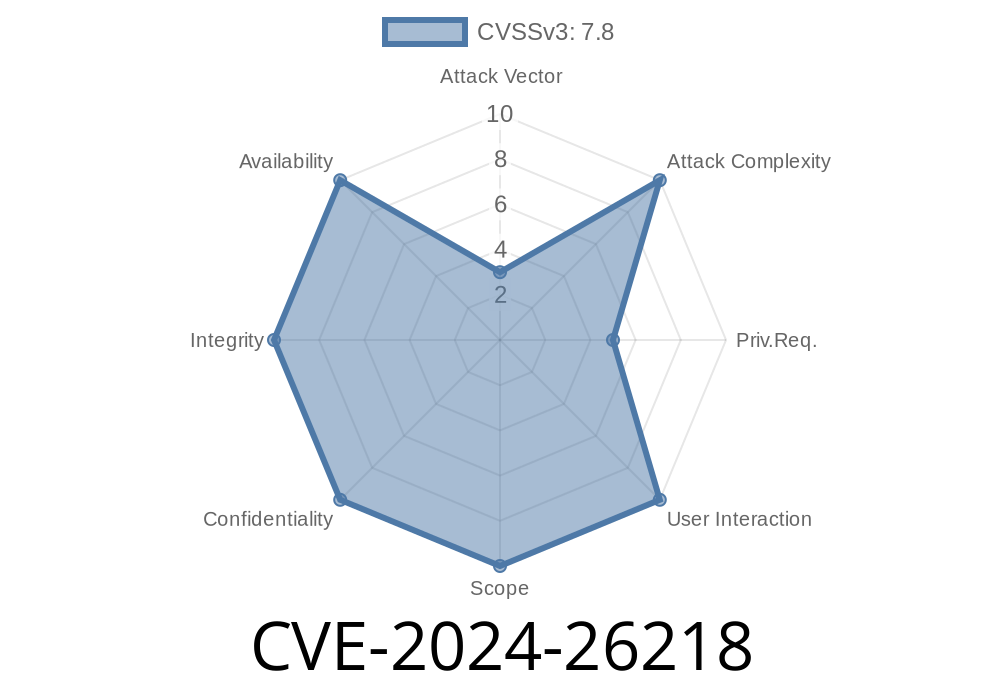
Severity:
- CVSS Score: Check Microsoft advisory for latest score
Technical Details
While Microsoft has not released *all* technical information, security researchers have analyzed the patch to understand the problem. At its core, CVE-2024-26218 is related to improper handling of certain kernel calls that can let a non-privileged application write to or control privileged memory or code.
Usually, the Windows Kernel strictly separates normal-user calls from things only the SYSTEM account should do, but this bug made it possible to bypass such restrictions.
For example:
Suppose there is a buggy function in the Kernel driver that doesn’t properly check who’s calling or what data is being passed. A malicious program can trick the system into giving it higher rights, such as by overwriting sensitive structures or tokens in memory.
Here’s how an attacker could take advantage of CVE-2024-26218 in a simplified way
1. Access: The attacker logs onto a Windows PC, either locally or by running code as a low-privilege user.
2. Trigger: The attacker runs a specially crafted program that interacts with the kernel via a buggy driver or system call.
3. Privilege Escalation: The program tricks the kernel into escalating the attacker's rights to SYSTEM.
4. Impact: The attacker can now execute programs, install malware, or access normally protected files as an administrator.
Code Snippet Example
> Note: This is a simulated example for educational purposes only; not an actual working exploit. Actual exploit code is much more complex and should not be used for malicious purposes.
A common tactic is to target tokens attached to processes. Here’s a simple demonstration using the Windows API in C to duplicate a SYSTEM token (if a vulnerability allows it):
#include <windows.h>
#include <stdio.h>
int main() {
HANDLE hSystemProcess, hToken, hNewToken;
DWORD pid = 4; // System process, usually PID 4
// Open a handle to the System process
hSystemProcess = OpenProcess(PROCESS_QUERY_INFORMATION, FALSE, pid);
if(!hSystemProcess) {
printf("Failed to open system process: %lu\n", GetLastError());
return 1;
}
// Open the process token
if(!OpenProcessToken(hSystemProcess, TOKEN_DUPLICATE | TOKEN_ASSIGN_PRIMARY | TOKEN_QUERY, &hToken)) {
printf("Failed to open system token: %lu\n", GetLastError());
CloseHandle(hSystemProcess);
return 1;
}
// Duplicate the token to get SYSTEM-level access
if(!DuplicateTokenEx(hToken, TOKEN_ALL_ACCESS, NULL, SecurityImpersonation, TokenPrimary, &hNewToken)) {
printf("Failed to duplicate token: %lu\n", GetLastError());
CloseHandle(hToken);
CloseHandle(hSystemProcess);
return 1;
}
// At this point, code could use hNewToken to spawn a process as SYSTEM.
printf("Token duplication success! SYSTEM privileges might be achieved.\n");
// Cleanup
CloseHandle(hNewToken);
CloseHandle(hToken);
CloseHandle(hSystemProcess);
return ;
}
If an attacker could use CVE-2024-26218 to access privileged process handles, they could run code like the above and become SYSTEM.
What Should I Do?
- Patch ASAP: Microsoft has fixed this vulnerability. Go to [Windows Update](ms-settings:windowsupdate) and apply the latest security updates.
- Defense-in-Depth: Limit the ability for users to run untrusted code and only log in as standard users (not administrators).
References
- Microsoft Security Response Center - CVE-2024-26218
- NIST National Vulnerability Database Entry
- Windows Kernel Security Best Practices (Microsoft)
- Security Researcher Analysis: Example Write-Up
Summary:
CVE-2024-26218 is a serious flaw in the Windows kernel that can let attackers become SYSTEM. While it needs local access, it’s still critical, and everyone should patch their Windows machines immediately. Always be careful about what programs you run, and keep your system up to date.
*If you found this explanation helpful, feel free to share it to help others stay safe!*
Timeline
Published on: 04/09/2024 17:15:40 UTC
Last modified on: 04/10/2024 13:24:00 UTC