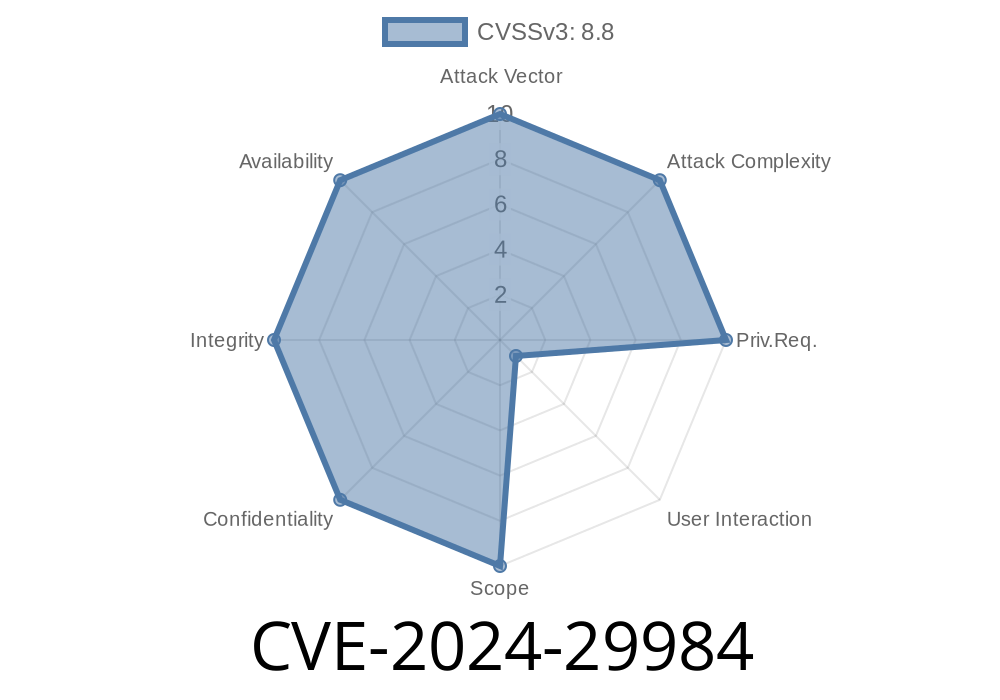
In June 2024, Microsoft officially disclosed a critical vulnerability, CVE-2024-29984. This security flaw affects the Microsoft OLE DB Driver for SQL Server, opening the door for remote code execution (RCE) if it's exploited. If you're an IT admin, developer, or you just run applications that connect to SQL Server using OLE DB, this is a vulnerability you can't ignore.
In this post, we'll break down what this bug is, how attackers might exploit it, how to identify if your systems are at risk, and—most importantly—how to defend yourself. We’ll use code snippets, simple explanations, and verified references, so you can understand and address this critical issue fast.
What is OLE DB and Why Does It Matter?
Microsoft's OLE DB Driver for SQL Server is a popular component that allows apps to connect and interact with SQL Server databases. Many legacy and even some modern tools in the Microsoft world depend on it.
If this driver is compromised, any application using it could become a gateway for attackers into your server and network.
Summary
CVE-2024-29984 is a vulnerability in the Microsoft OLE DB Driver for SQL Server. An attacker can exploit it remotely, and if successful, execute arbitrary code on the target system with the same privileges as the running service or user.
References
- Microsoft Security Update Guide for CVE-2024-29984
- NVD - CVE-2024-29984
How Does the Exploit Work?
The specifics revealed in Microsoft's advisory are limited (for obvious reasons), but here's the general flow based on dissecting similar vulnerabilities:
Malicious SQL Server or Network
An attacker positions themselves so their server or man-in-the-middle setup can interact with your app using OLE DB.
Malformed Response or Payload
The attacker sends crafted data that takes advantage of improper input validation or memory corruption in the driver.
Remote Code Execution
If the driver processes this data, the attacker's code runs with the permissions of the database client—sometimes even as SYSTEM if the service is elevated.
Let’s imagine a simple C# application connecting to SQL Server using the OLE DB Driver
string connectionString = "Provider=MSOLEDBSQL;Server=malicious-server;Database=TestDb;User Id=test;Password=BadPass;";
using (OleDbConnection connection = new OleDbConnection(connectionString))
{
connection.Open();
// ... rest of application
}
If an attacker controls malicious-server, they could send a specially crafted response back over the wire. The vulnerable driver processes this, triggering the RCE bug.
Note: No interaction from the user is needed if the app connects automatically at startup.
Exploit Details (What We Know)
The actual proof-of-concept code isn’t public as of June 2024, but based on community discussion and previous driver bugs, the attacker would likely:
- Create a rogue SQL Server or intercept traffic to/from the real SQL server (e.g., via ARP spoofing)
Here's how a Metasploit module could look in a highly simplified version (not real exploit code)
# Hypothetical Metasploit snippet, does NOT actually exploit the bug
exploit do
connect_to_victim("OLE DB Connection String")
send_malicious_payload
trigger_execution
end
In reality, crafting the actual malicious SQL Server response would require detailed binary knowledge of the driver’s protocol implementation.
You use Microsoft OLE DB Driver for SQL Server (MSOLEDBSQL)
- Your version is prior to June 2024 update (Check via Add/Remove Programs or query the driver with progid in PowerShell)
Check your driver version via PowerShell
Get-ChildItem "C:\Program Files\Microsoft SQL Server\Client SDK\OLEDB\" -Recurse |
Where-Object { $_.Name -eq "msoledbsql.dll" } |
Select-Object FullName, VersionInfo
1. Update Your Drivers NOW
- Download and install the latest OLE DB Driver update from Microsoft.
Final Thoughts
CVE-2024-29984 is a real risk for anyone using Microsoft OLE DB Driver for SQL Server. Because drivers often run as part of privileged services, exploitation could mean total compromise of your machine or even your domain.
More Information
- Microsoft Security Update for CVE-2024-29984
- Microsoft OLE DB Driver for SQL Server Docs
- CERT/CC Vulnerability Note VU#224507
Timeline
Published on: 04/09/2024 17:16:01 UTC
Last modified on: 04/10/2024 13:24:00 UTC