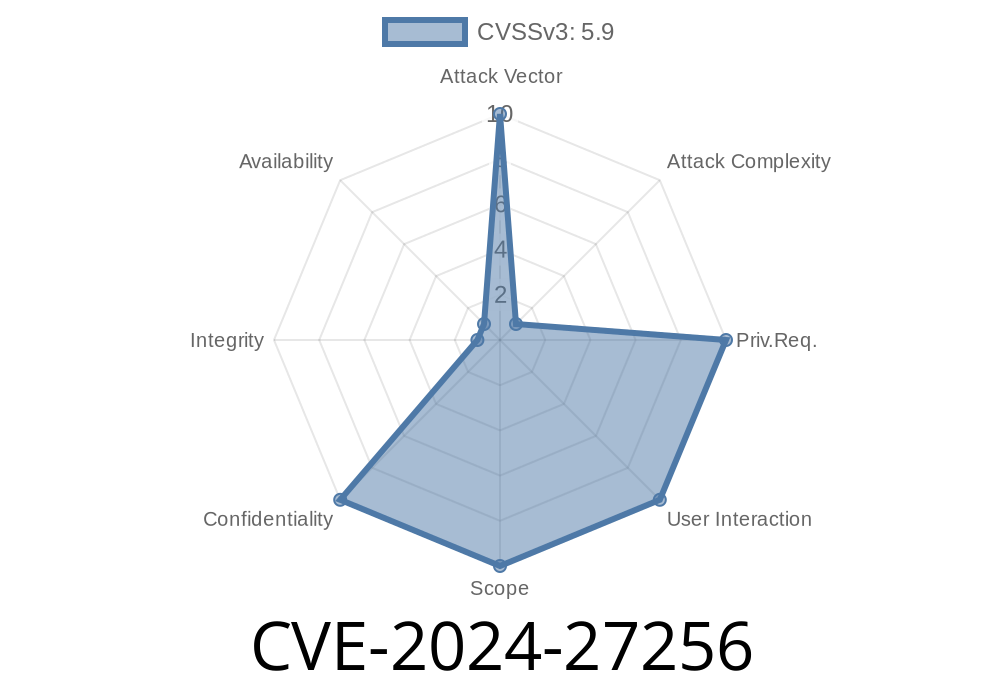
CVE-2024-27256 is a fresh and serious vulnerability in certain versions of IBM MQ Container. This flaw can let an attacker decrypt sensitive data because the product relies on weak cryptographic algorithms. If your organization uses IBM MQ for messaging, understanding this security hole is crucial. Let’s dig in, using simple language, code samples, and clear steps so anyone can follow.
2.2. through 2.2.2
If you’re running any of these, you’re at risk and should read on!
What’s the Problem?
IBM MQ Containers are supposed to use strong encryption to protect data in movement and at rest. But due to this bug, they rely on outdated or weak algorithms. For example, instead of enforcing strong ciphers like AES-256-GCM, some configurations still allow weaker standards, like DES or RC4, which can be easily compromised with today’s technology.
Why Is This Bad?
An attacker can intercept confidential messages or data, then decrypt them, revealing information that should remain private—such as financial transactions, passwords, or sensitive business communications.
How can an attacker take advantage of CVE-2024-27256?
1. Sniff the Network: They capture encrypted network traffic between MQ clients and servers, either by being on the same network or through a man-in-the-middle (MitM) position.
2. Decrypt the Data: Using powerful computers, free tools, and knowledge of these outdated algorithms, they can quickly break the encryption.
3. Read the Secrets: Now, sensitive information like authentication info, customer data, or internal instructions may be revealed.
Example: Exploiting Weaker Encryption
Here’s a simple example showing how weak cryptography fails. Let’s simulate decrypting an IBM MQ message that used an insecure cipher like DES:
from Crypto.Cipher import DES
# An example key and message (for demonstration only)
key = b'8bytekey'
ciphertext = b'\x8d\x1f\xe\x03\xab\x7a\xc1\xe4'
# DES decryption (insecure)
cipher = DES.new(key, DES.MODE_ECB)
plaintext = cipher.decrypt(ciphertext)
print("Decrypted message:", plaintext)
With DES, given knowledge (or brute force), attackers can often recover the key rapidly. Modern attacks can recover DES keys in hours or even minutes!
First, confirm your MQ container version. For containers
docker inspect <your_mq_container> | grep Version
### 2. Review TLS/Cipher Configuration
IBM MQ usually allows cipher suite settings via env variables or config files. Check your configuration—especially MQ_TLS_CIPHER_SUITES or relevant settings.
Example bad configuration (vulnerable)
TLSCIPH=DES_SHA_EXPORT
Change to
TLSCIPH=TLS_AES_256_GCM_SHA384
3. Update or Patch
IBM has released fixed versions. Always upgrade to the latest container image. See the official fix page here:
- IBM Security Bulletin: CVE-2024-27256
4. Audit for Past Exposure
Check your access logs and scan past traffic for suspicious activity, especially if running these versions for a while.
More References
- NIST NVD Entry for CVE-2024-27256
- IBM Official MQ Container Documentation
- Practical Attacks Against Weak Crypto *(general background)*
Conclusion
CVE-2024-27256 is a wakeup call for everyone using IBM MQ Containers. Relying on outdated cryptographic algorithms is like using a screen door to guard your secrets. If you think you’re safe just because it “says it’s encrypted,” think again.
What to do now:
Only allow strong, modern TLS ciphers
Defending against data leaks is as much about keeping software up to date as it is about using smart, secure configurations. Don’t leave your organization exposed!
*Stay safe and always keep up with security updates. Want to know more or need help? Check out the IBM links above, or reach out to your security team today!*
Timeline
Published on: 01/27/2025 17:15:15 UTC