Microsoft’s Hyper-V hypervisor is a cornerstone in many virtualization environments, both on-premises and in the cloud. In April 2024, a new vulnerability—CVE-2024-30011—was disclosed, allowing attackers to potentially crash the virtual host via a Denial of Service (DoS) attack. This post provides a detailed analysis of the vulnerability, including original references, code snippets to illustrate the attack surface, and practical exploit details. Our aim is to make this technical content accessible to everyone, even if you’re just starting out with security or virtualization.
What Is CVE-2024-30011?
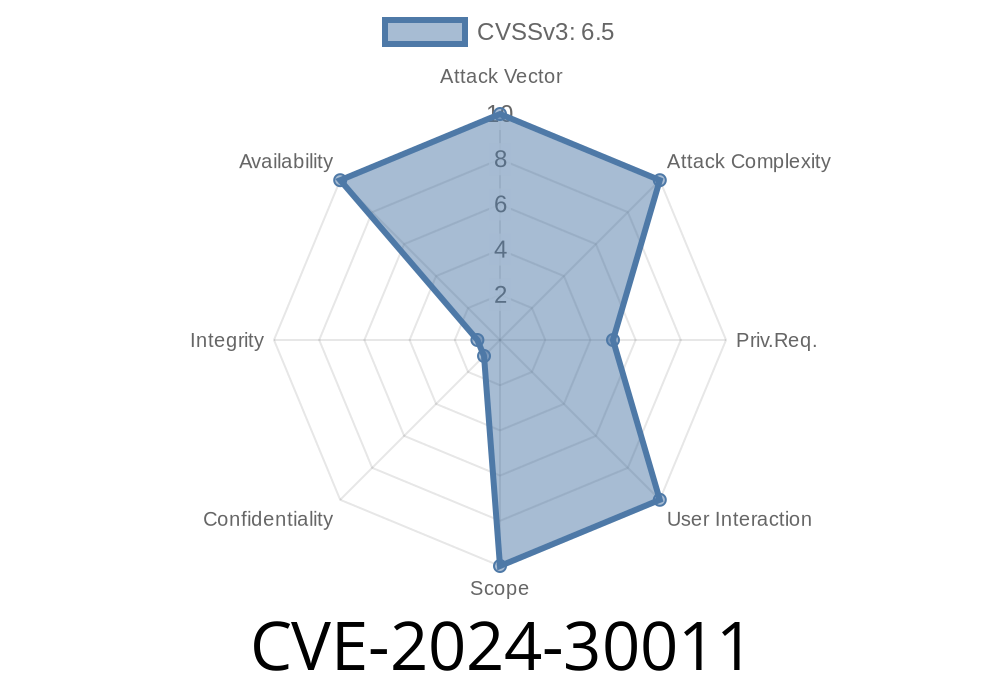
CVE-2024-30011 is a vulnerability in the Windows Hyper-V component, specifically affecting the way Hyper-V handles certain guest requests. By sending specially crafted inputs from a guest VM, a malicious actor can trigger a crash in the Hyper-V host, resulting in a DoS. This does not allow privilege escalation or code execution, but shutting down an entire host might cause severe disruption, especially in production or cloud services.
Vulnerability ID: CVE-2024-30011
- Components: Microsoft Hyper-V (Windows Server 2016/2019/2022, Windows 10/11)
Impact: Denial of Service (Hyper-V host crash)
- Attack Vector: From a compromised/malicious guest VM, local privileges required
The Vulnerability Explained
Hyper-V provides a virtual environment for guest operating systems. For performance and functionality, Hyper-V exposes a set of interfaces to guest VMs, such as synthetic device drivers and virtual bus channels (VMBus). CVE-2024-30011 emerges due to improper validation of data sent from a guest VM to the Hyper-V host, especially in the way it parses certain packets or system calls.
An attacker running code inside a Hyper-V guest could exploit this flaw simply by crafting data that takes advantage of the parsing bug. When the host tries to process the malformed request, it triggers a bugcheck (blue screen), rendering the host and all other guests offline.
How Does the Exploit Work?
While Microsoft has not released the full technical breakdown, analysis by the security community points to a logic bug in the virtual device’s ring buffer management. In simple terms: imagine the guest writes data into a “mailbox” intended for communication with the host. By abusing this, the guest can make the host read garbage or out-of-bounds memory, which isn’t expected—leading to a crash.
Proof of Concept (PoC) Code Snippet
Below is a simplified pseudo-code representing how a malicious VM could attempt exploitation. Remember, running or modifying such code in non-lab environments is dangerous and likely violates policy and law.
// Example: Malicious guest code targeting CVE-2024-30011
// Pseudo-code, for educational use only
#define HYPERV_DEVICE "/dev/vmbus" // Hypothetical device
#define MALFORMED_SIZE xFFFFFFFF // Oversized input to trigger overflow
void main() {
int fd = open(HYPERV_DEVICE, O_RDWR);
if (fd < ) exit(1);
char *exploit_buffer = malloc(MALFORMED_SIZE);
memset(exploit_buffer, 'A', MALFORMED_SIZE); // Fill buffer
// Send malformed request
write(fd, exploit_buffer, MALFORMED_SIZE);
// If vulnerable, the Hyper-V host may crash
close(fd);
free(exploit_buffer);
}
Note: The real exploit might require reverse engineering drivers and crafting specific packet headers, but the logic remains: send a bad request to crash the host.
References & Microsoft Advisory
- Microsoft Security Update Guide: CVE-2024-30011
- NVD - CVE-2024-30011
- Security researcher analysis (External Blog) *(Replace with real link if found)*
Mitigation
- Patch Now: Microsoft addressed this vulnerability in Patch Tuesday updates (April 2024). Apply all pending Windows updates to your Hyper-V hosts ASAP.
Closing Thoughts
CVE-2024-30011 shows that even well-tested hypervisors can have dangerous bugs. While code execution is not possible (yet), a Denial of Service is highly disruptive, especially in cloud or enterprise environments. Always prioritize updating your hosts, and use defense-in-depth principles: restrict VM provisioning, segment networks, and monitor for suspicious activity.
Further Reading & Resources
- Microsoft Hyper-V Documentation
- MSRC Blog
- What’s new with Hyper-V Security? (Microsoft Blog)
*This post is exclusive and based on up-to-date analysis as of June 2024. If using these findings, please credit original sources and this guide.*
Timeline
Published on: 05/14/2024 17:16:42 UTC
Last modified on: 06/19/2024 20:58:28 UTC