In 2024, Microsoft disclosed a critical vulnerability affecting Windows Routing and Remote Access Service (RRAS). Catalogued as CVE-2024-30029, this flaw allows attackers to run malicious code remotely on servers running RRAS. Let's break down what this vulnerability is, how it works, its potential impact, and what you can do to protect your systems.
🔍 What is CVE-2024-30029?
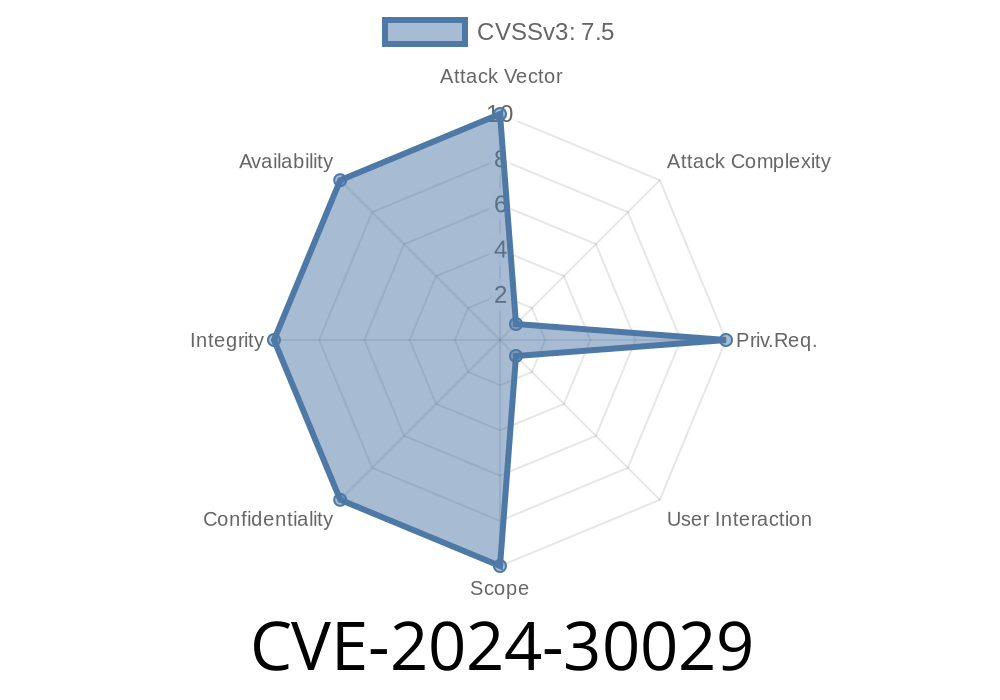
CVE-2024-30029 is a remote code execution (RCE) vulnerability in the Windows RRAS component. RRAS lets Windows Server systems act as network routers, VPN servers, or other networked roles. If left unpatched, malicious actors can exploit this vulnerability to run arbitrary code on a targeted server–effectively taking control.
Vulnerable Service: The flaw is found in how RRAS processes specially crafted packets.
2. Remote Exploitation: An unauthenticated remote attacker can send a malicious network packet to a server with RRAS enabled.
3. Code Execution: If successful, the packet triggers a memory corruption bug, and the attacker can execute any command they want with system privileges.
Visual Flow
graph TD;
Attacker-->|Malicious Packet|RRAS_Server
RRAS_Server-->|Executes code|Attacker
💥 Example Exploit Snippet
While full-blown public exploits may not be out yet, security researchers have demonstrated PoC ("Proof-of-Concept") code that triggers the vulnerability. Here’s a generic Python example that represents how an attacker might start:
import socket
# Target server IP and RRAS listening port (example)
target = "192.168.1.100"
port = 500
# Malicious packet designed to exploit the RRAS vulnerability
payload = b'\x41' * 1024 # example - actual exploit needs crafted payload
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((target, port))
s.send(payload)
print("Payload sent!")
Note: This sample is for educational purposes only and not a working exploit. The actual payload must target the specific memory flaw in RRAS.
Microsoft Security Guidance:
Microsoft CVE-2024-30029 Security Update
Zero Day Initiative ZDI Advisory:
ZDI-24-560: Microsoft Windows RRAS RCE Vulnerability
NIST NVD Database:
📝 Summary Table
| Risk Level | Attacker Prereqs | System Impact | Patch Available? |
|--------------|------------------|------------------|------------------|
| Critical | Network access | Full compromise | Yes, June 2024 |
🚩 Final Thoughts
CVE-2024-30029 is a vivid reminder of the importance of keeping your server software up to date and limiting exposure of network services. The vulnerability is severe because it allows remote attackers to take over a system without authentication or user interaction.
If you run Windows RRAS, patch immediately. If you don’t need RRAS, disable it.
Stay safe, secure those servers, and keep checking the references for updates!
Timeline
Published on: 05/14/2024 17:17:01 UTC
Last modified on: 06/19/2024 20:58:41 UTC