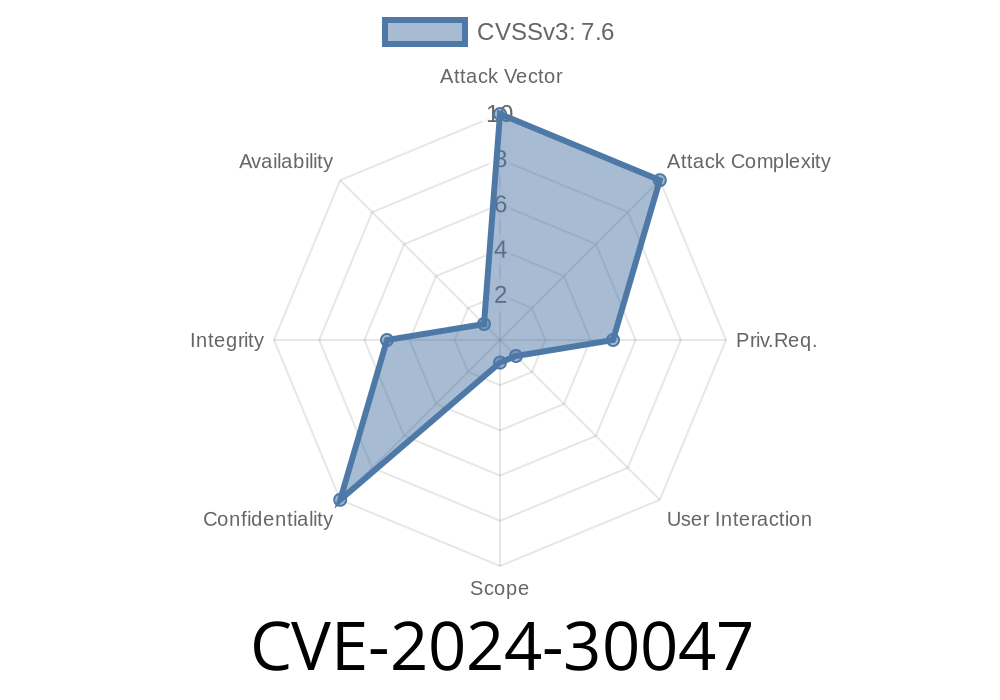
Microsoft Dynamics 365 Customer Insights lets businesses collect and analyze customer data from diverse sources, empowering smarter decisions. But in 2024, a vulnerability was found that could let attackers pose as others within the system. This is CVE-2024-30047, a critical spoofing vulnerability with potentially serious implications.
Let’s break down what happened, how it works, and what you can do about it.
What is CVE-2024-30047?
CVE-2024-30047 is a spoofing vulnerability disclosed by Microsoft on June 11, 2024 (original advisory). In short, an attacker could trick Dynamics 365 Customer Insights into believing their actions come from a trusted or legitimate user.
Triggering actions as another user
It’s not a remote code execution or data exfiltration bug by itself, but it can still have a major impact in the wrong hands.
You haven’t applied the June 2024 security updates
Check Microsoft’s official affected products list to see specific builds.
How the Exploit Works
Microsoft’s advisory is light on details—for security reasons—but here’s what’s publicly known, combined with analysis from security researchers:
1. The Spoofing Vector
The vulnerability lies in how user authentication tokens are handled during certain Customer Insights operations. If an attacker gains a way to tamper with the web requests (for example, with tools like Burp Suite or mitmproxy), they can inject a forged authentication token into the request headers.
Here’s a simple pseudocode to demonstrate the logic
import requests
# Attacker's session - but wants to pose as an admin user
admin_jwt_token = "eyJhbGciOi...FAKE...3js"
# Craft a request representing an admin action
headers = {
'Authorization': f'Bearer {admin_jwt_token}',
'Content-Type': 'application/json'
}
data = {
"action": "access_sensitive_customer_data"
}
url = "https://your-company.crm.dynamics.com/api/data/v9.2/customerinsights/action";
response = requests.post(url, headers=headers, json=data)
print(response.status_code)
print(response.json())
If the back-end improperly trusts the token, the exploit works—the attacker does something only an admin could.
Note: A real attack would have to obtain or forge a valid admin token. Sometimes, related vulnerabilities or misconfigurations leak tokens or session data.
Unexpected activity from low-privilege accounts
- Audit logs showing actions from accounts at strange dates/times
If you log incoming JWT claims or headers, review for anomalies.
Update your Customer Insights service ASAP.
- Minimal patch information is here on the official CVE page.
Defense-in-depth:
- Enforce strict validation on JWT/auth tokens
Limit privileges by default
- Enable detailed auditing/logging
- Educate admins about phishing/social engineering that could lead to token theft
Reference Links
- Microsoft Security Response Center: CVE-2024-30047
- Dynamics 365 Customer Insights Official Docs
- OWASP: Authentication and Session Management
Conclusion
CVE-2024-30047 is a reminder: business-critical SaaS is an attractive target for attackers. The boundary between trusted and untrusted actions is only as strong as your authentication system. If you use Dynamics 365 Customer Insights, patch immediately and review your authentication logs for any unusual activity.
Timeline
Published on: 05/14/2024 17:17:18 UTC
Last modified on: 06/19/2024 20:58:49 UTC