On March 12, 2024, Microsoft disclosed a critical Remote Code Execution (RCE) vulnerability: CVE-2024-26244. This flaw affects the Microsoft WDAC OLE DB Provider for SQL Server—a component used in countless Windows data applications and enterprise environments. Attackers exploiting this vulnerability could potentially run malicious code on targeted systems, allowing them to steal data, gain persistence, or launch further attacks.
This article will explain CVE-2024-26244 in simple terms, how the exploit works, who is at risk, and will show you relevant snippets of code and best practices to protect yourself. I’ll also share links to original advisories and demonstration resources.
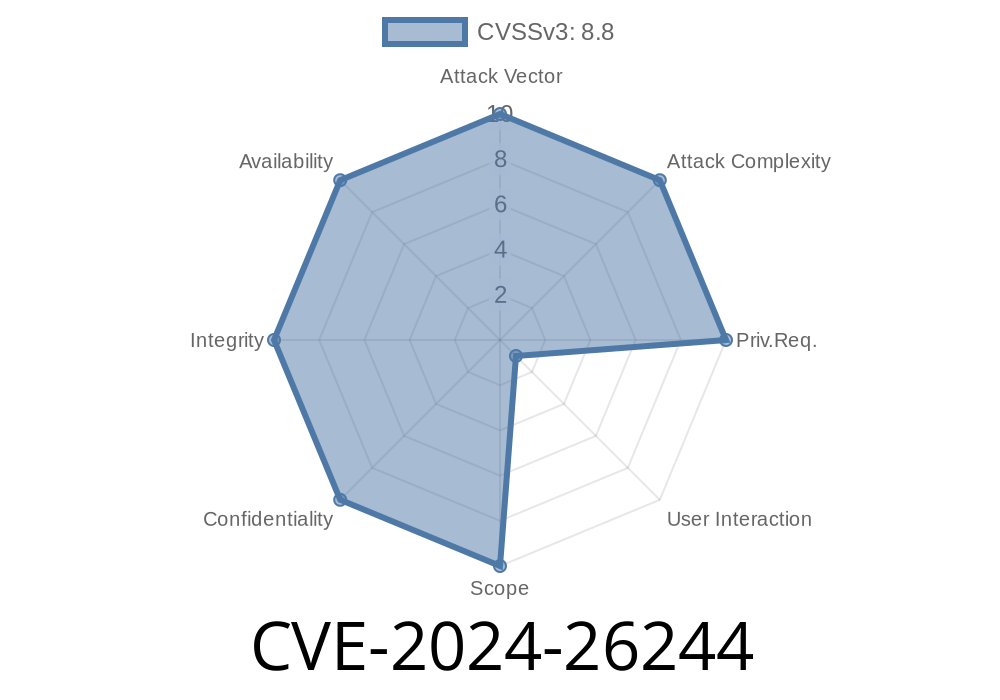
User Interaction: None
This vulnerability allows a remote, unauthenticated attacker to execute arbitrary code on a vulnerable Windows host using a specially crafted OLE DB connection to SQL Server. Since OLE DB is widely used for database connectivity in custom applications, this RCE can be a direct entry point to corporate databases and sensitive application servers.
How Does the Exploit Work?
The vulnerability lies in the way MSOLEDBSQL (Microsoft OLE DB Provider for SQL Server) handles some connection requests and input parameters sent from remote users. Attackers can craft malicious OLE DB connection strings or data packets which trigger a memory corruption or unsafe code execution path inside the provider.
The provider executes code in an unsafe context.
4. Attacker gains code execution—running arbitrary commands as the service account (sometimes with high privileges).
This means any custom Windows application (including web apps and services) using the OLE DB provider to connect to SQL Server is a possible target if it processes attacker-supplied connection details.
Here’s a simplified code pattern found in thousands of enterprise projects
// Example .NET code possibly vulnerable to CVE-2024-26244
string connString = GetConnectionStringFromUserInput(); // danger
using (OleDbConnection connection = new OleDbConnection(connString))
{
connection.Open();
// ... Query and data logic ...
}
If GetConnectionStringFromUserInput() lets the attacker fully control the connection string, an exploit for CVE-2024-26244 could trigger remote code execution before the application can even validate or sanitize.
Links to Original References
- Microsoft Security Update Guide (MSRC) - CVE-2024-26244
- Microsoft March 2024 Patch Tuesday Details
- NVD CVE Record for CVE-2024-26244
`
Provider=MSOLEDBSQL;Data Source=server;User ID=admin;Password=whatever;ApplicationIntent=malicious_payload...
If vulnerable, the app’s process loads attacker-controlled data and executes arbitrary code.
4. Attacker now has access to the Windows host (can drop malware, open backdoors, exfiltrate data, etc.)
Even if you don’t see an exploit today, history shows proof-of-concept code often emerges as security researchers reverse engineer the patch.
Custom applications using OLE DB for SQL Server.
- Web apps or network services that let users/clients control parts of the connection string.
Install all Windows and MSOLEDBSQL updates released after March 2024.
- Download the latest Microsoft OLE DB Driver for SQL Server
2. Sanitize all user-controlled input—never let users specify connection strings or untrusted parameters.
3. Restrict network access to applications/services using OLE DB (firewalls, segmentation).
Conclusion
CVE-2024-26244 is a serious RCE flaw lurking in the Microsoft WDAC OLE DB Provider for SQL Server. Most enterprise environments have at least one app using OLE DB, so patching is urgent. Double-check your own codebase to make sure no user input can control connection information, and always stay updated with the latest Microsoft advisories.
Don’t underestimate this one: It can turn a simple SQL connection into an attacker's beachhead!
For more details, read Microsoft's official advisory here.
*Stay safe, update often, and never trust user input!*
Timeline
Published on: 04/09/2024 17:15:45 UTC
Last modified on: 04/10/2024 13:24:00 UTC