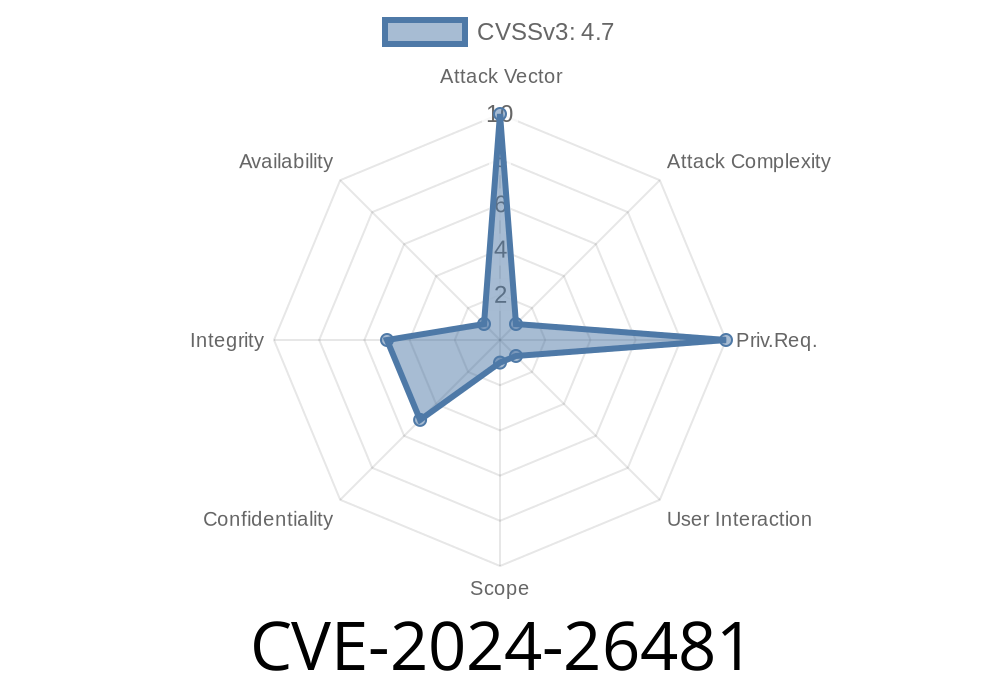
In early 2024, security researchers uncovered a weakness in Kirby CMS, a popular file-based content management system used by thousands of websites. The vulnerability, now identified as CVE-2024-26481, can be found in Kirby CMS version 4.1. and lets attackers trigger a reflected self-XSS attack using the url parameter.
Below, we'll walk through what this means, show how the vulnerability works, include code snippets, and link to additional resources—using a simple and clear approach for developers and site owners.
What is Self-XSS and Reflected XSS?
XSS (Cross-Site Scripting) is a web security weakness where attackers inject malicious scripts into websites, which then run in another user's browser. Self-XSS is a sub-type, where users trick themselves into running a script (often by pasting code into their own browser).
Reflected XSS means the injected code is received as part of a request and *immediately* returned in the web response, instead of being saved and rendered later.
How CVE-2024-26481 Works
In Kirby CMS v4.1., a developer found that the web application doesn't properly sanitize the value passed in the url parameter. This allows a user to manipulate the page so that JavaScript code can be injected and executed within their own session (self-XSS).
This is dangerous because savvy attackers can social engineer a site admin or editor into clicking or pasting a malicious link, leading to session hijacking, data theft, or other browser-based attacks.
Below is a simple representation of what might happen inside a vulnerable Kirby CMS PHP controller
// Hypothetical code inside Kirby CMS
$url = $_GET['url'] ?? '';
echo "Go to page: <a href=\"$url\">$url</a>";
Here, the value from the url parameter is injected right into the HTML without any escaping or sanitization. If a user visits:
https://victim-site.com/panel/some-page?url=javascript:alert('XSS')
The browser will render a link like this
<a href="javascript:alert('XSS')">javascript:alert('XSS')</a>
`
https://target-site.com/panel/some-page?url=javascript:alert(document.cookie)
Send this link to a user with privileged access (like an admin) and persuade them to click it.
3. If the admin clicks, their browser executes the JavaScript (alert(document.cookie)). An attacker could easily swap in a more dangerous payload that steals session information.
Proof of Concept (PoC)
Here’s a real-life PoC you can use for testing on a vulnerable instance (do not use this maliciously!):
https://YOUR-KIRBY-SITE.com/panel/some-feature?url=javascript:alert('CVE-2024-26481')
If the CMS shows this as a clickable link and triggers an alert, it’s vulnerable.
To protect your Kirby CMS site
1. Always sanitize output: Use PHP functions like htmlspecialchars() or Kirby’s built-in safe HTML methods.
2. Upgrade: The Kirby developers quickly addressed this in newer versions. Always update to the latest Kirby release!
3. Content Security Policy (CSP): Enable CSP headers to reduce XSS impact.
Example of a Secure PHP Output
$url = htmlspecialchars($_GET['url'] ?? '', ENT_QUOTES, 'UTF-8');
echo "Go to page: <a href=\"$url\">$url</a>";
References & Further Reading
- CVE-2024-26481 Details on CVE.org
- Kirby CMS Official Website
- Kirby Security Advisories
- XSS Explained (OWASP)
Conclusion
CVE-2024-26481 is a real example of why simple parameter handling can lead to dangerous vulnerabilities—even with trusted CMS platforms. If you use Kirby CMS, update to the latest version and sanitize all user-supplied data.
Timeline
Published on: 02/22/2024 05:15:09 UTC
Last modified on: 08/14/2024 20:35:08 UTC