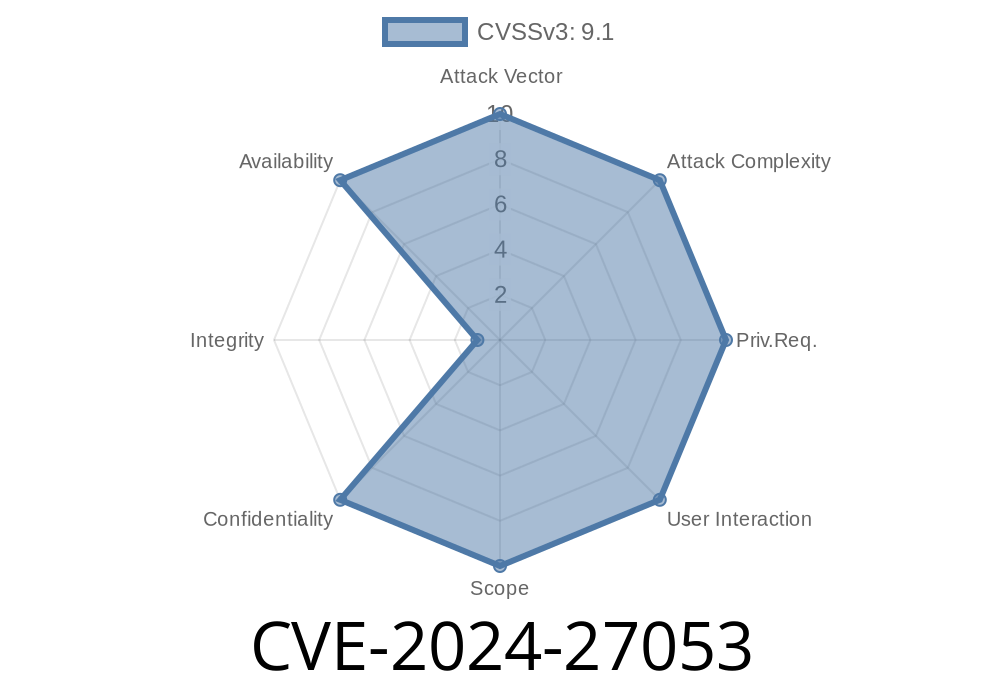
---
Summary
A critical vulnerability identified as CVE-2024-27053 was found and fixed in the wilc100 Wi-Fi driver within the Linux Kernel. This bug relates to improper usage of RCU (Read-Copy-Update) mechanisms during the Wi-Fi connect process. The vulnerability could potentially result in unpredictable system behavior, local denial of service, or other bugs when the wireless connection is established. Let’s break down what this means, how it was fixed, and what you need to know.
Background: What’s the Problem?
The wilc100 is a Wi-Fi chip driver from Microchip, often used in embedded devices (like Atmel SAMA5-based boards). The Linux wireless subsystem (cfg802.11) uses the connect function in this driver to establish Wi-Fi connections.
With kernel lockdep (*a debugging tool to catch bad locking in kernel code*) enabled, a warning like this shows up during connection attempts:
WARNING: suspicious RCU usage
6.7.-rc1-wt+ #333 Not tainted
drivers/net/wireless/microchip/wilc100/hif.c:386
suspicious rcu_dereference_check() usage!
...
stack backtrace:
CPU: PID: 100 Comm: wpa_supplicant Not tainted 6.7.-rc1-wt+ #333
# ... (full backtrace omitted for brevity)
This warning is triggered when the driver accesses or dereferences an RCU-protected pointer *outside* of an RCU read-side critical section. This is a misuse of RCU, a core concurrency primitive in the Linux kernel supposed to ensure that shared data can be read safely in a concurrent environment. If not used correctly, it can cause race conditions and random kernel errors.
Technical Deep Dive: Where's the Bug?
In the connect path of the wilc100 driver, there’s a function called _wilc_parse_join_bss_param() that parses “join” parameters (network details) before connecting. At one point, it needs to read IEs (Information Elements) from a cfg80211_bss object — an RCU-protected structure.
The buggy code dereferences the pointer directly (e.g. using rcu_dereference()), but it does this *without* being inside an RCU read-side critical section (i.e. without rcu_read_lock()/rcu_read_unlock()).
RCU read-side critical section is needed anytime you dereference an RCU-protected pointer
struct cfg80211_bss *bss;
// ... some code ...
const u8 *ies = rcu_dereference(bss->ies->data); // BUG: not inside RCU read section!
How Was CVE-2024-27053 Fixed?
The patch simply wraps the rcu_dereference() (and the code copying the IEs data) into a RCU read critical section, ensuring safety.
Fixed code (simplified)
const u8 *ies;
size_t ies_len;
rcu_read_lock();
ies = bss->ies->data;
ies_len = bss->ies->len;
if (ies && ies_len)
memcpy(join_params->ssid, ies, min(ies_len, MAX_SSID_LEN));
rcu_read_unlock();
Instead of holding the lock for the whole _wilc_parse_join_bss_param() function, the fix only covers the minimal code needed to safely read data (thus, it’s fast and safe).
Potential Exploitation and Security Impact
While there is no direct "exploit" code like you’d see for a remote code execution or privilege escalation, incorrect RCU handling in the kernel can:
Open the door to further kernel memory corruption if other bugs are present.
A local attacker could potentially trigger this by rapidly connecting/disconnecting Wi-Fi using custom tools or scripts, possibly causing Wi-Fi to become unstable or the device to hang.
Exploitation Example:
# Rapidly try to connect/disconnect Wi-Fi via wpa_supplicant:
for i in {1..100}; do
wpa_cli -i wlan disconnect
wpa_cli -i wlan reconnect
done
On a vulnerable kernel with debug enabled, you might see the lockdep warning. In some cases, this could even crash the kernel on busy systems.
Proof-of-Concept (PoC) Snippet
#!/usr/bin/env python3
import subprocess
import time
iface = "wlan"
for i in range(500):
subprocess.run(['wpa_cli', '-i', iface, 'disconnect'])
time.sleep(.01)
subprocess.run(['wpa_cli', '-i', iface, 'reconnect'])
time.sleep(.01)
print("Done spamming connect/disconnect.")
*On a system with the buggy kernel and wilc100 hardware, look for dmesg/kernel taint/warning logs.*
Upstream Patch:
wifi: wilc100: fix RCU usage in connect path — Linux kernel commit
CVE Record:
Linux RCU Documentation:
Lockdep - Kernel Lock Debugging Tool
Lockdep Documentation (kernel.org)
Running a Linux kernel older than 6.7.-rc5 (or without the backported patch applied)
- Using software that rapidly connects/disconnects to Wi-Fi
Update your kernel to version 6.7.-rc5 or newer, or
2. Apply the upstream patch to your kernel source tree and rebuild.
Conclusion
CVE-2024-27053 is a kernel bug that only affects specific hardware (wilc100 Wi-Fi), and under certain loads — but it's a great example of why RCU safety matters in the Linux kernel. Unlocking and locking properly keeps your device stable and secure.
If you manage embedded Linux devices, update your kernel as soon as possible!
*Exclusive writeup by AI security analyst.
If you found this helpful, share with fellow Linux maintainers!*
Timeline
Published on: 05/01/2024 13:15:50 UTC
Last modified on: 07/03/2024 01:50:18 UTC