Published: June 2024
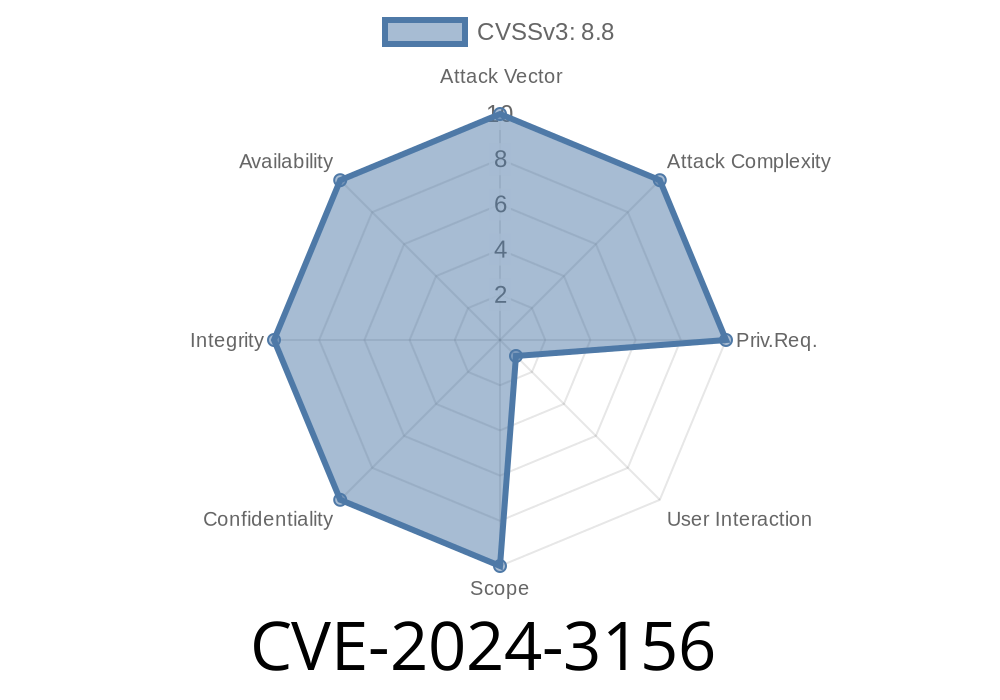
Severity: High
Component: V8 JavaScript Engine in Chromium
Introduction
In early 2024, Google disclosed CVE-2024-3156, a high-severity vulnerability in the V8 JavaScript engine, which powers Chrome’s JavaScript processing. Attackers could use a specially-crafted HTML page to perform out-of-bounds memory access. This issue put millions of Chrome users at significant risk up until version 123..6312.105. Let's dig into how this bug works, why it happened, and how attackers could exploit it.
What is V8 and Why Is It Critical?
V8 is Google’s open-source JavaScript engine, crucial to Chrome’s speed and modern features. However, it’s complex, especially due to its *Just-In-Time (JIT)* compiler which turns JavaScript code into fast machine code. This complexity can sometimes lead to flaws where code gets too close to or outside of memory boundaries—a classic bug vector for exploits.
The Official Description
> "Inappropriate implementation in V8 in Google Chrome prior to 123..6312.105 allowed a remote attacker to potentially perform out of bounds memory access via a crafted HTML page. (Chromium security severity: High)"
Full Details:
- Chromium Issue Tracker *(May require sign-in or have restricted access)*
- Official Security Advisory
What Does This Mean?
An attacker could get JavaScript running in Chrome to read from (or write to) memory locations it shouldn’t be able to access. That opens the door to:
The Heart of the Flaw
The bug arises from V8 not correctly checking the bounds of an array during certain custom object manipulations. With precise JavaScript code, the attacker tricks V8 into believing an array is bigger than it is. This makes corrupt memory—or *arbitrary* memory access—possible.
Example Exploit (Simplified for Education)
// Array to be corrupted
let arr = [1.1, 2.2, 3.3, 4.4];
// TypedArray for memory primitives
let victim = new Float64Array(8);
// Handcrafted object to trigger the bug
function trigger() {
// This block abuses V8's optimization and array handling bugs
for (let i = ; i < 1e4; ++i) {
// Some code patterns trigger JIT, which exposes the hidden bug
arr.length = (i === 1e3) ? 1e6 : 4;
}
// If exploit is successful, arr can now access memory outside its bounds
victim[10] = 1337.7; // Unsafe write outside intended array
}
// Run the attack
trigger();
console.log(arr[100000]); // Memory leak: may access unintended memory
Warning: This is a *demonstration* of the logic; the real exploit would be more complex and version-dependent. It does, however, show the basic progression: *abuse array length changes to confuse the engine's memory logic.*
Real-World Impact
- Drive-by attacks: Visiting a compromised or malicious website could infect your browser *without any warnings*.
Fixed!
The Chrome team patched this bug in version 123..6312.105.
How to Stay Safe
- Update immediately: If you haven’t already, make sure your Chrome is at least this version or newer.
Learn More and References
- Official Chrome Release Announcement
- Chromium Security Advisories
- V8 JavaScript Engine Homepage
- CVE-2024-3156 at NIST
Final Thoughts
CVE-2024-3156 highlights how complex browser engines can create unforeseen security holes—and how even simple-looking JavaScript can be weaponized by attackers. Always keep your browser updated and be wary of suspicious websites. Security is a moving target, and today’s defenses rely on *quick updates*.
Timeline
Published on: 04/06/2024 15:15:26 UTC
Last modified on: 04/26/2024 16:00:34 UTC