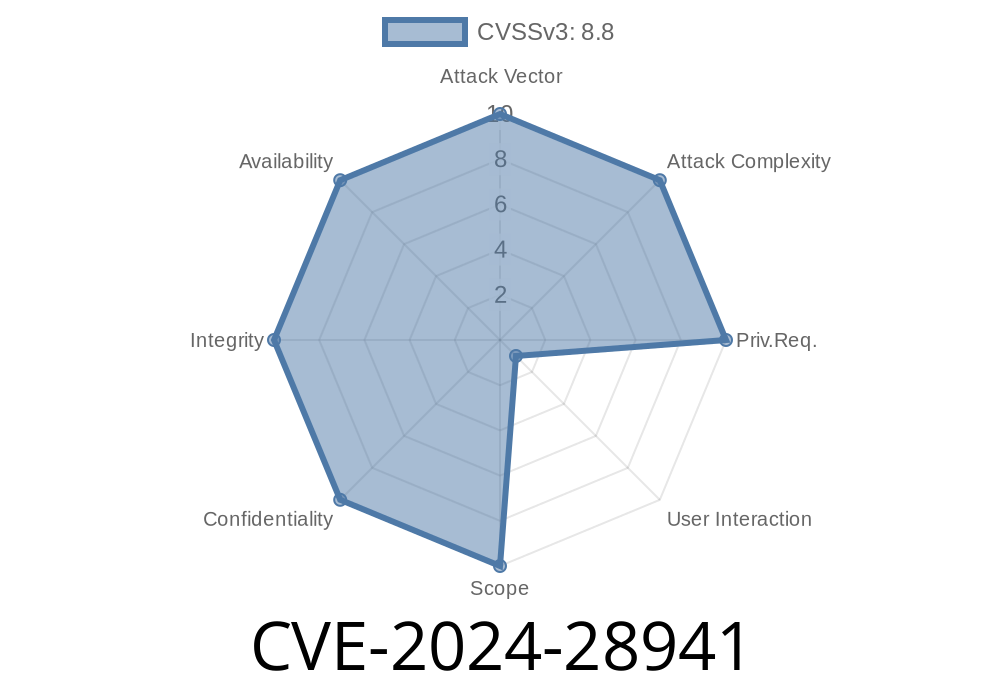
In March 2024, Microsoft addressed a critical security flaw tracked as CVE-2024-28941 which affects the Microsoft ODBC Driver for SQL Server. This vulnerability allows remote code execution (RCE), giving attackers the ability to run arbitrary code on a victim system with the privileges of the application using the ODBC Driver. In this article, we’ll break down what this CVE means, what’s at risk, how it can be exploited, and how you can stay safe. You’ll also find code snippets to help understand the exploit and links to original sources for further reading.
What is the Microsoft ODBC Driver for SQL Server?
The Microsoft ODBC (Open Database Connectivity) Driver for SQL Server is a key software component. It lets Windows applications, scripts, and other services connect and interact with SQL Server databases. Lots of business software and web applications use it every day, so bugs here have serious, wide-reaching consequences.
Type: Remote Code Execution (RCE)
- Impacted Component: Microsoft ODBC Driver for SQL Server (all supported versions before the March 2024 update)
Severity: Critical
- Attack Vector: Remote/Network
Microsoft’s advisory summarizes the impact as follows
> “A remote code execution vulnerability exists when Microsoft ODBC Driver for SQL Server improperly handles objects in memory.”
References:
- Microsoft Official CVE-2024-28941 Advisory
- NVD - CVE-2024-28941
How Does the Exploit Work?
The vulnerability occurs because the ODBC Driver improperly manages memory during specific database connection sequences. If an attacker can trick the application into parsing malicious data (for example, through a crafted DSN string or SQL payload), they may overwrite memory structures and execute their code.
Exploitation Scenario
Suppose an application takes client-supplied connection strings (or accepts SQL queries or DSN names from users or network data). An attacker sends a specially-created string to induce a memory corruption in the ODBC Driver process. This may lead directly to code execution—allowing full compromise of the host application.
Automation scripts using ODBC and processing external data.
- Exposed RDP/PowerShell/management scripts that parse ODBC configs.
Let’s imagine a Python script that connects to SQL Server using ODBC
import pyodbc
# User-supplied DSN - Insecure!
dsn = input("Enter your DSN: ")
conn = pyodbc.connect(f"DSN={dsn};")
If the vulnerability is present, and the attacker inputs a malicious dsn string designed to trigger the flaw, they can potentially cause memory corruption and get the script to execute their own code.
> Note: Actual exploit code is generally more complex and involves binary payloads, but this shows the entry point.
Proof of Concept (PoC) Snippet
WARNING: The code below is for educational purposes and does not contain actual shellcode or payloads. Executing real exploits is illegal without authorization.
# This is a hypothetical PoC for illustration, not a live exploit.
import pyodbc
# Faked "malicious" DSN string to show exploit entry point
# In a real-world exploit, this could contain a format string, buffer overflow, or similar
malicious_dsn = "ATTACKER_PAYLOAD" # Example placeholder
try:
# Vulnerable call if not patched!
conn = pyodbc.connect(f"DSN={malicious_dsn}")
print("Connected!")
except Exception as e:
print("Crash occurred. Possible memory corruption.")
A real attacker would replace "ATTACKER_PAYLOAD" with a specially-crafted value to trigger the underlying vulnerability in the Microsoft ODBC Driver for SQL Server.
Who is at Risk?
- Organizations with apps relying on unpatched versions of Microsoft ODBC Driver for SQL Server (Windows, Linux, macOS).
Patch Immediately:
Microsoft released updates for all supported ODBC drivers (versions 17, 18, and 13.1; includes Windows, Linux, macOS). Get them here:
- Microsoft ODBC Driver for SQL Server downloads
- Relevant MSRC Advisory
Community and Technical Analysis
- SSD Secure Disclosure - CVE-2024-28941 Analysis
- Microsoft Security Update for CVE-2024-28941
Closing Thoughts
CVE-2024-28941 is a major vulnerability because ODBC is everywhere—in dev environments, production apps, cloud services, and more. If your systems or code use Microsoft’s ODBC Driver for SQL Server, you must update immediately. Don’t ignore this risk, as attackers often scan for and exploit such bugs within days of public disclosure.
Stay secure: patch, filter, audit, and monitor.
If you want to dig deeper, here are some handy reference links
- Microsoft Download ODBC Driver for SQL Server
- Official CVE-2024-28941 Details
- Microsoft Security Response Center (MSRC) update
Timeline
Published on: 04/09/2024 17:15:56 UTC
Last modified on: 04/10/2024 13:24:00 UTC