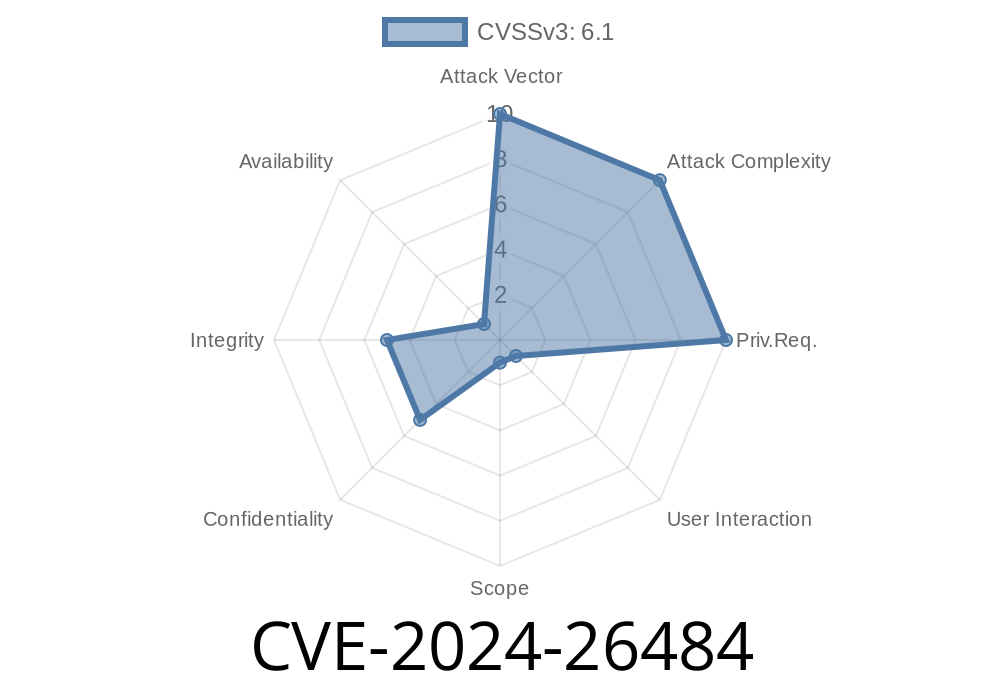
Summary:
CVE-2024-26484 uncovers a stored Cross-Site Scripting (XSS) vulnerability in the Edit Content Layout module of Kirby CMS v4.1.. This bug enables attackers to inject and execute malicious scripts via the “Link” field. Although the Kirby team states production versions aren’t affected, and only the demo site was exposed, the issue is an excellent case for learning about stored XSS vulnerabilities in CMS platforms.
What Is CVE-2024-26484?
On February 22, 2024, a security researcher discovered that it was possible to inject a script payload in the “Link” field when editing content layouts in Kirby CMS v4.1.. Once a payload was saved, it would execute for any user viewing the crafted content — classic stored XSS.
However, Kirby’s official position (Advisory link):
> “This issue did not affect any customer instance of Kirby; only the trykirby.com demo environment was vulnerable.
> *No official patch, no user action required.*”
How Does the Attack Work?
A malicious user logs into the trykirby.com demo, edits a page or module, and inserts a harmful script like <script>alert("Hacked!");</script> into the “Link” field. If a site editor later views the content, the script runs in their browser.
Go to Demo:
Open trykirby.com and use the live editor.
Here’s what an attacker might submit in the “Link” field
"><script>alert('CVE-2024-26484 XSS')</script>
Or wrapped in an image for bypasses
<img src="#" onerror="alert('CVE-2024-26484 XSS Exploit')">
The payload is saved to the server and served to others later.
- Exploiting this bug could allow attackers to steal cookies, perform actions as other users, or escalate privileges on multi-user sites.
If present in a customer-hosted CMS, such a bug could be devastating.
But again, Kirby states only their demo site was vulnerable.
Official References
- GitHub Advisory: CVE-2024-26484
- NVD Entry — CVE-2024-26484
- Kirby CMS
- trykirby.com
Mitigation
No patch is required for production Kirby installs.
Conclusion
CVE-2024-26484 is a textbook example of stored XSS. While no real Kirby users were at risk, it’s a great lesson on defense-in-depth — always sanitize fields, even in demos. If you build or test CMS software, set up secure sandboxing to avoid similar slip-ups.
Timeline
Published on: 02/22/2024 05:15:10 UTC
Last modified on: 08/26/2024 19:35:24 UTC