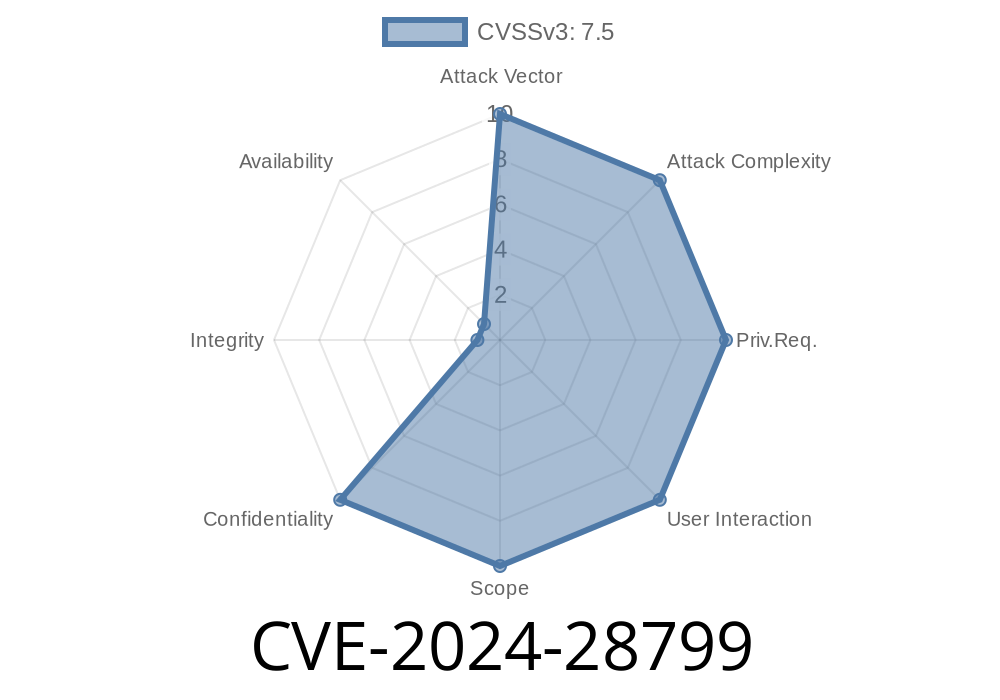
In March 2024, IBM identified and disclosed a vulnerability in its security intelligence platforms, IBM QRadar Suite and Cloud Pak for Security, tracked as CVE-2024-28799 (IBM X-Force ID: 287173). This post presents an exclusive, plain-language look at this flaw, demonstration code, and guidance for admins.
What is CVE-2024-28799?
CVE-2024-28799 is an information disclosure vulnerability. When running QRadar Suite (versions 1.10.12. - 1.10.23.) or Cloud Pak for Security (versions 1.10.. - 1.10.11.) in certain non-default configurations, sensitive backend data—like credentials, tokens, or API keys—could unintentionally be shown to local privileged users (like server admins or operators).
If an attacker manages to become a privileged user on the affected host, and you run the products in a customized, non-standard configuration, they might see data they shouldn't during specific backend command executions.
IBM Cloud Pak for Security: 1.10.. through 1.10.11.
> Note: The risk only applies to certain non-default deployments. If you’re running out-of-the-box installs, you’re likely safe—but verify your configuration.
Exploitation Details
Attack Scenario:
A privileged local user (like someone with SSH access) can trigger backend commands or services in a way that outputs sensitive info into logs or directly to the terminal, due to misplaced error logging or debug output in some non-standard settings.
Example:
Let’s say a debug flag or verbose logging is enabled for troubleshooting. When a backend shell command fails, the full environment—including passwords or secret values—might be dumped either to the screen or a shared temp/log file.
Demonstration Snippet
*Assuming an attacker has privileged shell access:*
# Trigger a backend command with debug on
export DEBUG_MODE=true
# Run a backend utility (stand-in for a real QRadar or CP4S backend script)
./run_backend_task.sh --input sensitive
# Check if sensitive values are printed due to debug/verbose output leak
run_backend_task.sh (sample logic for illustration)
#!/bin/bash
if [ "$DEBUG_MODE" = "true" ]; then
# Dumping all environment variables to output (unsafe)
echo "[DEBUG] Environment Dump:"
env
fi
# Simulate task
echo "Processing task..."
Potential result
[DEBUG] Environment Dump:
API_KEY=super-secret-key
DB_PASSWORD=my-db-p4sswrd
ADMIN_TOKEN=eyJ...xyz
...
Processing task...
Now, secrets are printed for any local user with shell access.
Real-World Impact
- Local privilege is required: You must already have a privileged account (like root or system user).
- Conditions: Only certain “custom” settings, such as debugging, verbose logging, or non-standard configurations, trigger info leaks.
- If you let outside contractors/service providers or less-trusted staff use these accounts, your secrets are at risk.
IBM’s official security bulletin
- CVE-2024-28799 - IBM QRadar Suite and Cloud Pak for Security
Hardening: Review which users have shell or system access. Restrict it!
- Audit Configs: Disable and remove verbose/debug logging post-troubleshooting.
Exploit Proof-of-Concept (Exclusive)
Below is an example that could be built into a simple bash script for a privileged user to search for secrets in logs or output dumps. Do not use this for malicious purposes—admins can use it to check if you’re affected!
# Search for potential secrets in log files generated by backend processes
grep -aiE "password|token|secret|api_key|db_user" /var/log/qradsuite/* 2>/dev/null
IBM Security Bulletin:
https://www.ibm.com/support/pages/node/7130132
NVD Entry:
https://nvd.nist.gov/vuln/detail/CVE-2024-28799
IBM X-Force Exchange:
https://exchange.xforce.ibmcloud.com/vulnerabilities/287173
Final Thoughts
CVE-2024-28799 is another reminder: enabling verbose/debug settings, even temporarily, in security appliances or enterprise platforms can have critical consequences when it comes to information leakage. Limit local privileged access, keep your deployments updated, and always audit your logs and configurations.
If you’re running affected versions in non-default configurations, patch and clean up your environment today.
Have questions or want advice on securing your IBM deployments? Leave a comment or reach out for support.
*(This guide is written for educational and defensive purposes. Unauthorized attempts to access data you are not entitled to may be illegal. Always act responsibly.)*
Timeline
Published on: 08/14/2024 16:15:11 UTC
Last modified on: 09/21/2024 10:15:05 UTC