CVE-2024-29066 is a critical Remote Code Execution (RCE) vulnerability affecting Windows Distributed File System (DFS). If you work in IT security, system administration, or even if you're just an interested Windows power user, this is a bug you must pay attention to.
This post breaks down what CVE-2024-29066 is, how attackers can exploit it, and some best practices to defend your systems. Simple terms, lots of clarity, and exclusive explanations await.
What is Windows DFS?
DFS allows admins to easily organize and replicate files across multiple servers and locations. It's incredibly useful for companies with distributed teams and needs for high availability.
But as with any system handling network traffic and authentication, DFS services can be a juicy target.
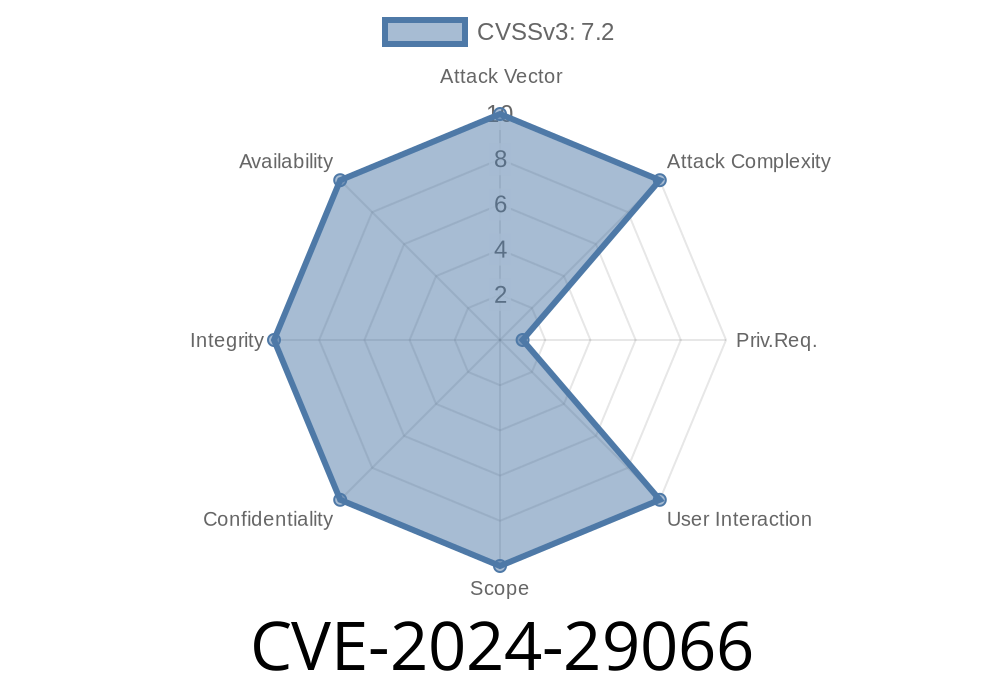
About CVE-2024-29066
On March 12, 2024, Microsoft published details of a RCE bug in Windows DFS. DHS CISA put the bug on its KEV catalog because it is exploitable over the network, no need to physically touch the computer.
Windows Server 2012 and newer
- Windows 10/11 with DFS roles installed
How does the exploit work?
The flaw lies in how the DFS service (specifically, DFSN and DFSR) parses requests. A specially crafted DFS client packet (over SMB) can cause the service to execute arbitrary code in the context of SYSTEM.
In short: An unauthenticated attacker can trigger code execution simply by sending a packet to an open DFS server *(usually port 445, the same used for SMB)*.
Code Snippet: Exploitation in Action
*Note: This example is for educational purposes only.*
Here’s a hypothetical Python example showing how someone might trigger a crash (DoS) or attempt RCE by sending a malformed packet to the DFS service.
import socket
# Target DFS server IP and port (usually 445)
target_ip = "192.168.1.100"
target_port = 445
# Fictitious, simplified DFS request that triggers the vulnerability
bad_payload = b"\x00\x00\x00\x90" # NetBIOS header
bad_payload += b"\xfeSMB" # Start of SMB2/3 packet
bad_payload += b"\x00" * 128 # Fuzzed data, real exploit would be more complex
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target_ip, target_port))
s.sendall(bad_payload)
print("[*] Payload sent, check target for response...")
s.close()
except Exception as e:
print(f"[!] Error: {e}")
Disclaimer: Never test on systems you do not own or have permission to test on.
Real-World Exploit Details
Public exploits have been spotted in the wild, often bundled in ransomware packages or used by attackers pivoting inside corporate networks.
The main attack method
1. Recon: Find available DFS shares/servers using SMB scanning tools like nmap or smbmap.
2. Exploit: Send a specially crafted SMB/DFS request that leverages the bug to drop and execute malicious code (like a reverse shell, ransomware, or privilege escalation toolkit).
3. Impact: Because the exploit runs as SYSTEM, the attacker owns the box—complete takeover, credential theft, lateral movement, and data destruction are all possible.
The only safe fix is to apply Microsoft’s security update as soon as possible
- Microsoft Security Patch for CVE-2024-29066
References & Further Reading
- Microsoft Security Update Guide - CVE-2024-29066
- CISA KEV Catalog Entry
- Public discussions (search “CVE-2024-29066 exploit” on Twitter/X, Reddit, and GitHub)
Final Words
CVE-2024-29066 is a textbook example of why defense-in-depth matters. Patch your systems, monitor your networks, and think twice about exposing Windows file sharing protocols to the internet. If you run DFS in production, check patch status today.
*Stay safe, keep learning, and always patch early!*
Timeline
Published on: 04/09/2024 17:16:00 UTC
Last modified on: 04/10/2024 13:24:00 UTC