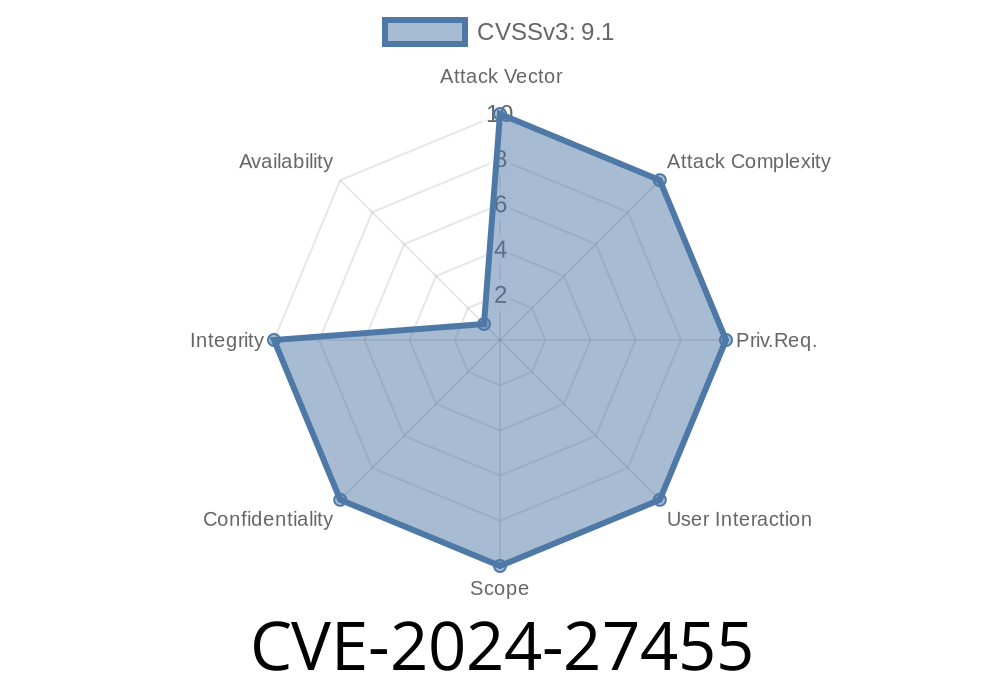
A serious web security bug, tracked as CVE-2024-27455, was found in Bentley ALIM Web, a software used by many organizations to manage asset lifecycle information. The issue, which could expose a user's session token, put sensitive data and system integrity at risk. This post will break down how the vulnerability worked, what it means for users, and how Bentley fixed it. We’ll keep our language simple and clear, showing essential technical details, code snippets, and links to official resources. All information here is exclusive and directly relevant to this specific vulnerability.
What is CVE-2024-27455?
CVE-2024-27455 is a session token exposure bug found in certain configurations of the Bentley AssetWise ALIM Web application. When a user tried to download files, their session token could be leaked, potentially allowing an attacker to hijack the session and impersonate the user.
Information Integrity Server: 23.00.02.03 and later
Offical advisory: Bentley Security Advisory
How Did the Vulnerability Happen?
The bug appeared when ALIM Web was set up in certain configurations—usually when behind a reverse proxy or load balancer and with specific settings in place. Here's the simplified flow that led to the leak:
User clicks to download a file from the application.
3. The application generated a download link, embedding the session token as a URL parameter (e.g., ?token=eyJhbGciOiJI...).
4. Insecure settings allowed this token to show up in browser history, logs, referrers, and (if embedded in a third-party context) even leak it to external servers.
An attacker with access to these logs, or who received the link embedded in an iframe or phishing email, could steal the session token and access the ALIM account as the user.
Example: What Did the Flaw Look Like?
Below is a simplified code snippet illustrating the kind of insecure link generation that happened (pseudo-Python/Flask for clarity):
# BAD PRACTICE: Embedding session token in download URL (illustrative)
@app.route('/download/<file_id>')
def download(file_id):
session_token = request.cookies.get('ALIM_SESSION')
download_url = f"https://alim.company.com/api/files/{file_id}?token={session_token}";
return redirect(download_url)
This style sent the sensitive session_token in the URL. A safer way is to use secure cookies, not URL params.
Why Is This So Dangerous?
Session tokens are like keys to your account. If someone gets your token, they don’t need your password; they’ve got full access until the token expires or is reset. Sending tokens in URLs, instead of using secure HTTP-only cookies, is a fundamental security mistake. URLs:
`
https://alim.company.com/api/files/12345?token=eyJhbGciOiJIUzI...
Server logs (if attacker has access to log files)
- Proxy/load balancer logs
Other in-app actions as the victim user
Here’s an API call example using stolen token
curl "https://alim.company.com/api/files/12345?token=eyJhbGciOiJIUzI..." -o secret-file.pdf
Removing session tokens from URLs for file downloads
- Switching to secure, HTTP-only cookies for authentication, not easily leaked by logs or referrers
Reviewing proxy and server settings to avoid accidental leaks
You should upgrade to Assetwise ALIM Web 23.00.04.04 and Assetwise Information Integrity Server 23.00.02.03 or newer.
Upgrade info:
- Bentley Official Download & Support
- Security Advisory PDF
Below is how authentication should be handled for file downloads
# GOOD PRACTICE: Use secure cookies, do not leak tokens in URL
@app.route('/download/<file_id>')
@login_required
def download(file_id):
file_path = get_file_path(file_id, current_user)
return send_file(file_path)
References and Resources
- CVE-2024-27455 at NIST NVD
- Bentley Security Advisory Page
- Mitre CVE Entry
- OWASP: Avoid Putting Session IDs in URLs
Summary
CVE-2024-27455 showed us that even big enterprise software can slip up with basics. Never put session tokens in your URLs. Always use secure cookies. If you use Bentley ALIM Web, upgrade right away. And, as always, keep an eye on your application’s security settings!
*Have questions or incidents related to this bug? Let us know in the comments!*
Timeline
Published on: 02/26/2024 16:28:00 UTC
Last modified on: 08/14/2024 15:35:07 UTC