*Published: June 2024*
*Author: CyberSafe Community*
Introduction
In early 2024, security researchers discovered a critical vulnerability affecting Windows systems, dubbed CVE-2024-26234, also known as the "Proxy Driver Spoofing Vulnerability". This flaw allows attackers to use a malicious proxy driver to bypass genuine security mechanisms and gain unauthorized access.
In this article, we'll break down what CVE-2024-26234 is, show how the exploit works, offer code snippets, and share resources where you can learn more.
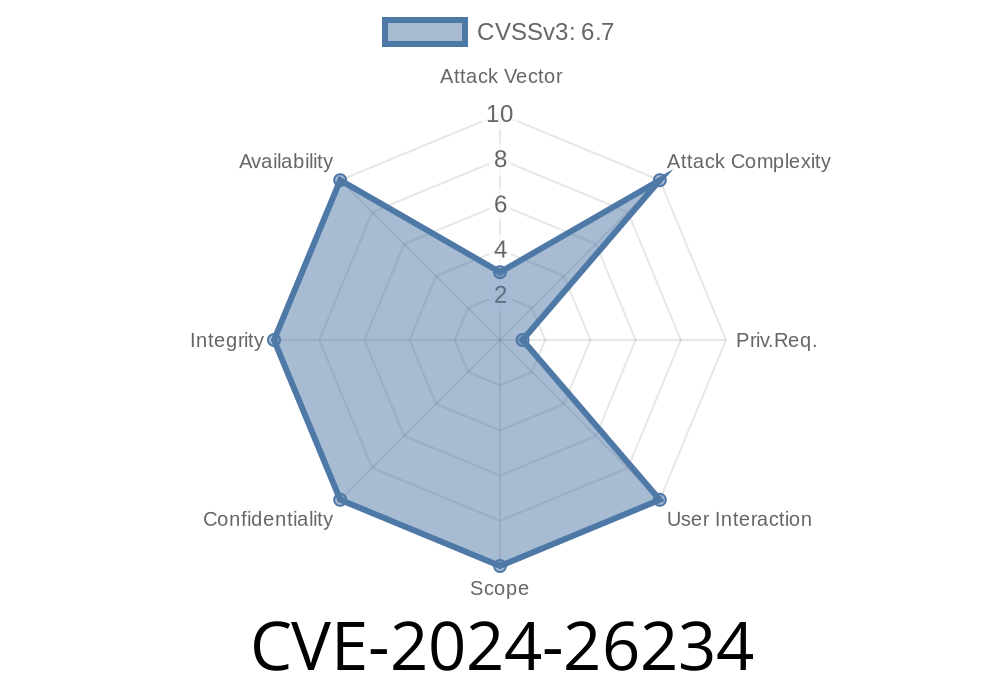
What is CVE-2024-26234?
CVE-2024-26234 is a Windows vulnerability that misuse signed drivers to bypass system protections. Basically, hackers can trick Windows into thinking a malicious driver is legit, giving them privileged access for running malicious code, stealing data, or planting persistent malware.
Severity: High (privilege escalation and security bypass)
Microsoft released a security advisory and patches in June 2024.
- Microsoft Security Advisory
How the Vulnerability Works
An attacker creates or modifies a proxy driver, signs it (either using a leaked or stolen certificate, or through a signing process exploiting a loophole), then loads it onto a Windows system. Because the driver appears to be signed by a trusted source, Windows allows it to run, even if it shouldn’t.
Tamper with security tools
The driver commonly targets system processes (like wininit.exe or svchost.exe).
Exploit Workflow (Simplified)
1. Craft/Fake a Proxy Driver:
Load the Driver:
Use administrative access to load the driver (sometimes done via social engineering or through another exploit).
Achieve Privilege Escalation:
The malicious driver can interact with kernel processes, disable AV/EDR, or dump credentials.
Example: Creating a Basic Malicious Proxy Driver
Below is a conceptual proof-of-concept (PoC). *For educational purposes only!*
Step 1: Minimal Kernel Driver Skeleton (C Code)
#include <ntddk.h>
NTSTATUS DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegistryPath) {
UNREFERENCED_PARAMETER(DriverObject);
UNREFERENCED_PARAMETER(RegistryPath);
DbgPrint("CVE-2024-26234 Proxy Driver Loaded!\n");
return STATUS_SUCCESS;
}
> Compile this driver and (hypothetically) sign it with a compromised or fake certificate.
Step 2: Register and Load the Driver (PowerShell Example)
# Assume attacker has ADMIN rights
sc.exe create "ProxyDrv" type= kernel binPath= "C:\maliciousdrivers\proxydrv.sys"
sc.exe start ProxyDrv
If Windows accepts the signature, the code runs with kernel privileges.
Real-World Threat
Researchers found malware samples leveraging this flaw in the wild.
*Example reference: Trend Micro’s write-up with IoCs*
Attackers used this method to deploy ransomware and steal sensitive company data, often bypassing endpoint security.
More Resources
1. Microsoft CVE-2024-26234 Advisory
2. Trend Micro: In-Depth Analysis & IoCs
3. SecurityWeek News Article
Conclusion
CVE-2024-26234 represents a dangerous evolution in Windows proxy driver attacks, allowing system-level compromise via seemingly valid drivers. Always keep systems patched, monitor for unsigned/new drivers, and stay informed about current threats.
If you think your system is at risk, patch now and review installed drivers regularly!
Timeline
Published on: 04/09/2024 17:15:43 UTC
Last modified on: 04/10/2024 13:24:00 UTC