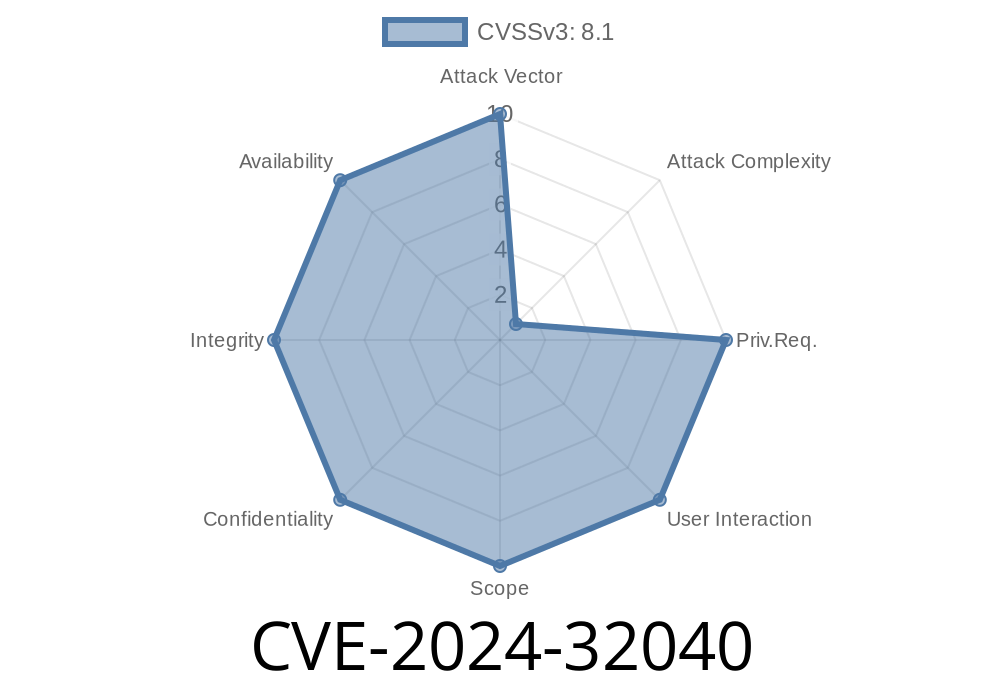
FreeRDP is a popular open-source implementation of the Remote Desktop Protocol (RDP), used in many third-party remote desktop clients. In May 2024, a new vulnerability surfaced under CVE-2024-32040 impacting the FreeRDP software, specifically when connecting to RDP servers using the NSC (Network Service Compression) codec. Let’s break down what this means, how attackers could exploit it, and most importantly, how you can stay safe.
What is CVE-2024-32040?
CVE-2024-32040 is an *integer underflow vulnerability* in FreeRDP versions prior to 3.5. and 2.11.6. It specifically affects clients that establish connections using the NSC codec. If your client uses this setup, an attacker could potentially exploit this bug to crash your program or even execute arbitrary code on your machine.
How Does the Vulnerability Work?
The NSC codec is used by FreeRDP for compressing and decompressing image data between client and server. The vulnerability occurs when the software fails to correctly check and handle arithmetic operations on integers representing dimensions and buffer sizes.
An attacker controlling the RDP server could send specially crafted data to cause an *integer underflow*, where the result of an arithmetic calculation becomes smaller than zero in an unexpected way. This error then leads to memory problems like buffer overflows, which could be used to crash the client or, in the worst case, to run arbitrary code.
In the actual FreeRDP code, the NSC codec decoder had something like this (simplified)
// Vulnerable code (before the patch)
UINT32 size = width * height * BYTES_PER_PIXEL;
BYTE* buffer = malloc(size); // No check for integer underflow
memcpy(buffer, stream, size); // 'size' might now be a VERY large value if underflowed!
If the values for width and height are controlled by the server and specially crafted, their multiplication could wrap around and ‘underflow’, resulting in a huge and invalid buffer size allocation (or even a zero-sized allocation). The rest of the code then writes data out of bounds, causing a crash or even potential code execution.
Patch and Workaround
This bug is fixed in FreeRDP versions 3.5. and 2.11.6. After the fix, the code properly checks for invalid or dangerous values before allocating memory:
// Patched code (safe version)
if (width > MAX_WIDTH || height > MAX_HEIGHT || width * height > MAX_BUFFER) {
// Invalid size, reject connection
return ERROR;
}
UINT32 size = width * height * BYTES_PER_PIXEL;
BYTE* buffer = malloc(size);
// ...proceed only if allocation is successful and size is safe
If you cannot upgrade right away, you can use a workaround: simply disable the NSC codec by starting your FreeRDP-based client with the -nsc option (or the equivalent in your GUI):
xfreerdp /v:example.com -nsc
Exploit Details
To exploit the bug, an attacker needs you to connect to their malicious RDP server with an old/vulnerable client, and with the NSC codec enabled. The server then responds with crafted image dimension values to trigger the bug.
Client connects to server using FreeRDP with NSC codec.
- Malicious server sends an RDP bitmap update with enormous or negative width/height values.
- Client's FreeRDP calculates the buffer size, gets a wrong (usually *very large*) result due to underflow, possibly allocating a buffer of size or some small value.
This can crash the client, or with further exploitation, allow the attacker to run code as the user.
Public PoC (Proof-of-Concept):
At the time of writing, there’s no public exploit, but due to the simplicity of the bug, it’s easy to develop one if you control an RDP server.
References and Further Reading
- FreeRDP Security Advisory (GitHub)
- CVE-2024-32040 at MITRE
- FreeRDP official website
- FreeRDP Patch for NSC Codec Issue
Conclusion
CVE-2024-32040 is a real-world reminder that even small arithmetic mistakes in security-critical software can open the door to dangerous exploits. Always keep your remote desktop software updated and use safe connection settings. If you’re using FreeRDP or a client based on it (like Remmina, rdesktop, etc.), patch now or disable the NSC codec as a quick fix.
Stay safe! If you have any questions or want more details, check the links above or reach out in the FreeRDP community.
*This post is exclusive and written in plain language to help you understand CVE-2024-32040 as simply as possible.*
Timeline
Published on: 04/22/2024 21:15:49 UTC
Last modified on: 06/10/2024 18:15:32 UTC