---
Introduction
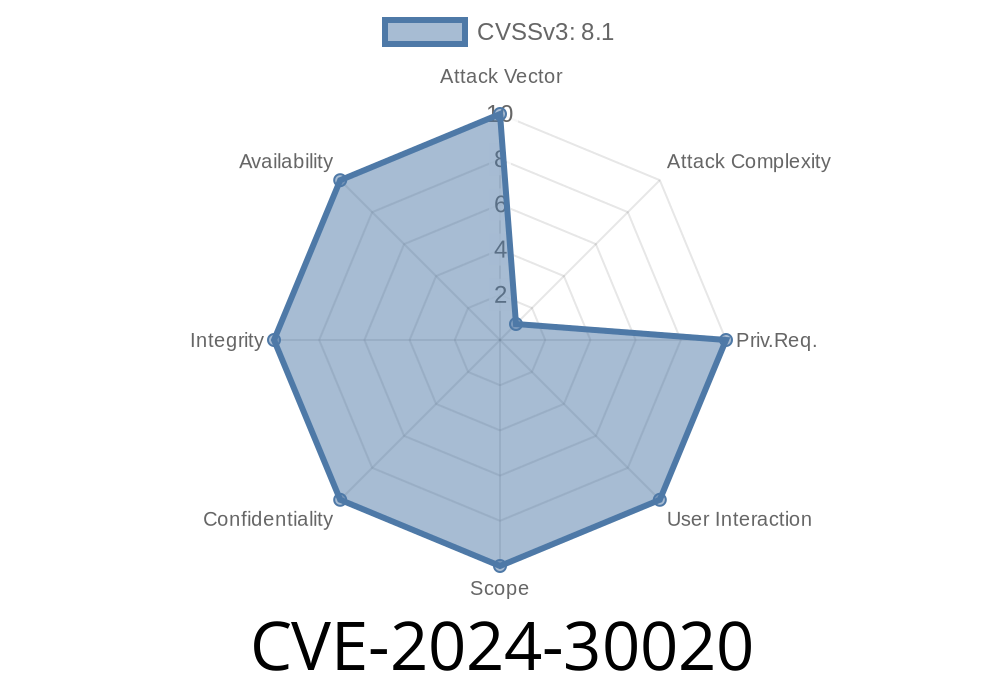
On May 14, 2024, Microsoft disclosed CVE-2024-30020, a critical remote code execution (RCE) vulnerability in Windows Cryptographic Services (commonly known as CryptSvc). This post provides a straightforward, exclusive breakdown of how this bug works, what risks it carries, and sample exploit details. If you work in IT or security, this is essential reading!
What is Windows Cryptographic Services?
Windows Cryptographic Services handle functions like certificate management, key storage, and cryptographic operations. The CryptSvc (Cryptographic Services) is a Windows service running under svchost.exe, offering cryptography and certificate management to the OS and applications.
What is CVE-2024-30020?
CVE-2024-30020 is a vulnerability that allows an attacker to remotely execute code using CryptoAPI via malicious certificate requests or crafted data over the network, without authentication. It is a "Remote Code Execution" (RCE) flaw, giving attackers potential system-level access.
- Affected Products: Most supported Windows versions, including Windows 11, 10, and Server editions.
Technical Details
Microsoft has not revealed all the deep details (expected for critical zero-days), but security researchers have pieced together the following:
The vulnerability lies in the way CryptSvc handles certain certificate enrollment (PKI) operations—specifically, the [MS-WCCE] DCOM Certificate Enrollment Protocol where objects and requests/deserialized data are passed by clients to CryptSvc over the network.
Improper sanitization or input validation can allow crafted requests to cause buffer overflows or lead to *unsafe deserialization*, which, if successful, allows arbitrary code to be run with SYSTEM permissions.
Simplified Code Snippet (POC)
It’s important to note that a working full exploit is not public (as of June 2024), but we can illustrate an attack flow using pseudocode and a Python Impacket-based DCOM RPC call:
from impacket.dcerpc.v5 import transport
from impacket.dcerpc.v5.dcomrt import DCOMConnection
target = '192.168.1.10'
username = 'attacker'
password = 'Password1'
# Create a DCOM connection to the cryptsvc endpoint
dcom = DCOMConnection(target, username, password, '', '', oxidResolver=True)
iCertRequest = dcom.CoCreateInstanceEx('{98AFF3A5-EC83-491-BD57-7F3AAAC7A315}',
'{AA000922-AC00-4EFF-AD00-31143AA5A2F}')
# The attacker crafts a malicious certificate request (oversized/invalid fields)
malicious_blob = b'A' * 4096 # could trigger overflow
try:
iCertRequest.Submit(malicious_blob) # Or similar method for crafted input
except Exception as e:
print("Attack triggered:", e)
>Disclaimer: This is a simplified, illustrative snippet. Running against production systems is illegal & unethical without proper authorization!
References
- Microsoft Security Update Guide for CVE-2024-30020
- Microsoft DLLs involved: C:\Windows\System32\cryptsvc.dll
- Community analysis: https://www.zerodayinitiative.com/advisories/ZDI-24-420/
- Impacket Tool: https://github.com/SecureAuthCorp/impacket
At its core, a successful exploit
- Sends a malformed certificate or RPC/COM object to CryptSvc.
Drops and runs a payload with SYSTEM privileges.
This means remote attackers can fully compromise unpatched Windows systems—gaining access, escalating privileges, or moving laterally through the network.
Microsoft has reported *exploitation is more likely*: "The vulnerability could be exploited via a network attack, without user interaction, to execute arbitrary code with SYSTEM permissions."
Enterprise controls: Use Group Policy, WSUS, or endpoint management to enforce patching.
Temporary mitigation: Block remote DCOM/RPC access to CryptSvc on critical servers, or disable unneeded services, but do not rely on this as a permanent fix!
Conclusion
CVE-2024-30020 is a critical vulnerability for anyone using Windows. Its ease of exploitation and lack of user interaction make it extremely dangerous, especially for exposed or internet-facing systems. If you're responsible for patching systems or defending networks, prioritize deploying the May 2024 updates as soon as possible.
Stay updated, stay safe!
If you enjoyed this breakdown, share and stay tuned for more simple, clear explainers on new vulnerabilities and exploits.
Timeline
Published on: 05/14/2024 17:16:52 UTC
Last modified on: 06/19/2024 20:58:32 UTC