In February 2024, Aruba Networks disclosed a vulnerability tracked as CVE-2024-26302 affecting their widely used ClearPass Policy Manager. This vulnerability, rated as “medium” severity, caught the attention of security professionals, as it allows a low-privileged authenticated user to access sensitive information through ClearPass’s web-based management interface. In this post, we’ll explain the vulnerability in simple terms, explore how it can be exploited, and give you steps to secure your networks.
What is ClearPass Policy Manager?
ClearPass Policy Manager is a network access control solution used by organizations to secure, manage, and enforce access policies for wired and wireless networks. It acts as a central “brain” for user/device authentication and policy enforcement.
Summary of CVE-2024-26302
Vulnerability Type: Information Disclosure
Attack Vector: Remote, Authenticated (Low Privilege)
Affected Products: ClearPass Policy Manager 6.11.x and possibly earlier
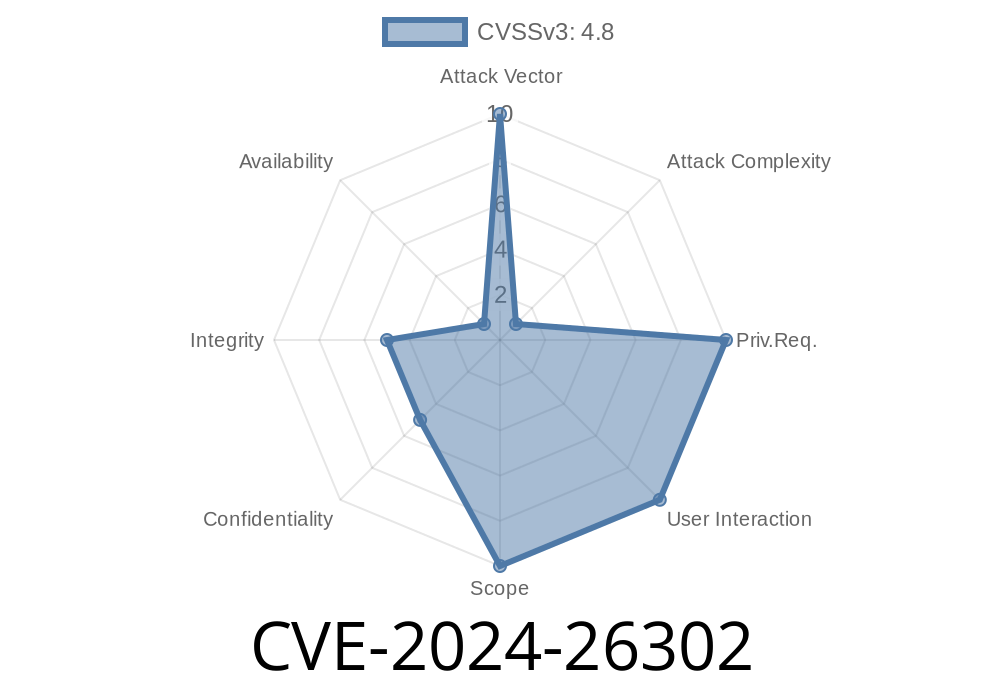
CVSS Score: [As per Aruba's advisory – see below]
Official Advisory: Aruba Security Advisory ARUBA-PSA-2024-003
Short Summary:
A flaw in ClearPass’s admin web interface lets a user with minimal access rights retrieve data they’re not supposed to see, including sensitive configuration details. If exploited, this could help an attacker plot further moves inside the network.
How Does the Vulnerability Work?
Aruba’s admin panel is supposed to limit what low-privileged users can access. However, due to inadequate backend checks on some API endpoints and web requests, attackers with these lower creds can make direct requests—either via the web UI or the API—to endpoints that spill information. This typically includes details about:
LDAP or RADIUS server settings
The key issue: Backend permissions weren’t handled correctly, so the web interface sometimes returns sensitive data to users who shouldn’t get it.
Maybe a helpdesk, guest, or temporary staff account with *minimal access* to ClearPass.
2. Malicious API/Web Request Issued
Attacker finds (by poking around or with guidance from public info) a “leaky” endpoint, such as /api/endpoint/resource or a diagnostic URL.
Dumping Sensitive Information
Attacker receives information about the network’s setup, other users, or authentication servers—the exact details could differ by ClearPass version and configuration.
Sample Exploit: Proof-of-Concept (PoC)
Below is a simplified Python script using the requests library to demonstrate querying an endpoint vulnerable to information disclosure (adjust endpoint as relevant):
import requests
# Replace with the real ClearPass URL and low-priv user credentials
clearpass_url = "https://clearpass.example.com/api/endpoint/resource";
creds = ("lowprivuser", "password123")
session = requests.Session()
session.auth = creds
session.verify = False # Ignore SSL warnings for testing
response = session.get(clearpass_url)
if response.status_code == 200:
print("[+] Received response!")
print(response.text)
else:
print(f"[-] Request failed: HTTP {response.status_code}")
> Warning: Only run exploitation code in your legal environment! This is for education only.
What might show up:
Configuration parameters, user listing, internal IPs, or hints about other services—enough for an attacker to plan lateral movement or privilege escalation.
Potential Impact
- Privilege Escalation Prep: Exposed info might include user lists, hashes, or config data that helps an attacker escalate.
- Lateral Movement Insights: Details about authentication servers (like RADIUS or LDAP) could be reused for attacks against those systems.
- Situational Awareness for Attackers: The “blueprint” of your network’s auth controls, policies, and even logs.
Aruba’s Official Security Advisory:
MITRE CVE Record:
ClearPass Release Notes (Remediation Info):
Conclusion
*CVE-2024-26302* highlights why rigorously checking permissions in admin interfaces matters so much—even users with “just enough” rights can sometimes pry loose sensitive info if the backend isn’t careful. Patch, audit, and monitor your ClearPass systems, and don’t ignore low-privilege users in your threat models.
Timeline
Published on: 02/27/2024 23:15:07 UTC
Last modified on: 02/28/2024 14:06:45 UTC