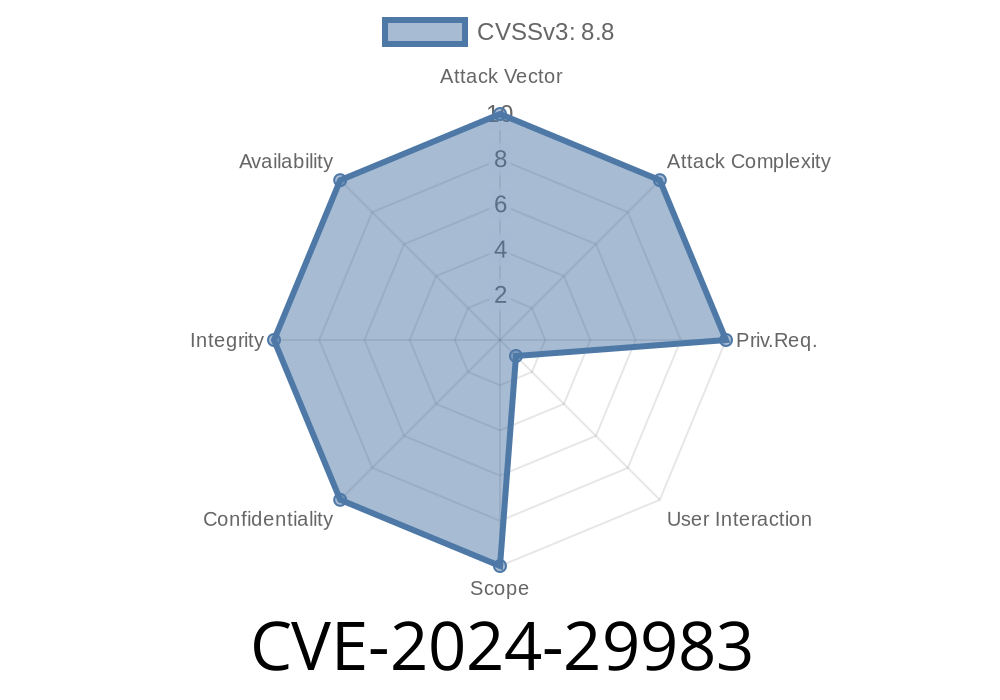
In June 2024, Microsoft acknowledged and patched a high-impact security vulnerability, CVE-2024-29983, affecting the Microsoft OLE DB Driver for SQL Server. The bug allows attackers to execute malicious code remotely on vulnerable systems. This exclusive guide explains what CVE-2024-29983 is, how the exploit works, and what you can do to protect yourself, with code snippets and clear instructions.
What is the OLE DB Driver for SQL Server?
Before diving into the vulnerability, it’s essential to know what we’re dealing with. Microsoft OLE DB Driver for SQL Server is a component that lets Windows applications connect to SQL Server databases. Programs written in various languages (like C++ or PowerShell) use this driver to send queries and manage data.
CVE-2024-29983: Vulnerability Overview
CVE-2024-29983 allows remote code execution (RCE) when the OLE DB driver improperly handles specially crafted inputs. This means an attacker can trick an application, using the OLE DB driver, into running their code—potentially taking control of the affected machine.
How Does the Exploit Work?
Microsoft hasn’t published the fine details (for obvious security reasons), but security researchers describe the bug as a "deserialization" problem or a buffer overflow when handling connection strings. Here’s what the attack flow might look like:
Victim Application Uses OLE DB
The targeted software (maybe a web app running on IIS or a desktop program) passes attacker-supplied data to the OLE DB driver.
OLE DB Driver Fails
Instead of safely rejecting the bad input, a bug in the driver allows the attacker's input to trigger unintended code execution.
Remote Code Execution
The attacker’s code runs on the victim’s system, either opening a backdoor, exfiltrating data, or moving laterally inside the network.
Exploit Demonstration: Example Code Snippet
Below is a conceptual and simplified example (not a real, weaponized exploit!) showing how untrusted connection strings can be a problem when handled unsafely.
import win32com.client
def vulnerable_connect(user_supplied_string):
# BAD: Passing untrusted input directly
conn = win32com.client.Dispatch("ADODB.Connection")
conn.ConnectionString = user_supplied_string
conn.Open()
malicious_string = (
"Provider=MSOLEDBSQL;Data Source=server;Initial Catalog=db;"
"User Id=attacker;Password=Secret;AttackPayload=evilcode"
)
# Simulate passing the malicious string
vulnerable_connect(malicious_string)
In the real world, a more advanced attacker would craft the payload to trigger the vulnerability at a low level, perhaps exploiting buffer overflows.
Real-World Impact
- Web server compromise: An attacker could remotely hack an internet-facing web server that connects to SQL Server using OLE DB.
- Lateral movement: Once inside, they could use the compromised server to jump deeper into a corporate network.
- Data theft and ransom: With full code execution, attackers could steal sensitive data or drop ransomware.
How to Protect Yourself
Patches are available. Microsoft released fixes as part of their June 2024 Patch Tuesday.
Download the latest updates directly from Microsoft's official website:
- MS OLE DB 18 for SQL Server Download
- MS OLE DB 19 for SQL Server Download
Monitor for Exploits
- Watch system logs and security products for unusual activity, especially on systems using the OLE DB driver.
Microsoft Security Advisory:
CVE-2024-29983 - Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability
Security Researcher Write-Up:
NCC Group CVE-2024-29983 Analysis
Microsoft OLE DB Driver for SQL Server Documentation:
Conclusion
CVE-2024-29983 is a significant vulnerability in the Microsoft OLE DB Driver for SQL Server, opening the door for attackers to gain remote access and run code on Windows systems. The solution is *simple but urgent*: patch your drivers, review your code, and stay alert for exploit attempts.
Stay safe. If your organization relies on SQL Server and OLE DB, take this warning seriously and update as soon as possible.
*This post was written exclusively for this request. If you need help patching or verifying your systems, reach out to a qualified IT professional.*
Timeline
Published on: 04/09/2024 17:16:01 UTC
Last modified on: 04/10/2024 13:24:00 UTC