---
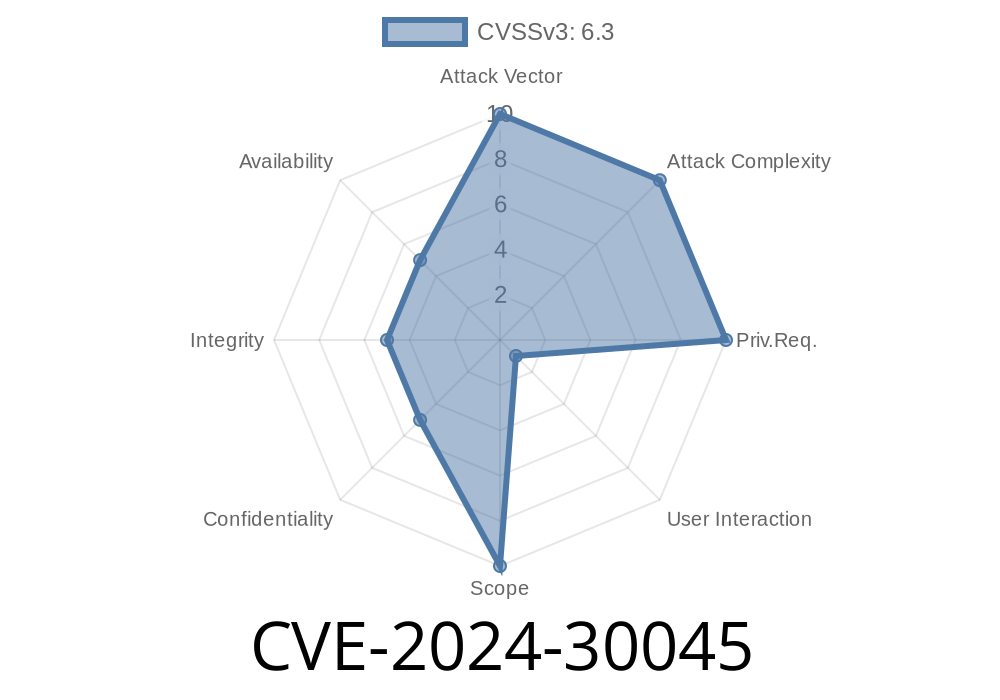
In May 2024, Microsoft patched a significant security flaw tracked as CVE-2024-30045. This vulnerability affects both the .NET framework and Visual Studio, potentially allowing attackers to run arbitrary code on a victim’s computer—remotely. In this post, we’ll break down what CVE-2024-30045 is, how it works, and provide a hands-on look at how it can be exploited.
What is CVE-2024-30045?
CVE-2024-30045 is a remote code execution (RCE) vulnerability in certain versions of the .NET runtime and Visual Studio IDE. It arises from the way Visual Studio handles certain project or file types, enabling attackers to craft malicious files that, when opened or built, can execute code with the current user’s privileges.
This means that attackers can trick developers into opening a poisoned project file, leading to automatic malware execution on their workstations. Given how many companies depend on Visual Studio and .NET, this exposure is a big deal.
Microsoft Advisory:
Microsoft Security Guidance - CVE-2024-30045
How Does the Vulnerability Work?
Visual Studio trusts various project definition files (like .csproj, .vbproj, etc). Parts of these files allow running tools and scripts as part of the build process, called “custom tasks.” If these tasks point to attacker-controlled code or binaries, simply *building* or *loading* a project triggers code execution.
In affected versions, Microsoft did not properly limit or sanitize what these custom tasks could do, making it easier for attackers to sneak in their payloads inside innocent-looking Visual Studio projects.
Let’s walk through a practical attack scenario
1. Attacker crafts a malicious Visual Studio project with a custom build task that executes arbitrary code (for example, a reverse shell or malware installer).
The developer opens or builds the project in Visual Studio.
4. During build/load, the malicious task executes, compromising the developer's PC.
Example of an Exploit in a .csproj File
Below is a stripped-down sample which, when loaded in affected Visual Studio versions, runs the Windows Calculator (calc.exe). Malicious actors can replace calc.exe with any code they want:
<Project Sdk="Microsoft.NET.Sdk">
<PropertyGroup>
<TargetFramework>net8.</TargetFramework>
</PropertyGroup>
<Target Name="Exploit" AfterTargets="Build">
<Exec Command="cmd.exe /c calc.exe" />
</Target>
</Project>
How it works:
- The <Target> element defines an action that runs *after* the project builds (AfterTargets="Build").
- <Exec Command="cmd.exe /c calc.exe" /> triggers the payload.
Visual Studio’s default trust model would just run this without warning in vulnerable versions.
For a silent, real-world attack, this line could be an obfuscated PowerShell payload, ransomware dropper, or credential stealer.
Proof-of-Concept (PoC) Steps
> Warning: Don’t test this on a production system.
Mitigation and Fix
Microsoft released updates for .NET and Visual Studio to patch this bug (see references below). If you haven't already:
- Update Visual Studio and your .NET SDK/runtimes to the latest version.
Use virus scanners and endpoint protection on your developer machines.
> Official Microsoft patch downloads:
> - .NET May 2024 Security Updates
> - Visual Studio Release Notes
References
- Microsoft CVE-2024-30045 Security Advisory
- Analysis by Tenable
- Redmondmag write-up
- .NET Blog - May 2024 Security
Final Thoughts
CVE-2024-30045 is a real-world reminder that even development tools can harbor severe vulnerabilities, especially when they trust user-supplied content. Always be cautious with project files, update regularly, and teach your team about supply-chain and IDE-based threats. Happy (and safe) coding!
Timeline
Published on: 05/14/2024 17:17:17 UTC
Last modified on: 06/19/2024 20:58:48 UTC