---
On June 2024 Patch Tuesday, Microsoft addressed a critical security issue—CVE-2024-30023—affecting Windows Routing and Remote Access Service (RRAS). This vulnerability enables attackers to execute malicious code remotely on unpatched systems, putting business networks at serious risk. In this exclusive post, let's break down what happened, how exploitation works, and what you can do about it.
What is RRAS?
RRAS (Routing and Remote Access Service) is a Windows service that allows organizations to route network traffic and enable remote client connectivity (such as VPNs). It’s commonly enabled in enterprise and some small business environments for remote work.
What’s CVE-2024-30023?
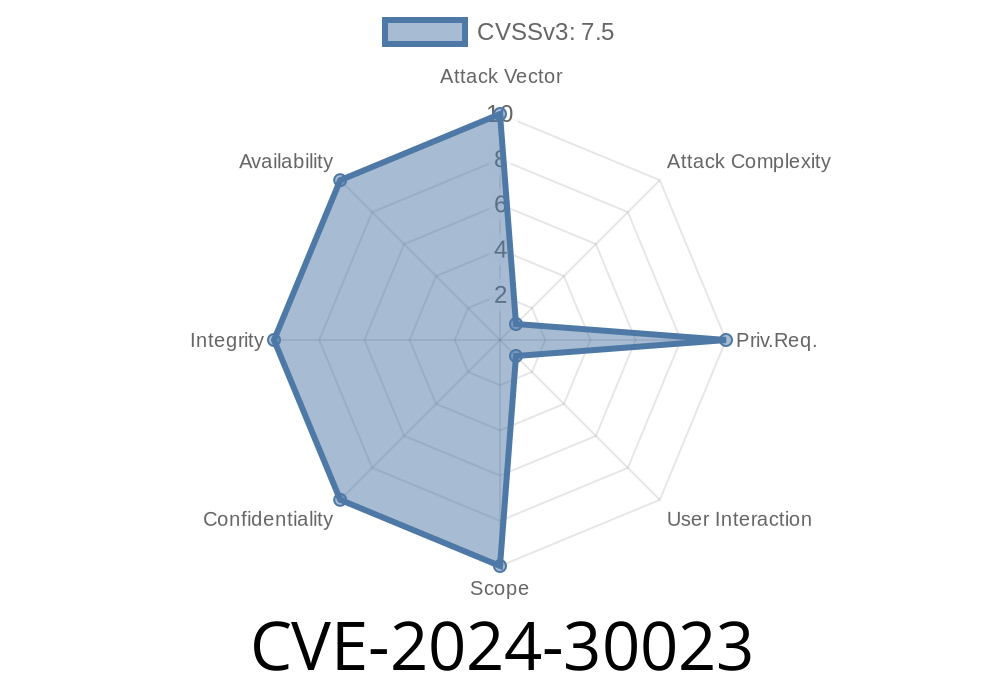
CVE-2024-30023 is a remote code execution (RCE) vulnerability caused by improper handling of specially crafted network packets in RRAS. If exploited, an unauthenticated attacker can run arbitrary code on the affected RRAS server—potentially leading to full system compromise.
User interaction: None
> References:
> - Microsoft Security Update Guide: CVE-2024-30023
> - NVD - CVE-2024-30023
Windows Server 2016, 2019, 2022
- Some supported Windows 10/11 editions with RRAS enabled (less common)
How Does Exploitation Work?
A remote attacker can send specially crafted network packets to the RRAS service. If RRAS is listening on a network (commonly VPN or gateway servers), the attacker doesn’t need valid credentials or user interaction. The crafted packets exploit improper memory handling, similar to buffer overflows or use-after-free bugs.
Sample Exploit Logic
While no *full* exploit has been publicly released (as of June 2024), here’s a *simplified pseudocode* to show how such bugs are commonly triggered:
import socket
# Replace with the RRAS server's IP and port (e.g. PPTP, L2TP, or other RRAS listening port)
target_ip = "192..2.10"
target_port = 1723 # Example for PPTP
# The malicious payload (this would be specific to the actual bug found in RRAS)
payload = b'\x90' * 1024 # Fill with NOPs or the crafted buffer overflow payload
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect((target_ip, target_port))
sock.send(payload) # Sends the payload to crash or control the service
sock.close()
> NOTE:
> The exploit details are abstract due to lack of full public exploit, but many RCE bugs in RRAS historically involve sending malformed VPN (PPTP, L2TP) or routing packets.
Real-World Impact
Attackers can use CVE-2024-30023 to penetrate a target Windows infrastructure, install ransomware, steal data, or move laterally across the network. Since RRAS often runs on the edge, exploiting it can grant immediate access into normally protected environments.
Mitigation & Patch
Microsoft released patches for all supported versions. Patch immediately if you run RRAS or have it installed.
June 2024 Patch Tuesday updates:
Download from Microsoft Update Catalog (example link; check for the specific patch for your OS)
Scan your network for active RRAS services
Get-Service -Name RemoteAccess
Look for listening RRAS ports
# Find open RRAS-related ports
Get-NetTCPConnection | Where-Object { $_.LocalPort -in 1723, 1701, 47, 500, 450 }
Monitor logs for suspicious VPN connection attempts or unusual traffic.
Conclusion
CVE-2024-30023 is one of the most dangerous RCEs in recent history for Windows RRAS. Many businesses rely on RRAS, often without realizing their exposure. Make sure to patch your servers, restrict network access, and review why and where RRAS is running in your environment.
Stay secure—share this information and keep your systems updated!
Further Reading
- Microsoft Security Guide for June 2024
- Rapid7 Analysis on Patch Tuesday, June 2024
- How RCE Works in Windows Services
Timeline
Published on: 05/14/2024 17:16:56 UTC
Last modified on: 06/19/2024 20:58:33 UTC